Lacework Console - Container Vulnerability
View Vulnerabilities
The container vulnerability page contains open vulnerabilities and previous vulnerabilities that were fixed. To navigate to this page, select Vulnerabilities > Containers in the Lacework Console.
note
Lacework only reports on a container image if it has permission to access the image.
Tabs
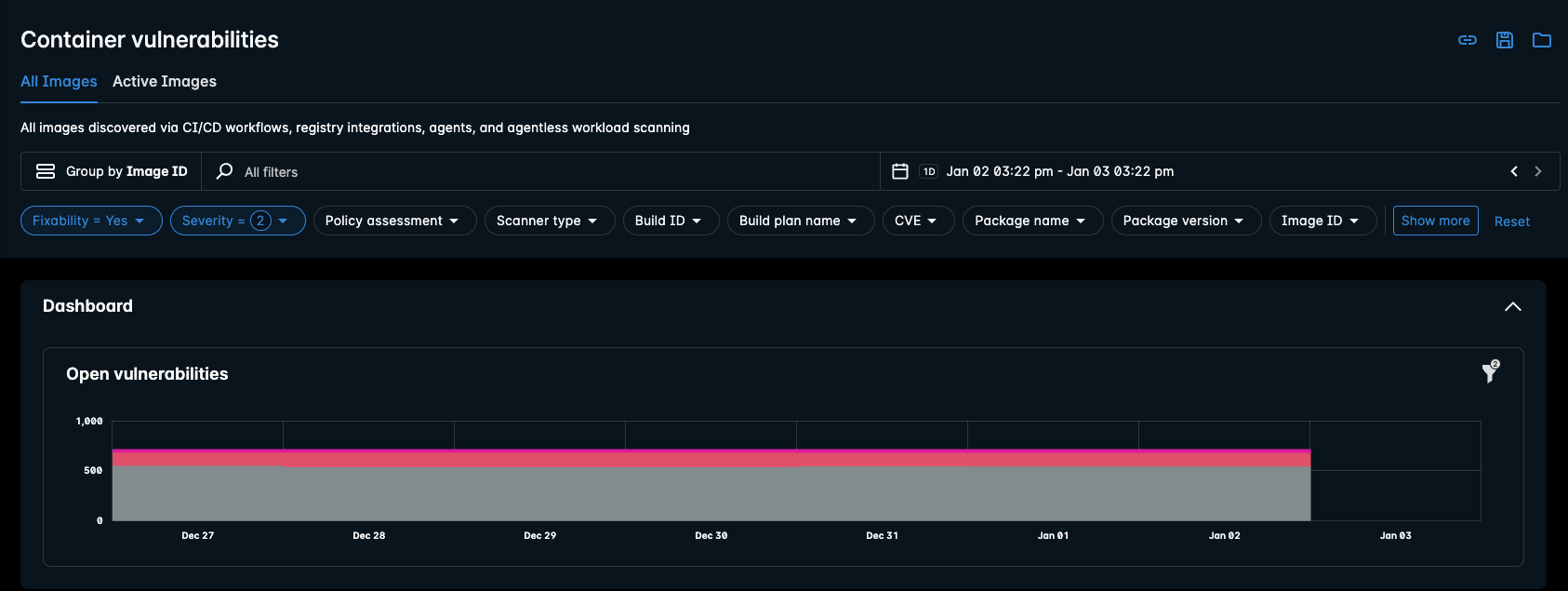
All Images
The All Images tab displays images and vulnerabilities that have been found through CI/CD workflows (for example: Kubernetes Admission Controller), registry integrations, agents and Agentless Workload Scanning integrations.
Active Images
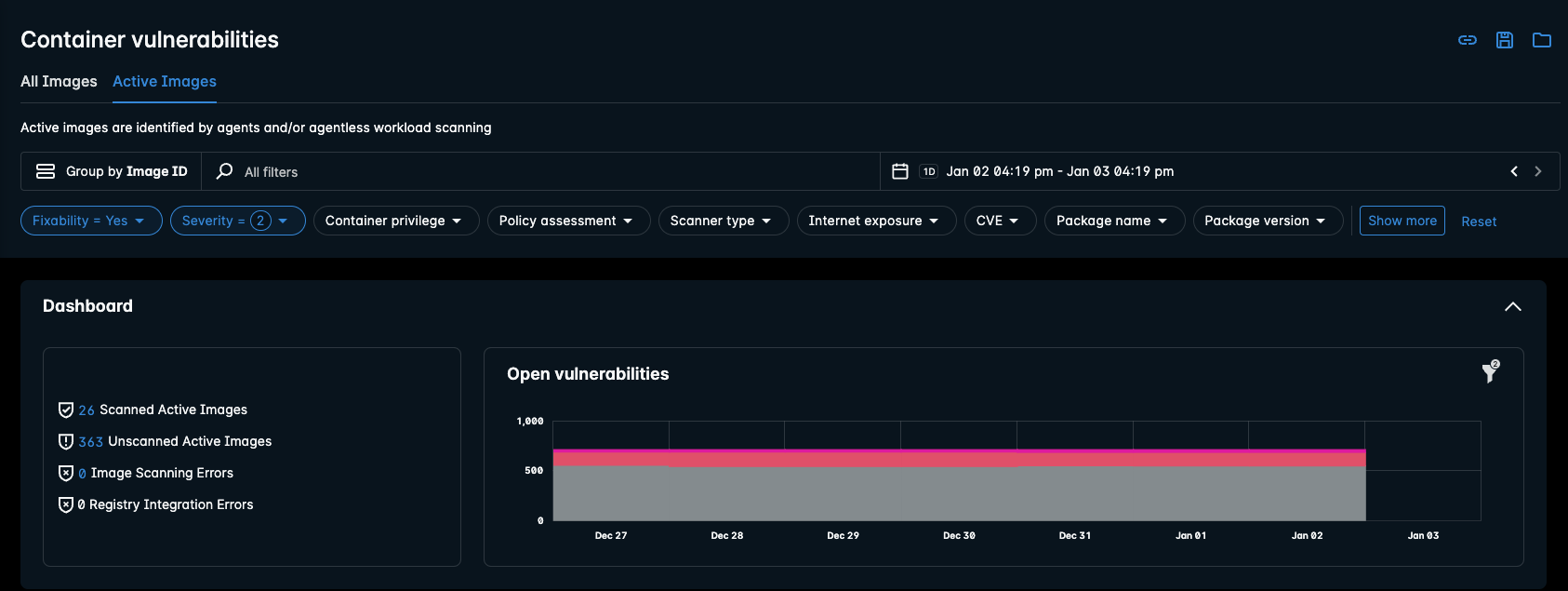
The Active Images tab displays images and vulnerabilities that are found on active containers.
note
Containers can only be identified as Active within container registries that have been integrated with Lacework.
Statistics / KPIs
When the Active Images tab is selected, statistics are shown that display the following data:
| Statistic/KPI | Description |
|---|---|
| Scanned Active Images | Displays the number of images that are actively being used by containers. Active image data is persisted by Lacework during daily re-evaluations, and reports show when an assessment was last run on an image. |
| Unscanned Active Images | Displays the number of images that are actively being used by containers, but have not been scanned by Lacework. Active image data is persisted by Lacework during daily re-evaluations, and reports show when an assessment was last run on an image. |
| Image Scanning Errors | Displays the number of errors that have occurred during scans of images in integrated repositories. |
| Registry Integration Errors | Displays the number of errors seen when Lacework has tried to integrate with a container registry. |
tip
Click on any of these statistics (except Registry Integration Errors) to view the Container Image Information in the Containers Dossier.
Hover over the filter icon to see the active filters that are influencing the statistics.
Groups
By default, the list displays vulnerabilities that are grouped by image registry. To change how the list groups vulnerabilities, select a different grouping option from the Group by drop-down:
- Image ID
- Image Registry
- Image Repo
- CVE
- Package Name
- Package Namespace
Search
Use the search function at the top of the page to find specific text in any of the details available on the page. You can also click the search field to select values and operators to filter your search (these vary depending on the Group by option).
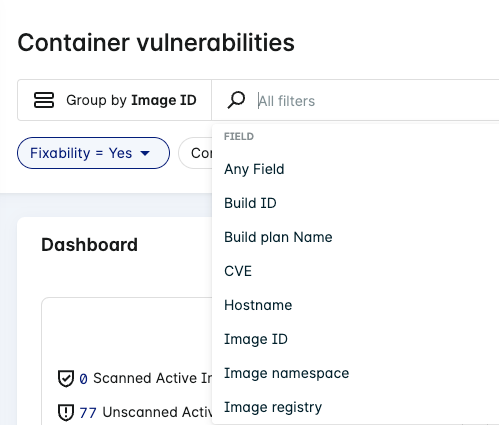
Click a field from the search dropdown to apply an operator that helps refine your search (these vary depending on the type of filter).
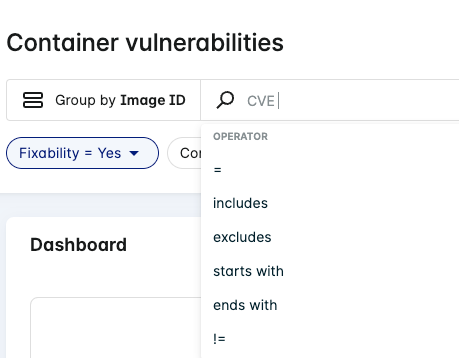
For example, when Group by Image ID is active, search for all container images affected by a CVE matching CVE-2016-3709:

Filters
By default, the page is grouped by Image ID on the Active Images tab and the following filters are active:
When switching to All Images, the following filters are active by default:
You can use the following methods to refine the list of vulnerabilities displayed:
- Use the search function at the top of the page to find specific text in any of the details for all images.
- Click the filter dropdowns along the top of the page, select your desired matches and then click Show results to make them active. To remove an active filter, deselect the checkbox in the corresponding filter dropdown and then click Show results. You can also click Reset in the filter dropdowns or in the row of filters to reset all filters. You can also click on the tags in the vulnerabilities list to use them as filters.
Fixability
tip
This filter functions as an AND operator when paired with one or more Severity levels.
For example, Fixability = Yes and Severity = Critical lists images with at least one CVE that is critical and fixable.
Group by Image ID fixability filter definitions:
- Yes - The images listed contain fixable packages for the vulnerabilities found.
- No - The images listed contain unfixable packages for the vulnerabilities found.
Severity
tip
This filter functions as an AND operator when paired with one or more Fixability levels.
For example, Severity = Critical and Fixability = Yes lists images with at least one CVE that is critical and fixable.
Group by Image ID severity to filter results based on the severity of the vulnerabilities found in the container images. Filter based on the following severities:
- Critical
- High
- Medium
- Low
- Info
Container Privilege
note
Group by Image ID: Active Images tab only.
Group by Image ID container privilege filter definitions:
- Privileged - One or more privileged containers are using the images listed.
- Not Privileged - No privileged containers are using the images listed.
note
Group by CVE: Available to both tabs.
Group by CVE ID container privilege filter definitions:
- Privileged - One or more privileged containers are affected by the CVEs listed.
- Not Privileged - No privileged containers are affected by the CVEs listed.
Policy Assessment
When grouped by Image ID, filter for container images that either:
- Pass - No container policy violations were found on the image in the latest assessment.
- Fail - One or more container policy violations were found on the image in the latest assessment.
Scanner Type
Internet Exposure
note
Group by Image ID: Active Images tab only.
The vulnerability's internet exposure value is derived from the Exposure Polygraph / Attack Path Analysis feature.
Group by Image ID internet exposure filter definitons:
- Yes - Matches all images with at least one active container that have been determined as exposed to the internet during the latest Agentless or Agent scan.
- No - Matches all images with at least one active container that have been determined as not exposed to the internet during the latest Agentless or Agent scan.
- Unknown - Matches all all images with at least one active container where the internet exposure status could not be determined.
Each image assessment contains tags for the internet exposure status and when the status was last updated. The internet exposure status depends on the last update in a given time range (including up to 24 hours prior to the start time).
Build ID
note
All Images tab only
Filter for build IDs by using this Group by Image ID filter. Apply an operator (for example: includes) to help constrain your search.
Build Plan Name
note
All Images tab only
Filter for build plan names by using this Group by Image ID filter. Apply an operator (for example: excludes) to help constrain your search.
CVE
Filter for certain vulnerability IDs (CVEs) by using this Group by Image ID filter. Apply an operator (for example: includes) to help constrain your search.
Hostname
Filter for certain hostnames by using this Group by Image ID filter. Apply an operator (for example: matches) to help constrain your search.
Image ID
Filter for certain image IDs by using this Group by Image ID filter. Apply an operator (for example: does not match) to help constrain your search.
Image Namespace
Filter for certain image namespaces by using this Group by Image ID filter. Apply an operator (for example: ends with) to help constrain your search.
Image Registry
Filter for certain image registries by using this Group by Image ID filter. Apply an operator (for example: starts with) to help constrain your search.
Image Repository
Filter for certain image repositories by using this Group by Image ID filter. Apply an operator (for example: excludes) to help constrain your search.
Image Tag
Filter for certain image tags by using this Group by Image ID filter. Apply an operator (for example: includes) to help constrain your search.
User
Filter for certain users (that are running containers) by using this Group by Image ID filter. Apply an operator (for example: excludes) to help constrain your search.
Pod Namespace
note
Group by Image ID: Active Images tab only.
Filter for certain Kubernetes pod namespaces by using this Group by Image ID filter. Apply an operator (for example: includes) to help constrain your search.
K8s Cluster
note
Group by Image ID: Active Images tab only.
Filter for Kubernetes cluster names by using this Group by Image ID filter. Apply an operator (for example: includes) to help constrain your search.
Machine Tags
note
Group by Image ID: Active Images tab only.
Filter for machine tags on nodes the containers run on by using this Group by Image ID filter. Apply an operator (for example: includes) to help constrain your search.
Machine tags are metadata associated with the node (for example: AWS Instance metadata).
Package Name
Filter for package names by using this Group by CVE filter. Apply an operator (for example: starts with) to help constrain your search.
When searching for package names on images, the results contain both vulnerable and non-vulnerable packages.
Package Namespace
Filter for package namespaces by using this Group by CVE filter. Apply an operator (for example: ends with) to help constrain your search.
This can be both operating system and language library namespaces.
Package Type
Filter by package type by using this Group by CVE filter. Either Operating System or Library.
Affected Version
Filter for affected versions (of packages) by using this Group by CVE filter. Apply an operator (for example: starts with) to help constrain your search.
Fixed Version
Filter for fixed versions (of packages) by using this Group by CVE filter. Apply an operator (for example: includes) to help constrain your search.
Current Version
Filter for current versions (of packages) by using this Group by CVE filter. Apply an operator (for example: excludes) to help constrain your search.
Time Range
To change the time period, select a different one from the drop-down or use the horizontal arrows to move to the next/previous period. Select from the following past periods: hour, day, three days, week, month, or a Custom range.
Only information found during assessment of the specified date range is reported. For example, if 9 days ago a container image was removed from a container repository in the registry and the specified date range is 7 days, this container image is not listed in the table.
Save View
When the page displays your list of vulnerabilities, save the current view by clicking the Save view icon in the top right corner. This lets you access the saved view later through the Open view icon.
When you open a saved view, its name displays in the page title as Container vulnerabilities/view name. Click the icon adjacent to this name to access additional actions such as delete or duplicate.
You can also copy the link to the current view by clicking the Copy link icon. You can then share that link with others so they can see the same view. Note that searches and sorting cannot be saved in views or copied as links.
Charts
Open Vulnerabilities
The chart depicts open vulnerabilities. Hover your mouse over the Open vulnerabilities chart to see the critical, high, medium, and low vulnerabilities for that date.
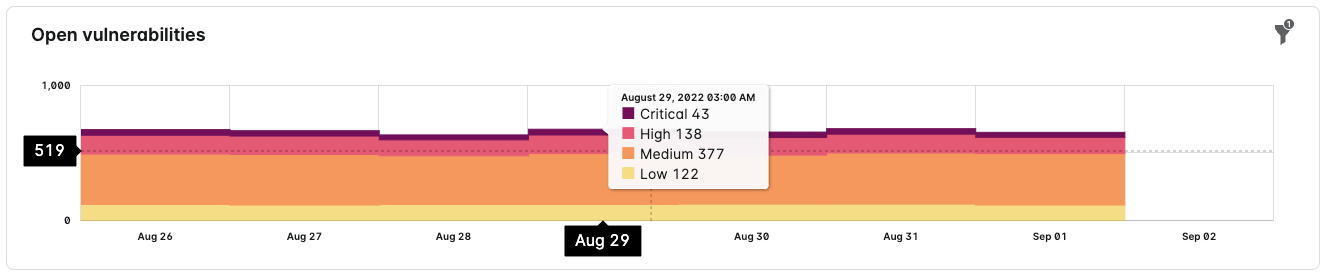
Hover over the filter icon to see the active filters that are influencing the chart.
note
The Open Vulnerabilities chart always displays a minimum of one week's results even if the time range is set to less than a week.
Group by Image ID Charts
If you select Group by Image ID/Registry/Repo, a sunburst chart appears in the row for each image name.
You can click on the image name/ID for more details. A detailed sunburst chart is displayed on the CVE tab.
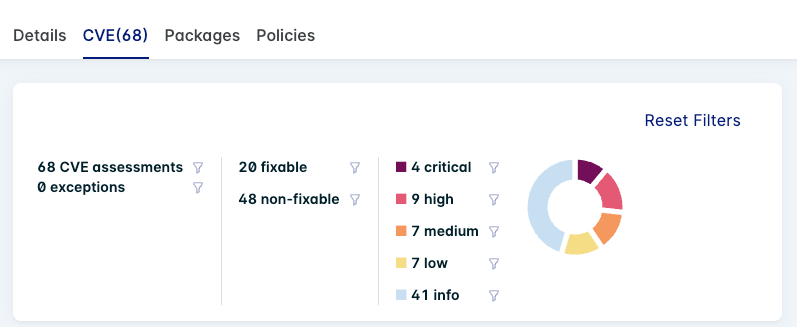
info
The numbers of vulnerabilities detailed in the sunburst chart represent only the unique vulnerabilities that Lacework discovers. Because one vulnerability can affect multiple packages, the total vulnerabilities in the list can be greater.
Vulnerabilities List
The vulnerabilities list is below the overview statistics and Open Vulnerabilities chart. The information displayed depends on how the vulnerabilities are grouped.
The vulnerability list allows you to Refresh data, Download CSV, and sort.
Click a tag link to reload the vulnerability list with the tag as the filter.
Download CSV
note
Image IDs with zero vulnerabilities are not listed in the CSV report.
There is a limit of 500,000 rows per report.
Click on the Download icon to generate a vulnerability report in CSV format.
The following options are available depending on which Group by option is selected:
- When grouped by CVE, the Download option provides the Simplified CSV.
- When grouped by Image ID, choose from Simplified, Detailed, or Custom for your CSV report.
Once you have confirmed any additional options (such as for Custom CSV), click Start the download.
A popup appears once the report is ready to download. You can also view available and in-progress downloads on the Downloads page:
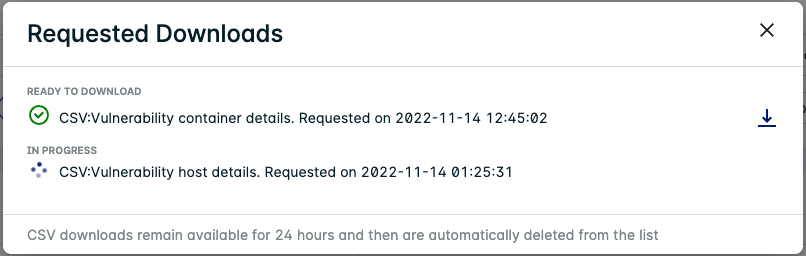
Some reports are compressed in Gzip format, you can decompress them using the following command:
gzip -d 'Container Vulnerabilities Simplified CSV.csv.gz'
Do not use tar as the format will be unrecognized.
Simplified CSV
Your active filters or tags control which Image IDs or CVEs are listed in the CSV report.
Both types list when the last assessment was performed on the Image ID/CVE.
Group by Image ID: The CSV is indexed by Image ID and provides details about the image and a summary on the number vulnerabilities found (categorized into severity and fixability).
CSV Column Description START_TIME The start time of the latest scan of the image. IMAGE_SCAN_TIME Lacework internal. IMAGE_CREATED_TIME When the image was created in the repository. EVAL_TYPE Lacework internal. EVAL_GUID Lacework internal. IMAGE_REGISTRY The image registry. IMAGE_NAMESPACE The image namespace. IMAGE_ID The SHA-256 identifier of the image. IMAGE_SIZE The image size in bytes. IMAGE_DIGEST The SHA-256 digest of the image. IMAGE_REPO The image repository. IMAGE_TAGS The image tags. IMAGE_SCAN_STATUS Whether the image was successfully scanned or not. IMAGE_SCAN_ERROR_MSG Any error message relating to an unsuccessful scan of the image. EVAL_STATUS Whether the image was successfully evaluated or not. POLICY_STATUS Whether there is a policy violation on the image or not. NUM_FIXES Number of fixable vulnerabilities found on the image. NUM_EXCEPTION Number of vulnerability exceptions applied to the image. NDV_CONTAINERS Number of active containers found using this image. PRIVILEGED Container Privilege:
1 = Privileged.
0 = Not privileged.NUM_VULNERABILITIES_SEVERITY_1 Number of Critical vulnerabilities found on the image. NUM_VULNERABILITIES_SEVERITY_2 Number of High vulnerabilities found on the image. NUM_VULNERABILITIES_SEVERITY_3 Number of Medium vulnerabilities found on the image. NUM_VULNERABILITIES_SEVERITY_4 Number of Low vulnerabilities found on the image. NUM_VULNERABILITIES_SEVERITY_5 Number of Info vulnerabilities found on the image. ENVIRONMENT_TAGS Tags of the environment where the scan took place (for example, the Inline Scanner host). RISK_SCORE LW Risk Score for the image. REQUEST_SOURCE Scanner Type INTERNET_EXPOSURE Whether one or more containers using this image have been exposed to the internet or not. INTERNET_EXPOSURE_LAST_UPDATED The last time internet exposure was determined on any containers using this image. Group by CVE: The CSV is indexed by Vulnerability (CVE) ID and provides details on the vulnerability and affected package.
CSV Column Description Affected images The number of unique images affected by the vulnerability. Vulnerability ID The identifier for the vulnerability. PACKAGE Details about the vulnerability for the affected package. PACKAGE_TAGS Same as PACKAGE. LAST ASSESSMENT The time and date when the vulnerability was last found on an affected image during a scan. Impact Score LW Risk Score for the vulnerability. Num Exception Images The number of vulnerability exceptions applied to images for this vulnerability.
Detailed CSV
Your active filters or tags control which Images or CVEs are listed in the CSV report.
The Detailed CSV is indexed by Image ID and lists details on all the CVEs applicable to the Image ID in each row.
| CSV Column | Description |
|---|---|
| IMAGE_ID | The SHA-256 identifier of the image. |
| VULN_ID | The identifier for the vulnerability. |
| SEVERITY | The severity of the vulnerability. |
| STATUS | Status of the vulnerability: EXCEPTION = Vulnerability Exception applied. VULNERABLE = No Vulnerability Exception applied. |
| FIX_AVAILABLE | Whether a fix is available for the vulnerability: 1 = Fix available. 0 = No fix available. |
| PACKAGE_NAME | The package name where the vulnerability was found. |
| PACKAGE_NAMESPACE | The package namespace where the vulnerability was found. |
| CURRENT_VERSION | The current version of the affected package. |
| FIXED_VERSION | The fixed version of the affected package. |
| IMAGE_REGISTRY | The image registry. |
| IMAGE_REPO | The image repository. |
| IMAGE_DIGEST | The SHA-256 digest of the image. |
| IMAGE_TAGS | The image tags. |
| SCAN_CREATED_TIME | The start time (in Epoch Unix format) of the latest scan of the image. |
| START_TIME | The start time of the latest scan of the image. |
Custom CSV
Define which type of CVEs are listed in the report by filtering for the Severity, Package name, Fixability, and/or CVE(s).
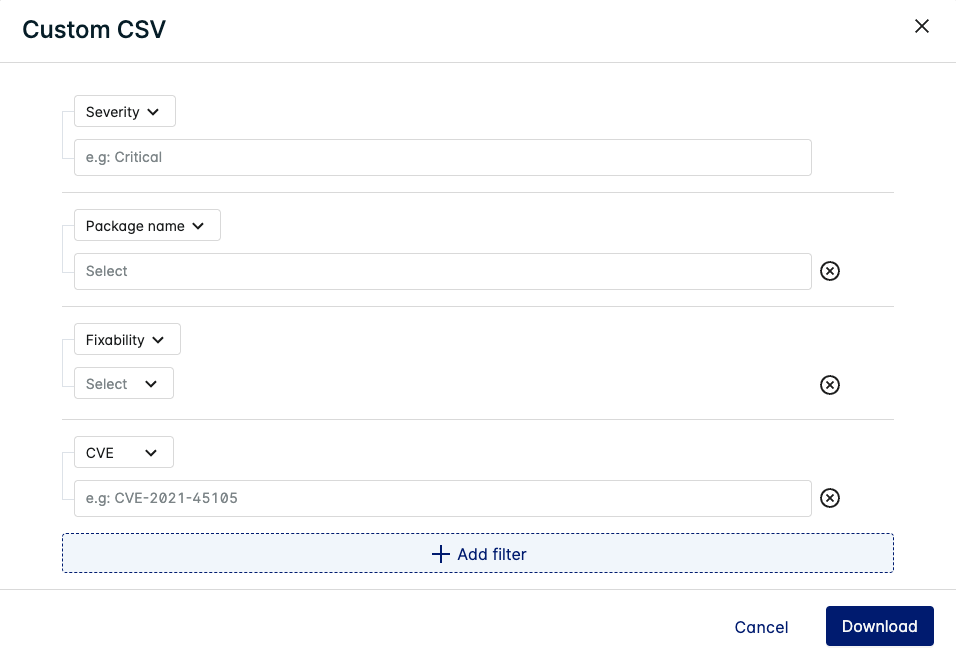
Click Download once you have specified your filters.
The Custom CSV is indexed by Image ID and lists details on the CVEs applicable to the Image ID in each row (depending on which filters you have applied).
See Detailed CSV for information about the other columns used in the Custom CSV.
Group by Image ID
When grouped by Image ID, the images shown depend on which tab is being used at the time. Use the dashboard filters to change which affected images are shown on the list.
The Group by Image ID/Registry/Repo list allows you to sort by Image Risk, Image Creation Date, Image Repository, Active Containers, or CVE Severity.
When these groups are selected, the list displays the following information:
- Image risk(default)
- Image creation date
- Image repository
- Active containers
- CVE severity
Image Assessment Drawer
Click an image name to display detailed assessment results (click the < icon to expand this view to full screen).
Image Assessment - Details
The Details tab contains descriptive information about the image. Click a detail to apply the filter to your list of Vulnerabilities. Click the Image ID tag to filter all active containers with this image.
Image Assessment - CVE (default)
The CVE tab displays a list of vulnerabilities for the image with additional information in columns. This table lets you refresh data, download CSV/PDF, filter, add/remove columns, and search.
Click the filter icon to view the active filters on the table.
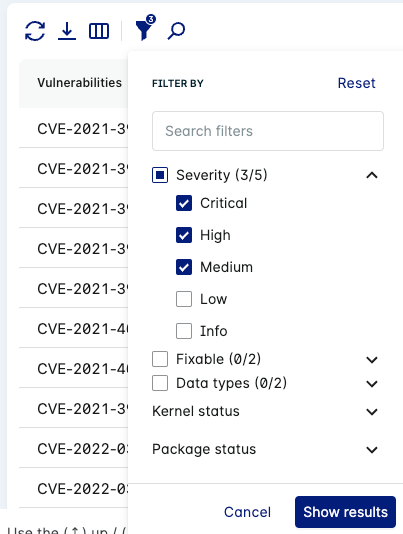
You can search for, add, and remove filters to adjust the list of vulnerabilities displayed in the table.
The available columns in the CVE tab are listed below:
| Column | Description |
|---|---|
| Vulnerabilities | Displays the common vulnerabilities and exposures (CVE) code assigned to this vulnerability by the CVE Numbering Authority. Click the More Info icon |
| Severity | Displays the CVE’s severity ranking, which is assigned by the vendor or computed from CVSSv3 or CVSSv2 scores (in that order of precedence). |
| CVSS Score | Displays the CVSS (Common Vulnerability Scoring System) severity rankings score for the vulnerability. For both CVSS 3.x and CVSS 2.0, the severity ranking is a scale from 0 - 10, where 10 is the highest severity. Defaults to CVSSv3 scores or CVSSv2 if v3 scores are not available. |
| Vulnerability impact | Displays the Lacework risk score for the vulnerability. |
| Package Name | Displays the operating system package or language package that the vulnerability was found in. |
| Current Version | Displays the current version of the package found on the image. |
| Fix Version | Displays the version of the package where the issue is fixed when a patch is available. |
| Introduced in Layer | Displays the Docker file command that applied the package onto the current Docker image. Each Docker container image is made up of a series of layers and each layer is the result of a command. |
| Image Size (hidden by default) | The size of the image affected by the vulnerability. |
| Image Repo (hidden by default) | The repository where the image was found containing the vulnerability. |
| OS Distribution | Displays the operating system and version that the vulnerability is found in. |
| Image Layer (hidden by default) | Displays the image layer digest (sha256) from where the vulnerability is found. |
| Status | Displays a status to state whether the image is affected by this vulnerability. The status will either be VULNERABLE or EXCEPTION. |
| Package Type | Displays the type of package that the vulnerability is found in. Either OS or Library. |
| File Path | If applicable, displays the filesystem path to the vulnerable package source. |
Next to the filter icon, click the Select columns icon () to show/hide columns.
Image Assessment - Packages
The Packages tab displays a list of vulnerable packages found on the image with additional information in columns. This table lets you refresh data, download CSV/PDF, add/remove columns, filter, and search.
Click the filter icon to view the active filters on the table. You can search for, add, and remove filters to adjust the list of packages displayed in the table.
note
If there is more than one vulnerability found on a package, use the dropdown icon to view each vulnerability found on that package.
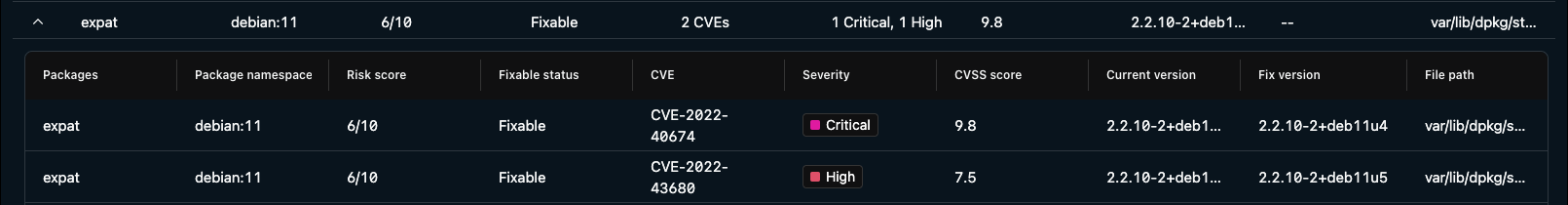
The available columns in the Packages tab are listed below:
| Column | Description |
|---|---|
| Packages | Displays the vulnerable operating system package or language package that was found on the image. |
| Package namespace | Displays the namespace of the vulnerable package. |
| Risk Score | Displays the Lacework risk score for the package. |
| Fixable Status | Displays whether the package fixable or not (whether there is a new or patched version of the package available). |
| CVE | Displays the common vulnerabilities and exposures (CVE) code assigned to this vulnerability by the CVE Numbering Authority. |
| Severity | Displays the CVE’s severity ranking, which is assigned by the vendor or computed from CVSS v3 or CVSS v2 scores (in that order of precedence). |
| CVSS Score | Displays the CVSS (Common Vulnerability Scoring System) severity rankings score for the vulnerability. Hover over the score for the CVSS version. For both CVSS v3 and CVSS v2, the severity ranking is a scale from 0 - 10, where 10 is the highest severity. Defaults to CVSS v3 scores or CVSS v2 if v3 scores are not available. |
| Current Version | Displays the current version of the package found on the image. |
| Fix Version | Displays the version of the package where the issue is fixed (when a patch is available). |
| File Path | If applicable, displays the filesystem path to the vulnerable package source. |
Image Assessment - Policies
The Policies tab lists any active container vulnerability policies that apply to the image.
Group by CVE
When grouped by CVE, all active and non-active images are shown regardless of which tab is being used at the time. Use the dashboard filters to change which affected images are shown on the list.
The Group by CVE/Package Name/Package Namespace list allows you to sort by Vulnerability Impact / Package Risk(default), Severity, CVSS Score, Vulnerability ID, or Affected Images.
When these groups are selected, the list displays the following information:
- Vulnerability (CVE) ID
- Vulnerability Impact / Package Risk
- Number of affected images
tip
Use the Package type filter to list either OS or Library packages.
CVE Assessment Drawer
Click a Vulnerability ID to display detailed assessment results (click the < icon to view this drawer in full screen).
CVE Assessment - Details
The Details tab contains descriptive information about the vulnerability. Click a detail to filter the vulnerability list based on the detail.
If there is a CVSS v3 score available for the vulnerability, additional information will be displayed that is derived from CVSS Metrics (such as Attack Vector, Access Complexity, etc).
CVE Assessment - Images (default)
The Images tab displays a list of image names where the vulnerability was found with additional information in columns. This table lets you refresh data, download as CSV/PDF, select which columns to display, and search.
note
The list of images shown for the CVE depend on which tab is selected:
- All Images - The number of images listed in the table matches the Affected images count.
- Active Images - Only active images that are affected by the CVE are listed in the table.
The available columns in the Images tab are listed below:
| Column | Description |
|---|---|
| Image Name | Displays the image name that the vulnerability was found in. The image name may be presented in the format of repository-name:image-name. |
| Repository (hidden by default) | The repository where the vulnerability was found. |
| Image Tags (hidden by default) | The image tag affected by the vulnerability. |
| Image ID | Displays the sha256 hash that was generated for this image. You can copy the container image ID to the clipboard by clicking the Copy to clipboard |
| Image Created Time | Displays when the image was created in the repository. |
| Last Assessment (hidden by default) | When the image was last assessed for vulnerabilities by Lacework. |
| Active Containers | Displays the total number of unique and active containers that ran for this image. Note: Lacework must be integrated with your container registries for these reports. |
| Image Risk | Displays the Lacework risk score for the image. A higher score indicates more risk/impact from discovered vulnerabilities. |
| Status | Displays the vulnerability status of the image. The status will either be VULNERABLE or EXCEPTION. |
Vulnerability Continuous Assessment
Lacework continuously reassesses container images for new vulnerabilities. Lacework lets you control what images are continually reevaluated. You can globally override the default option and configure what images should be assessed.
- Go to Settings > General in the Lacework Console to display the General Settings page.
- Scroll down to the bottom of the page to configure Continuous Assessments.
- Under Continuous Assessments, enable Reassess active images to reassess only active images in the past 24 hours.