Lacework Console - Agentless Workload Scanning
View Agentless Workload Scanning Results
Once you have integrated Agentless Workload Scanning with your cloud provider, you can view the results of Host and Container scans.
Agentless Host Vulnerability
- Click Vulnerabilities > Hosts to view host vulnerabilities in your environment.
- Apply the Scanner type: Agentless filter (when Group by Host is active) to view host scan results from Agentless Workload Scanning integrations.
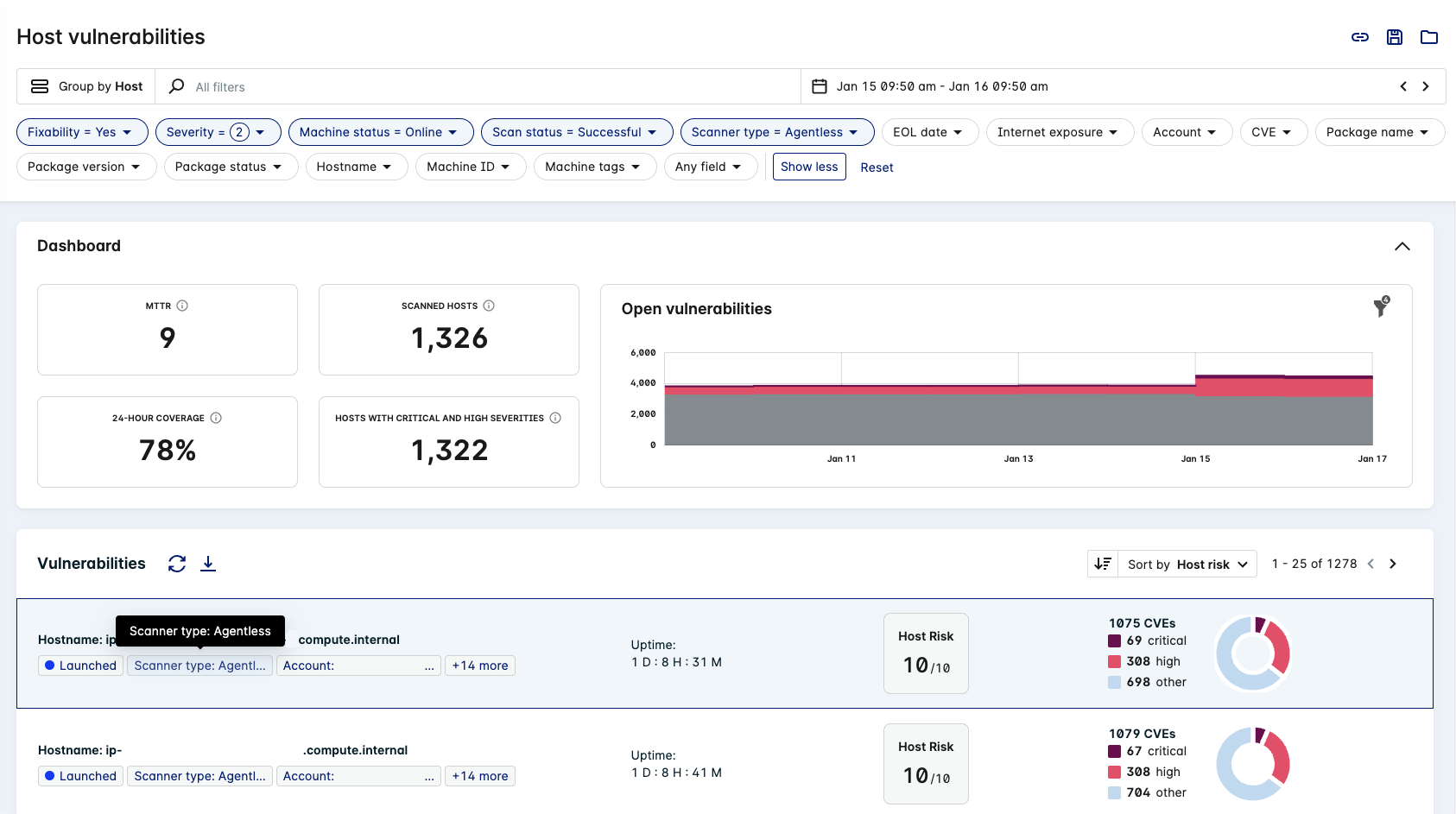
The Scanner type value is Agentless for any host that has been assessed using this type of integration.
Agentless Container Vulnerability
- Click Vulnerabilities > Containers to view container vulnerabilities in your environment.
- Apply the Scanner type: Agentless filter (when Group by Image ID is active in either tab) to view image scan results from Agentless Workload Scanning integrations.
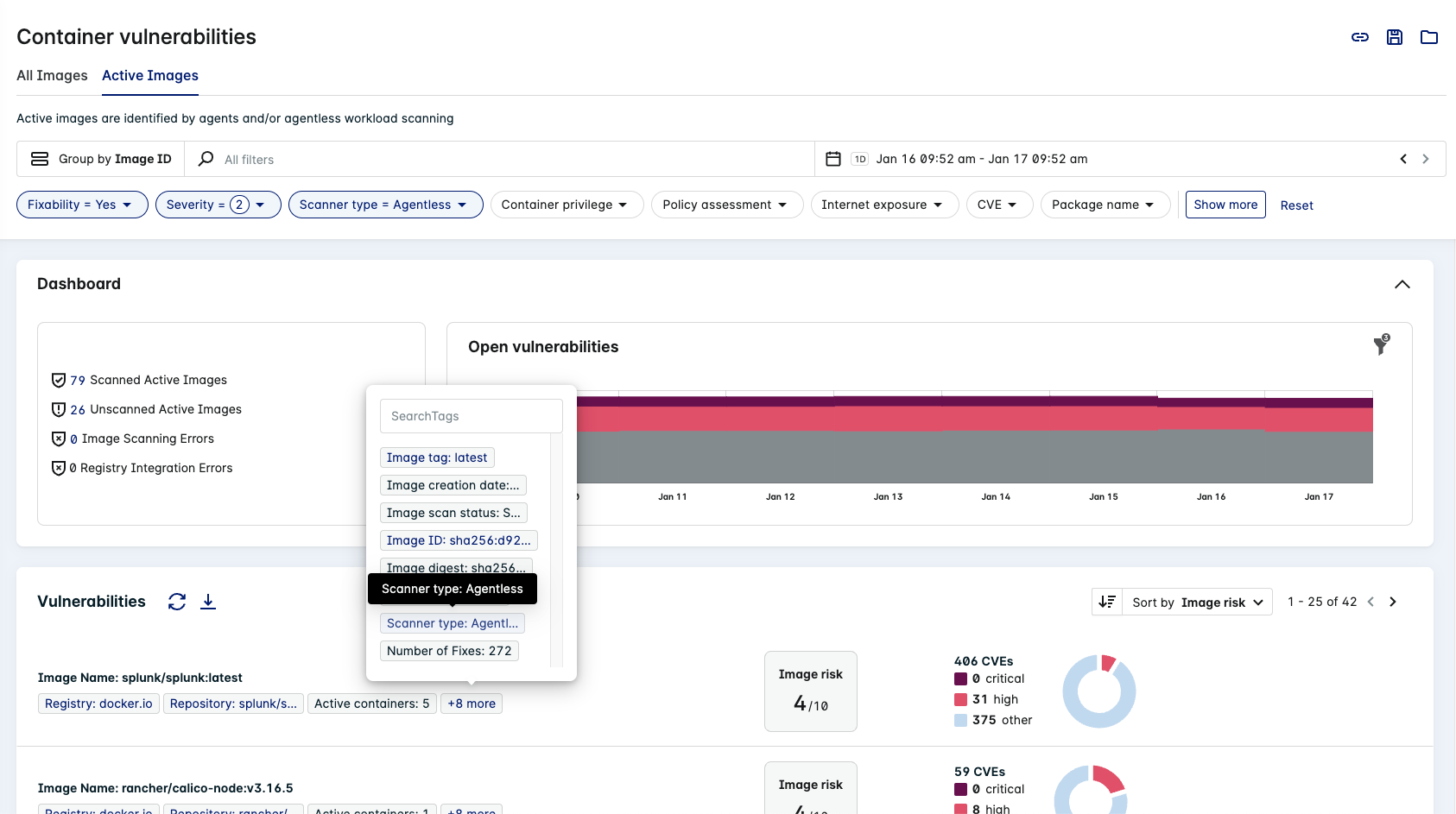
The Scanner type value is Agentless for any image that has been assessed using this type of integration.
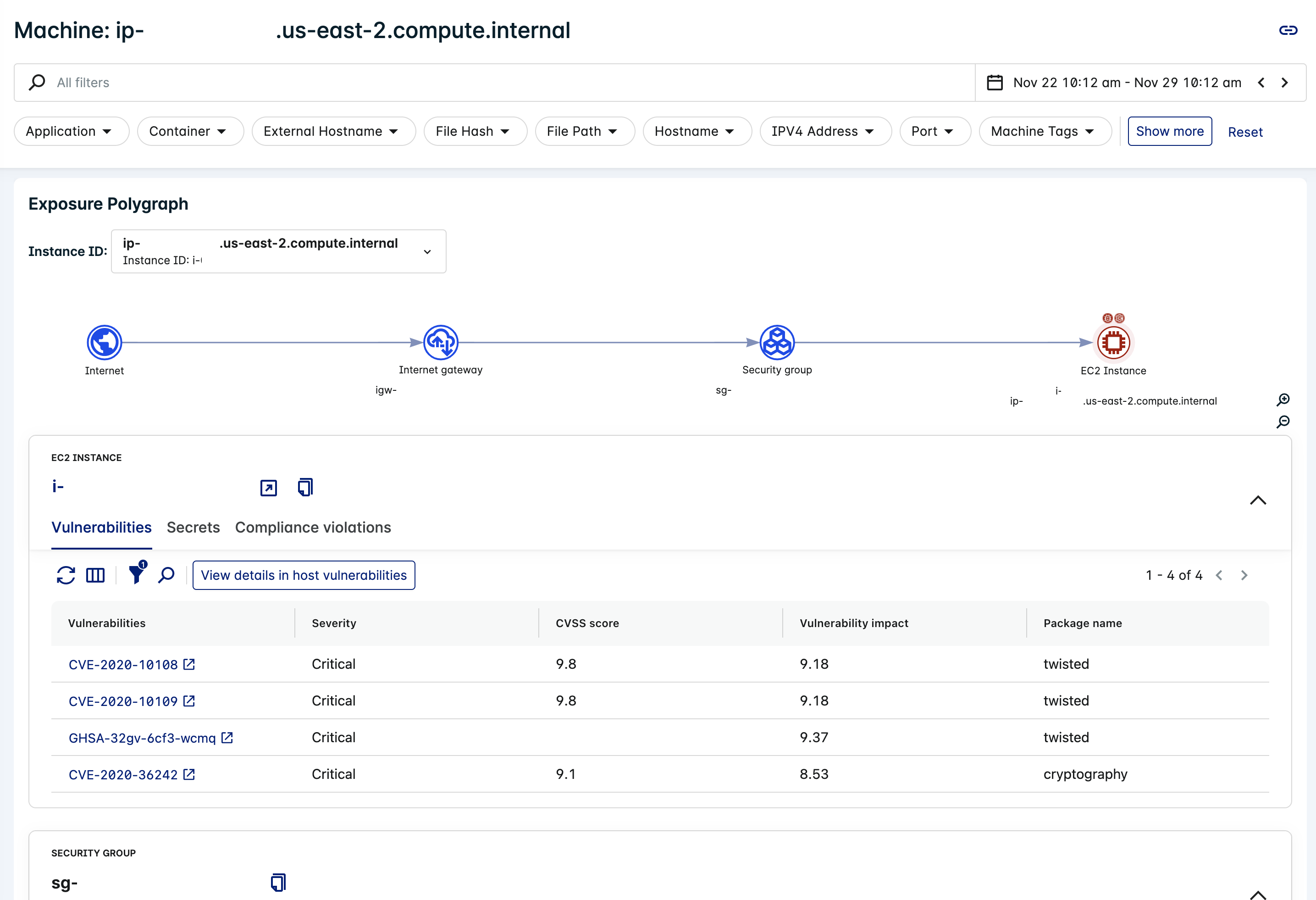
View Exposure Polygraph in Single Machine Dossier
- Click Resources > Host > Machines to view the Machines dossier.
- Click on a Hostname (for example, in the Machine properties or Machine activity table) to view the Single Machine Dossier for that host.
- Find the Exposure Polygraph section to view exposure details from the latest Agentless scan.
Manage your Integration in the Lacework Console
View your Agentless Workload Integrations by navigating to Settings > Integrations > Cloud accounts.
tip
Enter Agentless in the search bar to look for Agentless Workload Scanning integrations.
View Integration Details in the Lacework Console
Select an Agentless Workload Scanning integration in the Cloud accounts table to view its details. The details vary depending on the cloud provider.
note
The majority of the non-editable fields are automatically populated after completing the integration.
AWS
| Title | Description | Example |
|---|---|---|
| Title | The name for the integration (as it will be displayed in the Lacework Console). | myAWSAgentlessIntegration |
| Account | The AWS Account ID for this integration. | 123456789012 |
| Provider | The Cloud Provider for the integration. | AWS |
| Type | AWS Integration Type | Agentless (Single account) or Agentless (Organization) |
| ID | The Lacework generated ID for the integration | MYACCOUNT_123ABC... |
| External ID | The AWS External ID for the integrated AWS account. | 1A2B3C4D5 |
| Role ARN | The AWS Role ARN created for the Agentless Workload Scanning integration. | arn:aws:iam::account:role/role-name-with-path |
| Management Account (Organization integrations only) | The ID of your AWS organization management account. | 123456789012 |
| Monitored Accounts (Organization integrations only) | The IDs of the Root, Organizational Unit(s), and/or accounts in your AWS organization on which agentless workload scanning will be run. | 123456789012 |
| Scanning Account (Organization integrations only) | The ID of the AWS account that was configured to scan your AWS organization during the agentless workload scanning integration. | 123456789012 |
| Bucket ARN | The S3 bucket ARN created for the Agentless Workload Scanning integration. | arn:aws:s3:::bucket_name/key_name |
| Limit Scanned Workloads | The LQL key and value to constrain the Agentless Workload Scanning to specific resources. If it is blank, Lacework will scan all resources available to the account or organization. See Limit Scanned Workloads for further guidance. | |
| Scan Frequency (hours) | How often your containers and hosts are scanned for vulnerabilities (in hours). | 24 |
| Scan containers | Whether your containers will be scanned for vulnerabilities. | true |
| Scan host vulnerabilities | Whether your hosts will be scanned for vulnerabilities. | true |
| Authorization Token | The Lacework authorization token for the integration. | _123456789abcdef123456789abcd |
| credentials.json | Click to download the Lacework authorization token for the integration in JSON format. | N/A |
| Updated | Displays the last time the integration was updated. | 5/25/2022 12:36 PM (PST) |
| Updated by | Displays the user that last updated the integration. | myemail@address |
| Status | The current status of the integration. | Success Pending Error |
AWS - Limit Scanned Workloads
If this field is left blank, Agentless Workload Scanning will scan all EC2 instances and their volumes in the integrated regions.
Using an LQL query, you can "target" specific instances and volumes rather than all available resources.
The LQL query must return the following:
- A single key/value.
- The key can be anything.
- A workload identifier (such as an EC2 instance ID) as the value.
- Any filter can be used as long as it returns a workload identifier.
The following is an example LQL query:
{ source { LW_HE_MACHINES m } filter { m.TAGS:VpcId = 'vpc-0d75bdd9f82d71669' } return { m.TAGS:InstanceId::STRING as InstanceId }}As per the example, the following will also apply to your query:
- The
returnclause in the query statement must return a single key value pair. Note that the result of running this query will return a list of these key value pairs, for example if you have many instances in this VPC. - On line 9, the returned value is an
InstanceId. - The name of the returned pair
InstanceIdis customizable, provide a name of your choice.
GCP
info
GCP support for Agentless Workload Scanning is in Preview.
| Title | Description | Example |
|---|---|---|
| Title | The name for the integration (as it will be displayed in the Lacework Console). | myGCPAgentlessIntegration |
| Account | The GCP Organization or Project ID that has been integrated with Agentless Workload Scanning. | mygcpproject |
| Provider | The Cloud Provider for the integration. | GCP |
| Type | GCP Integration Type | Agentless |
| ID | The Lacework generated ID for the integration. | MYACCOUNT_123ABC... |
| Client ID | The GCP Client ID of the service account used for the integration. | 112233... |
| Private Key ID | The Private Key ID of the service account used for the integration. | abc123... |
| Client Email | The GCP Client Email of the service account used for the integration. | serviceaccount@project.iam.gserviceaccount.com |
| Private Key | The Private Key of the service account used for the integration. | ***** |
| Token URI | The Token URI of the service account used for the integration. | https://oauth2.googleapis.com/token |
| Integration Level | The GCP integration level (project or organization). | PROJECT |
| Scanning Project | The GCP project where the Agentless scanning resources are deployed. | mygcpproject |
| Shared Bucket | The GCP bucket used for the Agentless Workload Scanning integration. | mygcpbucketname |
| Limit Projects | Only relevant to Organization integrations. A list of comma-delimited GCP projects that will be scanned. If left blank, all projects in the organization will be scanned. | myscannedproject1, myscannedproject2 |
| Limit Scanned Workloads | The LQL key and value to constrain the Agentless Workload Scanning to specific resources. If it is blank, Lacework will scan all resources available to the account or organization. See Limit Scanned Workloads for further guidance. | |
| Scan Frequency (hours) | How often your containers and hosts are scanned for vulnerabilities (in hours). | 24 |
| Scan containers | Whether your containers will be scanned for vulnerabilities. | true |
| Scan host vulnerabilities | Whether your hosts will be scanned for vulnerabilities. | true |
| Authorization Token | The Lacework authorization token for the integration. | _123456789abcdef123456789abcd |
| credentials.json | Click to download the Lacework authorization token for the integration in JSON format. | N/A |
| Updated | Displays the last time the integration was updated. | 5/25/2022 12:36 PM (PST) |
| Updated by | Displays the user that last updated the integration. | myemail@address |
| Status | The current status of the integration. | Success Pending Error |
GCP - Limit Scanned Workloads
If this field is left blank, Agentless Workload Scanning will scan all virtual machines and their volumes in the integrated regions.
Using an LQL query, you can "target" specific instances and volumes rather than all available resources.
The LQL query must return the following:
- A single key/value.
- The key can be anything.
- A workload identifier (such as a virtual machine ID) as the value.
- Any filter can be used as long as it returns a workload identifier.
The following is an example LQL query:
{ source { LW_HE_MACHINES m } filter { m.TAGS:network = 'https://www.googleapis.com/compute/v1/projects/myproject/global/networks/default' } return { m.TAGS:name::STRING as name }}As per the example, the following will also apply to your query:
- The
returnclause in the query statement must return a single key value pair. Note that the result of running this query will return a list of these key value pairs, for example if you have many VMs in this VPC. - On line 9, the returned value is a
name. - The name of the returned pair
nameis customizable, provide a name of your choice.
Enable or Disable an Integration in the Lacework Console
Go to Settings > Integrations: Cloud accounts.
Find and select your integration in the table.
Click the Enable/Disable button
to enable or disable the integration.
This can also be done when viewing the Cloud accounts table and clicking the Enable/Disable button in the State column for the integration.
Edit your Integration in the Lacework Console
Go to Settings > Integrations: Cloud accounts.
Find and select your integration in the table.
Click the Edit button
to start editing the integration settings.
The settings vary depending on the Cloud Provider:
Delete your Integration in the Lacework Console
- Go to Settings > Integrations: Cloud accounts.
- Find and select your integration in the table.
- Click the Delete icon
to delete the integration.