Integrate with Kubernetes Admission Controller
Overview
The Kubernetes Admission Controller acts as the last point of enforcement before images are deployed (rather than at runtime or build). It helps define and customize what is allowed to run on a cluster. Use our ValidatingAdmissionWebhook with the Kubernetes Admission Controller to automatically scan images for vulnerabilities and enforce security policies during continuous deployment.
Install our Proxy Scanner and Webhook together in your Kubernetes cluster to allow communication between Lacework and the Admission Controller.
Once integrated, associate the policies with a registry integration or associate registry integrations with a policy in the Lacework Console. Choose to block or allow continuous deployment when a policy violation occurs (if the criteria of a policy is not met).
Workflow
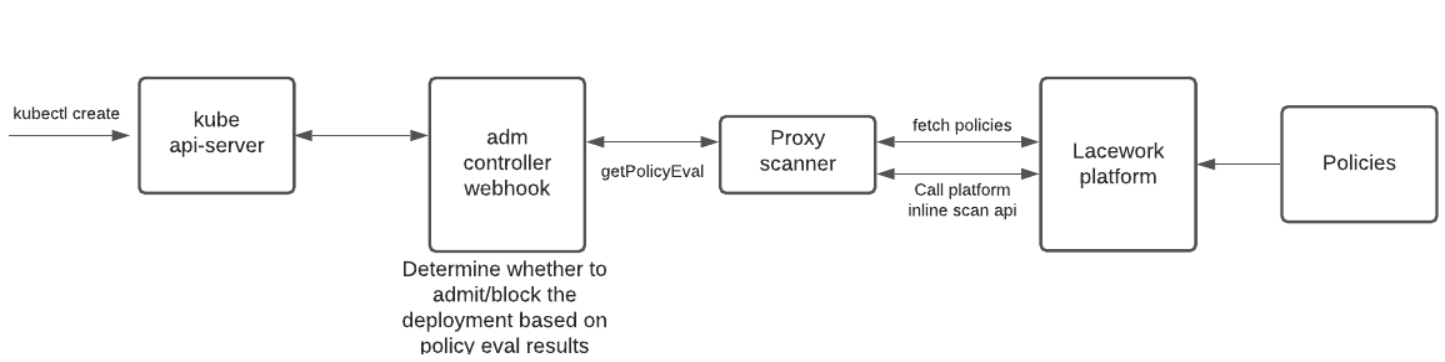
Default Scanning Quotas
See Proxy Scanner Default Scanning Quotas.
Prerequisites
Choose your installation method first as some prerequisite steps will change depending on your chosen method.
Once you have selected your installation method, complete the following prerequisites:
- Provide or generate the TLS/SSL certificates that are set during installation.
- Prepare the Proxy Scanner configuration, which is referenced during installation.
- Consider Kubernetes workload resources that you want to exclude from vulnerability scans.
Installation Methods
Choose one of the following installation methods for the Proxy Scanner and Webhook:
Option 1: Install the Webhook and Proxy Scanner in a Combined Helm Chart (Recommended).
Use this method to install both the Webhook and Proxy Scanner on the same host as the Kubernetes Admission Controller.Option 2: Install the Proxy Scanner and Webhook in Separate Helm Charts.
This method can be used to install the Webhook and Proxy Scanner on separate hosts (or if you already have the Proxy Scanner installed).Option 3: Download and Install the Helm Charts Manually.
This method allows you to download templates for both the Proxy Scanner and Webhook configuration (values.yaml) and configure them manually prior to installation.
Helm Charts help you define, install, and upgrade Kubernetes applications.
Create TLS/SSL Certificates
Secure communication between the Admission Controller Webhook and the Kubernetes API server by providing Base64 encoded certificates for the Webhook. Choose from one of the following options:
- Option 1: Provide your own certificates.
- Option 2: Generate the certificates using a script provided in the Lacework Helm Charts repository.
Optionally, secure communication between the Proxy Scanner and Admission Controller Webhook by providing Base64 encoded certificates for the Proxy Scanner.
important
The lacework namespace should be used when installing the Admission Controller Webhook and Proxy Scanner.
If integrating with EKS Fargate, make sure the lacework namespace is added to your Fargate profile:
eksctl create fargateprofile \
--cluster <fargate_cluster_name> \
--name <fargate_profile_name> \
--namespace lacework
If you want to deploy in a different namespace, ensure that the domain of the Subject Alternative Names in your certificates are adjusted accordingly.
Provide Your Own Certificates
Provide your own Base64 encoded certificates for the Admission Controller Webhook. Create these files for the following properties or values during installation:
| File to use | Entries in values.yaml or Helm entry |
|---|---|
| Webhook Root CA | <base64_webhook_ca.crt> |
| Webhook server certificate | <base64_webhook.crt> |
| Webhook server key | <base64_webhook.key> |
Proxy Scanner Certificates (Optional)
Create these files for the following properties or values during installation:
| File to use | Entries in values.yaml or Helm entry |
|---|---|
| Proxy Scanner Root CA | <base64_scanner_ca.crt> |
| Proxy Scanner server certificate | <base64_scanner.crt> |
| Proxy Scanner server key | <base64_scanner.key> |
Encode the certificates in Base64 format before using them.
cat myScannerCA.crt | base64 | tr -d '\n' > myScannerCA.crt_b64
Generate Certificates Using the Script in the Lacework Helm Charts Repository
Get the latest copy of the Admission Controller from the Lacework Helm Charts repository
tip
If using Helm, you can pull the repository directly using
helm pull lacework/admission-controller.The file will be in the format of admission-controller-<version>.tgz.
Extract the script:
tar -xvf admission-controller-*.tgz \
admission-controller/generate-certs.shThis extracts the script to a subdirectory named 'admission-controller' in your current working directory.
Run the script to generate the certificates:
cd admission-controllerchmod u+x generate-certs.sh./generate-certs.shUse these generated files for the following properties or values during installation:
File to use Entries in values.yaml or Helm entry ca.crt_b64<base64_webhook_ca.crt>admission.crt_b64<base64_webhook.crt>admission.key_b64<base64_webhook.key>
Generate the Proxy Scanner certificates (Optional)
note
Generating certificates using the script in the Lacework Helm Charts repository only provides the Webhook certificates.
You can reuse the same certificates for the Proxy Scanner if you generated them for the Webhook:
| File to use | Entries in values.yaml or Helm entry |
|---|---|
ca.crt_b64 (same as the Webhook Root CA) | <base64_scanner_ca.crt> |
admission.crt_b64 | <base64_scanner.crt> |
admission.key_b64 | <base64_scanner.key> |
Configure the Proxy Scanner
Configure the Proxy Scanner to authenticate with Lacework and automatically initiate scans prior to deployment. This also allows container vulnerability policies to be evaluated during scans. Scan results are then sent to the Admission Controller prior to pod deployment.
During installation of the Proxy Scanner, the values.yaml file will need to be provided. This section explains how to prepare this file depending on your installation method.
note
If choosing the manual installation method, a template of values.yaml is downloaded as part of the installation and does not need to be prepared in advance.
Proxy Scanner Config for Combined Helm Chart
When installing the Webhook and Proxy Scanner in a Combined Helm Chart, create the values.yaml file in advance by using the following blank template of the proxy-scanner section:
proxy-scanner:
config:
scan_public_registries:
default_registry:
static_cache_location: /opt/lacework
lacework:
account_name:
integration_access_token:
existingSecret:
key:
name:
registry_secret_name:
registries:
- domain:
name:
ssl:
auto_poll: false
is_public:
auth_type:
auth_header_name:
credentials:
user_name:
password:
poll_frequency_minutes: 20
disable_non_os_package_scanning:
go_binary_scanning:
enable:
scan_directory_path: ""
See Configure the Proxy Scanner for on-demand scans for instructions on how to populate the configuration.
There are also example configurations available to view (other authentication types with examples can be found in this section).
Proxy Scanner Config for Separate Helm Charts
When installing the Proxy Scanner and Webhook in Separate Helm Charts, create the values.yaml file in advance by using the following blank template of the config section:
config:
scan_public_registries:
static_cache_location: /opt/lacework
default_registry:
lacework:
account_name:
integration_access_token:
existingSecret:
key:
name:
registry_secret_name:
registries:
- domain:
name:
ssl:
auto_poll: false
is_public:
auth_type:
auth_header_name:
credentials:
user_name:
password:
poll_frequency_minutes: 20
disable_non_os_package_scanning:
go_binary_scanning:
enable:
scan_directory_path: ""
See Configure the Proxy Scanner for on-demand scans for instructions on how to populate the configuration.
There are also example configurations available to view (other authentication types with examples can be found in this section).
Exclude Workload Resources
warning
It is highly recommended that all resources except Pod are excluded from scans. All other resources may spawn multiple child resources, and these will cause excessive scanning during the deployment if not excluded.
For example, a CronJob will spawn instances of Jobs, which can also launch Pods. If only CronJob and Job are excluded, then a scan will still be triggered on Pod.
Only remove resources from the exclude list if you are okay with the additional delay that may occur during deployments.
You can exclude Kubernetes Workload Resources from vulnerability scans by adding them to an excluded resources list.
The types of resources that can be excluded from scans are:
PodDeploymentReplicaSetDaemonSetJobCronJobStatefulSet
Edit the values.yaml to Exclude Resources
Exclude resources by adding an admission.excluded_resources field to the values.yaml file for the Admission Controller Webhook configuration.
If not added, the default configuration will exclude all resources except Pod (which is recommended).
The example below is an exhaustive list of all possible resources that can be excluded. Only add the resources that you want to exclude from scanning.
admission:
excluded_resources:
- Pod
- Deployment
- ReplicaSet
- DaemonSet
- Job
- CronJob
- StatefulSet
Where and when to add this field depends on which installation method you have chosen:
Combined Helm Chart: Add this field to the Proxy Scanner configuration prior to installation as it can contain both Proxy Scanner and Webhook configuration.
Separate Helm Charts: Create a separate
values_resources.yamlfile and add this field as the contents. It can then be used when prompted during the Webhook installation steps.Manual Installation: Add this field to the
values.yamlwhen prompted during the Webhook installation steps.
Installation Steps
Option 1: Install the Webhook and Proxy Scanner in a Combined Helm Chart
Before you begin, ensure you have all the TLS/SSL certificates in your working directory.
Add the Lacework Helm Charts repository:
helm repo add lacework https://lacework.github.io/helm-charts/Install and configure the Admission Controller Webhook and Proxy Scanner by using the
values.yamlfile created earlier:helm upgrade --install --create-namespace --namespace lacework \
--set webhooks.caBundle=`cat <base64_webhook_ca.crt>` \
--set certs.serverCertificate=`cat <base64_webhook.crt>` \
--set certs.serverKey=`cat <base64_webhook.key>` \
--values values.yaml \
lacework-admission-controller lacework/admission-controller(Optional) If you want to secure communication between the Proxy Scanner and Admission Controller Webhook, include these optional properties:
--set scanner.skipVerify=false \
--set scanner.caCert=`cat <base64_scanner_ca.crt>` \
--set proxy-scanner.certs.skipCert=false \
--set proxy-scanner.certs.serverCertificate=`cat <base64_scanner.crt>` \
--set proxy-scanner.certs.serverKey=`cat <base64_scanner.key>` \Examplehelm upgrade --install --create-namespace --namespace lacework \
--set webhooks.caBundle=`cat <base64_webhook_ca.crt>` \
--set certs.serverCertificate=`cat <base64_webhook.crt>` \
--set certs.serverKey=`cat <base64_webhook.key>` \
--values values.yaml \
--set scanner.skipVerify=false \
--set scanner.caCert=`cat <base64_scanner_ca.crt>` \
--set proxy-scanner.certs.skipCert=false \
--set proxy-scanner.certs.serverCertificate=`cat <base64_scanner.crt>` \
--set proxy-scanner.certs.serverKey=`cat <base64_scanner.key>` \
lacework-admission-controller lacework/admission-controllerAlternatively, provide the full Base64 encoded string for each certificate instead of the
cat certificateFilecommand.(Optional) If you want to exclude workload resources from vulnerability scans, ensure you have added the
admission.excluded_resourcesfield to thevalues.yamlfile.
Display the pods for verification:
kubectl get pods -n lacework
Option 2: Install the Proxy Scanner and Webhook in Separate Helm Charts
Install the Proxy Scanner with Helm
Before you begin, ensure you have all the TLS/SSL certificates in your working directory.
Add the Lacework Helm Charts repository:
helm repo add lacework https://lacework.github.io/helm-charts/Install and configure the Proxy Scanner by using the
values.yamlfile created earlier:helm upgrade --install --create-namespace --namespace lacework \
--values values.yaml \
lacework-proxy-scanner lacework/proxy-scanner(Optional) If you want to secure communication between the Proxy Scanner and Admission Controller Webhook, include these optional properties:
--set certs.skipCert=false \
--set certs.serverCertificate=`cat <base64_scanner.crt>` \
--set certs.serverKey=`cat <base64_scanner.key>` \Examplehelm upgrade --install --create-namespace --namespace lacework \
--set certs.skipCert=false \
--set certs.serverCertificate=`cat <base64_scanner.crt>` \
--set certs.serverKey=`cat <base64_scanner.key>` \
--values values.yaml \
lacework-proxy-scanner lacework/proxy-scanner
Display the pods for verification:
kubectl get pods -n lacework
Install the Admission Controller Webhook With Helm
Before you begin, ensure you have all the TLS/SSL certificates in your working directory.
Install and configure the Admission Controller Webhook:
helm upgrade --install --create-namespace --namespace lacework \
--set proxy-scanner.enabled=false \
--set webhooks.caBundle=`cat <base64_webhook_ca.crt>` \
--set certs.serverCertificate=`cat <base64_webhook.crt>` \
--set certs.serverKey=`cat <base64_webhook.key>` \
lacework-admission-controller lacework/admission-controller(Optional) If you want to exclude workload resources from vulnerability scans, include the
values_resources.yamlfile that was created earlier.--values values_resources.yaml \Examplehelm upgrade --install --create-namespace --namespace lacework \
--set proxy-scanner.enabled=false \
--set webhooks.caBundle=`cat <base64_webhook_ca.crt>` \
--set certs.serverCertificate=`cat <base64_webhook.crt>` \
--set certs.serverKey=`cat <base64_webhook.key>` \
--values values_resources.yaml \
lacework-admission-controller lacework/admission-controller(Optional) If you want to secure communication between the Proxy Scanner and Admission Controller Webhook, include this optional property:
--set scanner.caCert=`cat <base64_scanner_ca.crt>` \
--set scanner.skipVerify=false \Examplehelm upgrade --install --create-namespace --namespace lacework \
--set proxy-scanner.enabled=false \
--set webhooks.caBundle=`cat <base64_webhook_ca.crt>` \
--set certs.serverCertificate=`cat <base64_webhook.crt>` \
--set certs.serverKey=`cat <base64_webhook.key>` \
--set scanner.caCert=`cat <base64_scanner_ca.crt>` \
--set scanner.skipVerify=false \
lacework-admission-controller lacework/admission-controller
Display the pods for verification:
kubectl get pods -n lacework
Option 3: Download and Install the Helm Charts Manually
Install the Proxy Scanner Manually
Get the latest copy of the Proxy Scanner from the Lacework Helm Charts repository.
The file will be in the format of
proxy-scanner-<version>.tgz.Extract the Proxy Scanner files into your current working directory:
tar -xvf proxy-scanner-*.tgzThis creates the 'proxy-scanner' directory containing the related files.
Edit the
proxy-scanner/values.yamlfile to configure the Proxy Scanner for on-demand scans (follow the links for instructions on how to populate the configuration). There are also example configurations available to view for each authentication type.(Optional) If you want to secure communication between the Proxy Scanner and Admission Controller Webhook, provide the scanner certificate and key entries in the
values.yamlfile.certs:
skipCert: false
serverCertificate: "<base64_scanner.crt>"
serverKey: "<base64_scanner.key>"Provide the full Base64 encoded strings for the certificates encapsulated in double quotes.
Install the Proxy Scanner:
helm install -n lacework --create-namespace lacework-proxy-scanner ./proxy-scannerDisplay the pods for verification:
kubectl get pods -n lacework
Install the Admission Controller Webhook Manually
Get the latest copy of the Admission Controller from the Lacework Helm Charts repository.
The file will be in the format of
admission-controller-<version>.tgz.Extract the Admission Controller Webhook files into your current working directory:
tar -xvf admission-controller-*.tgzThis creates the 'admission-controller' directory containing the related files.
Provide the certificate entries in
values.yamlfor the Admission Controller.certs:
name: lacework-admission-certs
serverCertificate: "<base64_webhook.crt>"
serverKey: "<base64_webhook.key>"
webhooks:
caBundle: "<base64_webhook_ca.crt>"Provide the full Base64 encoded strings for the certificates encapsulated in double quotes.
(Optional) If you want to exclude workload resources from vulnerability scans, add the
admission.excluded_resourcesfield to thevalues.yaml.(Optional) If you want to secure communication between the Proxy Scanner and Admission Controller Webhook, provide the scanner root CA entry in the
values.yamlfile:scanner:
skipVerify: false
caCert: "<base64_scanner_ca.crt>"Provide the full Base64 encoded string for the certificate encapsulated in double quotes.
Install the Admission Controller Webhook:
helm install -n lacework --create-namespace lacework-admission-controller ./admission-controllerDisplay the pods for verification:
kubectl get pods -n lacework
Configurable Parameters for Admission Controller Webhook
The following table lists all parameters for the Admission Controller Webhook configurable in the values.yaml file:
| Parameter | Description | Default | Mandatory |
|---|---|---|---|
logger.debug | Set to enable debug logging | false | NO |
certs.name | Secret name for Helios certs | helios-admission-certs | NO |
certs.serverCertificate | Certificate for TLS authentication with the Kubernetes api-server | N/A | YES |
certs.serverKey | Certificate key for TLS authentication with the Kubernetes api-server | N/A | YES |
webhooks.caBundle | Root certificate for TLS authentication with the Kubernetes api-server | N/A | YES |
policy.block_exec | Set to enable 'exec' shell access to a Kubernetes pod. | false | NO |
policy.bypass_scope | CSV of namespaces to bypass | kube-system,kube-public,lacework,lacework-dev | NO |
nodeSelector | Kubernetes node selector | {} | NO |
scanner.server | Lacework proxy scanner name | lacework-proxy-scanner | NO |
scanner.namespace | Namespace in which it is deployed | lacework | NO |
scanner.skipVerify | SSL between the webhook and the scanner | true | NO |
scanner.caCert | Root cert of scanner | N/A | NO |
scanner.timeout | Context deadline timeout | 30 | NO |
scanner.defaultRegistry | Default registry to use when one is not provided in the image name | index.docker.io | NO |
admission.excluded_resources | List of resources to skip admission review | N/A | NO |
scanner.blockOnError | Block admission request if proxy scanner returns error | false | YES |
scanner.defaultRegistry Configuration
If the scanner.defaultRegistry value is changed to be empty (the default value of index.docker.io would need to be removed), the registry must also be provided when supplying the image name that you want to scan.
Configuring Parameters After Installation
important
You can configure parameters using Helm after an installation, but the changes will not become active until you redeploy.
Configure parameters by using either of the following methods:
Method 1: Make Changes to values.yaml
Make your changes to the values.yaml and push them through Helm:
helm upgrade --values values.yaml lacework-admission-controller lacework/admission-controller
helm upgrade --values values.yaml lacework-proxy-scanner lacework/proxy-scanner
Method 2: Set Values Directly
Set values directly using Helm:
helm upgrade --set logger.debug=true lacework-admission-controller lacework/admission-controller
helm upgrade --set default_registry="NewDefaultRegistry.io" lacework-proxy-scanner lacework/proxy-scanner
Default Scan Behavior
If a Kubernetes image tag is not specified during a scan, the latest tag is used by default.