Container Vulnerability Policies
Overview
Create container vulnerability policies to assess your container images at build and/or runtime based on your own unique requirements. A policy is a set of rules that can define the following:
- The conditions to be triggered, for example:
- Any critical vulnerability with a fix available.
- A base image not including the
latesttag. - A dockerfile invoking
rootorsudouser.
- A severity, such as low, medium, high, or critical.
- An action for build-time, such as alert, warn, or block.
- The status of the policy: Enabled or Disabled.
Each policy can be associated with a registry integration that has been configured in Lacework. This includes Proxy and Inline Scanner integrations (Kubernetes Admission Controller integrations are also included as the Proxy Scanner is deployed as part of those integrations).
Lacework also provides a number of default policies that can be enabled or disabled depending on your requirements.
Vulnerability Policy Management
All container vulnerability policies are managed through the Policies page in the Lacework Console.
Default policies are read-only except for the Action on failure, Status, and Scope fields.
tip
View Container Vulnerability Policies by using the Domain: Container filter on the Policies page.
Create a Policy
Follow these steps to create a container vulnerability policy:
- Click Policies.
- Create new policies by cloning existing ones. Locate and click the policy you want to base your policy on. Ensure that the policy type is correct for your new policy, as this field cannot be edited.
- In the policy window:
- If the Clone policy icon is available, you can clone the policy.
- If the Clone policy icon is not available, the policy cannot be cloned or the policy has already been cloned the maximum number of times (4 clones).
- Once cloned, click the edit option for the title
to provide the event name that is generated when the policy triggers. Click Save when complete.
- On the Summary tab, edit the Description field and change the Action on failure and Severity fields as desired. Click Save when complete.
- Click the Query tab in the policy drawer and fill in your parameters. The subsections in Container Vulnerability Policy Types provide the available parameters for each Type.
- Click Save after completing the parameters.
- The policy is enabled by default. If you want to disable the policy, toggle the Status
.
Container Vulnerability Policy Types
All container vulnerability policies are managed through the Policies page. The subsections below detail the parameters for each Type.
CVE
Define the disallowed package names or CVE IDs that will cause a violation to occur when found on an image. You can also define the maximum number of CVEs (including severity and fixability) that can be found on an image before a violation occurs.
| Parameter | Data Type & Operators | Description |
|---|---|---|
| Package name | String * includes any of | Specify the name of the software package(s), such as vim. You can specify multiple values but they will be considered as "or" values (rather than "and"). |
| CVE ID | String * includes any of | Specify the CVE ID full name(s), such as CVE-2019-01234, CVE-2019-5678. You can specify multiple values but they will be considered as "or" values (rather than "and"). |
| CVE count | Integer * Greater than Severity * includes fixability * matches | Specify the number of CVEs that would need to be discovered in an image before the policy is triggered. Define the policy criteria further by including the severity level and fixability of the CVEs. |
Image
Define the allowed image tags or labels for your container registries. Any tag or label that does not match the final filter (data type + operator) will cause a violation to occur.
| Parameter | Data Type & Operators | Description |
|---|---|---|
| Image Tag | String * does not include | Specify the image tag(s). A typical tag could look like DATE_BRANCH_RANDOM_ID, such as 2019-10-10_master_db0dd95. You can specify multiple values but they will be considered as "or" values (rather than "and"). |
| Image Label | String * includes any of | Specify the image label(s), such as author, maintainer, or buildID. You can specify multiple values but they will be considered as "or" values (rather than "and"). |
Dockerfile
Define any commands (or any string) that will cause a violation when found in a Dockerfile.
| Parameter | Data Type & Operators | Description |
|---|---|---|
| Dockerfile | String * includes * does not include | Check for specific strings in your dockerfile, such as sudo, or USER root. You can specify multiple values but they will be considered as "or" values (rather than "and"). |
Edit a Policy
To edit a policy, click a policy in the Policies page and then click the edit option.
Delete a Policy
To delete a policy, click it in the Policies page and then click the delete option.
Disable/Enable a Policy
On the Policies page, find the policy and click the Status toggle to disable or enable the policy.
Associate Policies with a Registry Integration
For each registry integration, an optional setting can be used to enable container vulnerability policies (also known as CI/CD policies).
The first step depends on whether this is a new or existing integration:
- For new integrations, follow the steps to Create a Proxy Scanner Integration in Lacework up to when you reach the Optional Settings page.
- For existing integrations, go to Settings > Integrations > Container Registries in the Lacework Console. Select the registry by clicking the checkbox on the left-hand column and click the Edit icon
. Proceed to the Optional Settings page.
Click Select policies (optional) underneath CI / CD Policies to view a table of all container vulnerability policies.
Select individual policies by clicking the checkbox on the left-hand column. If you want to enable all policies, click the checkbox for the entire column.
Select which columns are displayed by using the Select columns
option.
Click Add to integration once you have selected your policies.
The policies are listed on the Optional Settings page. If/When returning to this page, click the edit icon
if you want to add or remove policies.
Finish configuring any other optional settings and click Save.
Dissociate policies with a registry integration at any time by repeating this procedure and deselecting the policies during step 3.
Associate Registry Integrations with a Policy
Associate registries with a container vulnerability policy on the Policies page in the Lacework Console.
On the Policies page, click the policy that you want to associate a registry (or registries) with.
tip
Use the Container filter to display only container vulnerability policies.
To add registry integrations to the policy, click the edit
option in the Scope field (Summary tab).
To select individual registries, select the checkbox in the left-hand column. If you want to enable all registries for this policy, select the checkbox for the entire column.
Select which columns are displayed by using the Select columns
option.
Click Add to policy once you have selected your registries.
The registry integrations are then displayed in the Scope field.
Dissociate registry integrations with a policy at any time by repeating this procedure and deselecting the registries during step 3.
Action on Failure
Define what action is taken when a policy failure occurs.
On the Policies page in the Lacework Console, filter or search for your specific policy.
Click a policy in the policy list to view the drawer.
In the Summary tab, select the option you prefer for Action on failure:
Allow: This permits container image deployment to continue even when the policy fails.
Block: This blocks container image deployment when the policy fails.
Any change is reflected in new container deployments where policies are associated with a registry integration or are in the scope of the policy. New policy changes will be fully active within 5 minutes on the container registry integration (this includes Inline, Proxy, or Admission Controller with Proxy Scanner integrations).
Policy Changes
Any changes to policies will be fully propagated to the container registry integration within 5 minutes.
Policy Evaluation Results
View evaluation results for container vulnerability policies on the Vulnerabilities > Containers page.
Click on an image name in the vulnerabilities list and click the Policies tab to display the evaluation results.
Two charts display the number of failed vs passing policies, and the number of policies by severity.
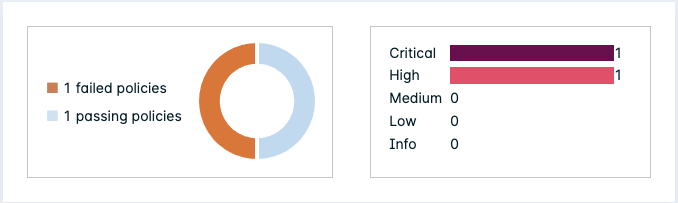
The following info is shown in the table:
| Column | Description |
|---|---|
| Policy | A description of the policy. If the policy has failed, you can click on it for information including: * Resource - The resource related to the policy failure. * Reason - The reason for the failure of the policy. |
| Severity | The severity level of the policy; Info, Low, Medium, High, or Critical. |
| Status | Whether the image evaluation has passed or failed for this policy. |
Using Helm
Helm informs you when a successful deployment occurs for a Kubernetes cluster. If the deployment is blocked due to a policy violation, check the Admission Controller logs for failures.
Default Policies
Default policies are read-only except for the Action on failure, Status, and Scope fields.
There are a number of default policies that are enabled by default for container vulnerability. The following table lists each default policy that we provide:
| Policy ID | Event Generated by Policy | Description |
|---|---|---|
| LW_CONTAINER_POLICY_1 | Disallowed packages | PackageName includes any of package1, package2.Note: This is a dummy policy for demonstration purposes only. |
| LW_CONTAINER_POLICY_2 | Disallowed CVEs | CVE ID includes any of CVE-2020-1234.Note: This is a dummy policy for demonstration purposes only. |
| LW_CONTAINER_POLICY_3 | Critical, fixable CVEs | Critical and fixable CVE count greater than 0.Note: This is a dummy policy for demonstration purposes only. |
| LW_CONTAINER_POLICY_4 | Critical CVEs | Critical CVE count greater than 0.Note: This is a dummy policy for demonstration purposes only. |
| LW_CONTAINER_POLICY_5 | Image with a 'latest' tag | Image Tag does not include latest |
| LW_CONTAINER_POLICY_6 | Missing required image labels | Image Label includes any of author, maintainer, or buildID |
| LW_CONTAINER_POLICY_7 | ENTRYPOINT defined with root privilege | Dockerfile includes ENTRYPOINT ["sudo"* |
| LW_CONTAINER_POLICY_8 | apt-get upgrade, apk upgrade, or dist-upgrade commands Dockerfile | Dockerfile includes apt-get get upgrade, apk upgrade, dist-upgrade |
| LW_CONTAINER_POLICY_9 | ’apk add’ is not used with --no-cache in Dockerfile | Dockerfile includes apk *--no-cache |
| LW_CONTAINER_POLICY_10 | apt-get caches are not cleared in Dockerfile | Dockerfile does not include apt-get clean |
| LW_CONTAINER_POLICY_11 | USER is not defined in Dockerfile | Dockerfile does not include USER |
| LW_CONTAINER_POLICY_12 | USER is defined as root | Dockerfile includes USER root |
| LW_CONTAINER_POLICY_13 | sudo command used in Dockerfile | Dockerfile includes sudo |
Edit a Default Policy
Default Policies cannot be edited except for the Action on failure, Status, and Scope fields. They can be cloned or you can disable the default policy if required.
Delete a Default Policy
Default policies cannot be deleted, only disabled.
Disable/Enable a Default Policy
On the Policies page, find the default policy and click the Status toggle to disable or enable the policy.
Policies Chart
The Policies page display a visual summary detailing the following information:
- Coverage - Shows total number of policies, including the number of enabled vs disabled, and the number of policy exceptions.
- Policy Types - Shows the number of default vs custom policies.
- Policies By Severity - Shows the number of policies for each severity.
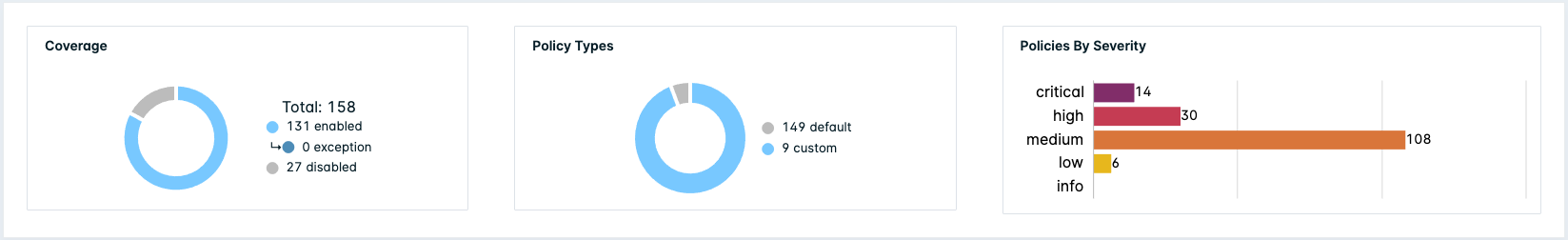
The chart updates when any filters are active.
Inline Scanner Support
Container Vulnerability Policies can be used with the Inline Scanner trigger exit codes during image evaluations. Find out more in the policy support section for Inline Scanner.