Policies Overview
Lacework policies help you maintain the security of your cloud integrated environments by detecting conditions and events that indicate risk. A Lacework policy combines a condition statement, an action, a severity level, and other policy-specific settings.
This topic introduces you to Lacework policies and how to view and configure policies in the Lacework Console.
View Policies
You can view and work with policies in the Policies page in the Lacework Console. To view Lacework policies, log in to the Lacework Console and click Policies from the left navigation menu.
The page consists of a dashboard and the policy list. The dashboard presents a graphical view of the policy list, showing the number of policies enabled and disabled, policies by type, and policies by severity.
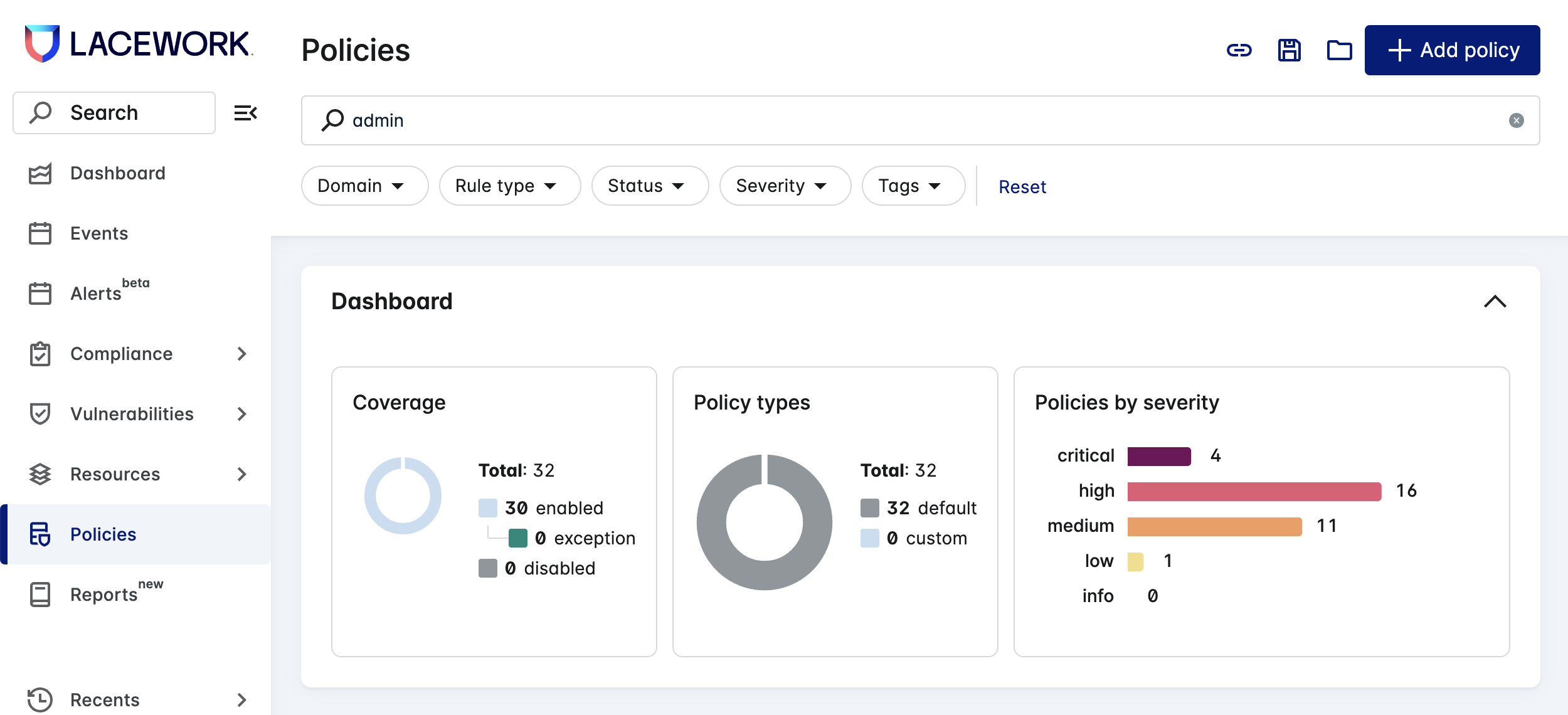
You can hide the dashboard by clicking the collapse icon at the top right.
Filter Policies
The policy list displays up to 50 policies at a time. Use the arrows to page through the policy list or the Sort by menu to order policies by name, severity, or date of last update.
The filtering options enable you to specify criteria for which policies appear in the policies list. Filters let you select policies by domain, type, status, severity, and more.
The filtering options are dynamic. For example, if you filter domain on AWS, the policy types relevant to AWS appear in the Type filter options, such as S3, Identity and Access Management, and CloudTrail.
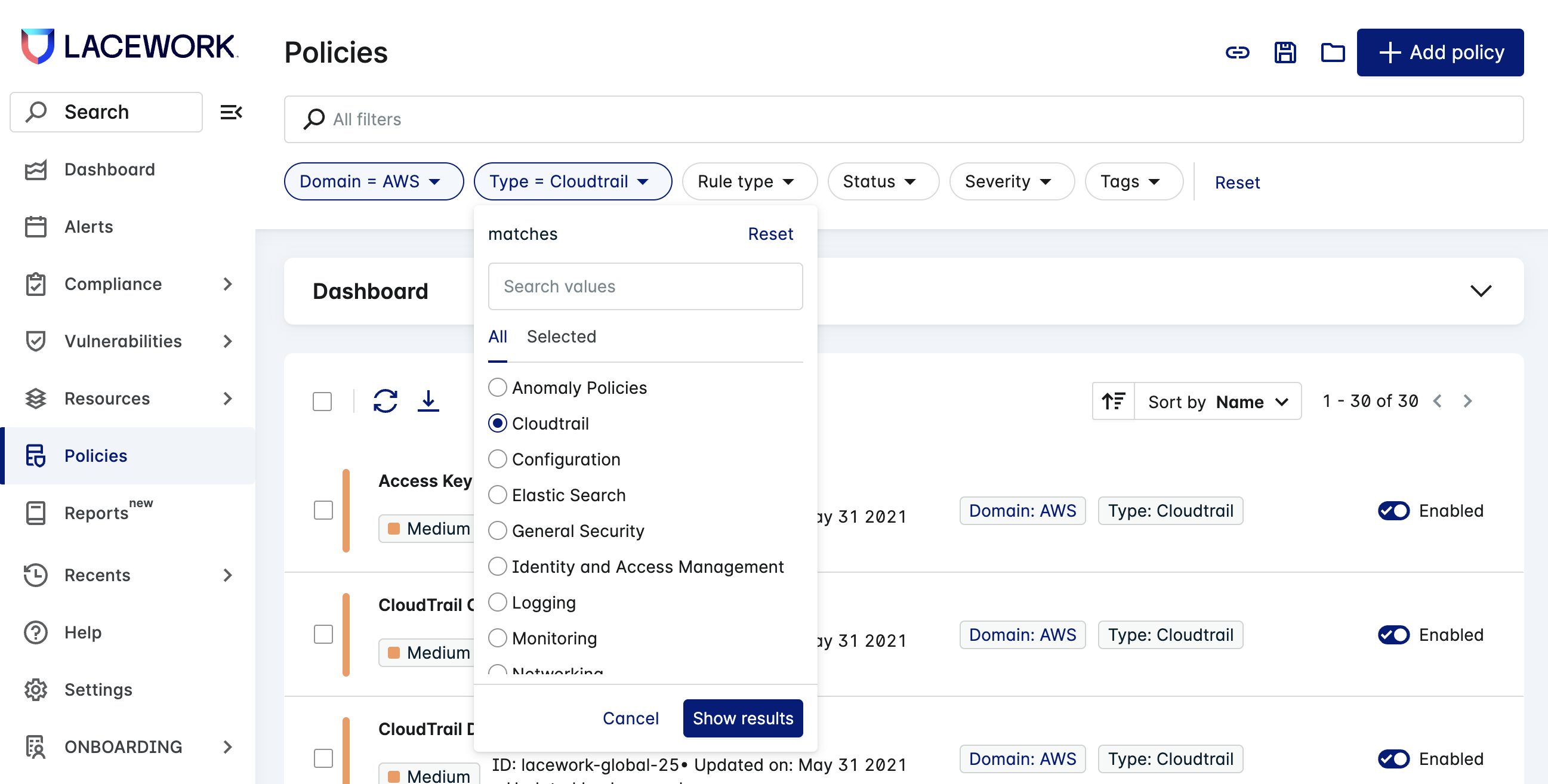
The rule types include these options:
- Default policies are built-in, Lacework provided policies.
- Custom policies are policies that you or others in your organization have created. For information on custom policies, see Create Policies.
- Legacy policies are policies that are obsolete or have been superseded. In general, you should move away from legacy policies over time.
Other filtering options include:
- Status: Whether a policy is enabled or disabled
- Severity: The severity level associated with the policy, such as critical, high, low, and so on.
- Tags: Descriptive tags associated with policies
After selecting filtering criteria, click Reset to return the list to its default.
Save and Share a View
At any time, you can share your current view by clicking the Copy link icon at the top right. You can send that link to others who will be able to view the same filtering selections.
After configuring filter options, you can save your view by clicking the Save view icon at the top right of the console. Access the view later through the Open view icon.
When you open a saved view, its name displays in the page title in the format Policies / view name. Click the icon adjacent to this name to access additional actions, such as duplicate or delete. Note that saved or shared views consist of your filtering options only, not search or sorting options.
Disable/Enable Policies
Disabling a policy excludes it from your assessment reports. To enable or disable policies from the Lacework Console:
Click Policies from the navigation menu.
Search for the name of the policy you want to disable or enable.
Find the policy and click the toggle button to disable or enable the policy.
You can also update multiple policies at once, as described in the following section.
Batch Update Policies
It can take some time to modify many policies individually. If you have many policies that you want to enable or disable at once, you can modify them as a batch. You can also download many policies at once in CSV format.
note
Vulnerability policies are not currently supported for batch enable/disable operations.
To enable or disable multiple policies at once, select the checkboxes next to each policy and click Enable/Disable. If the operation cannot be applied to any of the selected policies (for example, if a policy cannot be enabled), those policies are listed. You can confirm or cancel the operation as appropriate.
The batch update feature is most useful when used with search filters. By filtering the policy list first, you can quickly select and modify many policies with just a few clicks.
For example, to disable legacy AWS policies only, follow these steps:
In the Policies page, expand the Domain filter options, choose AWS and click Show results.
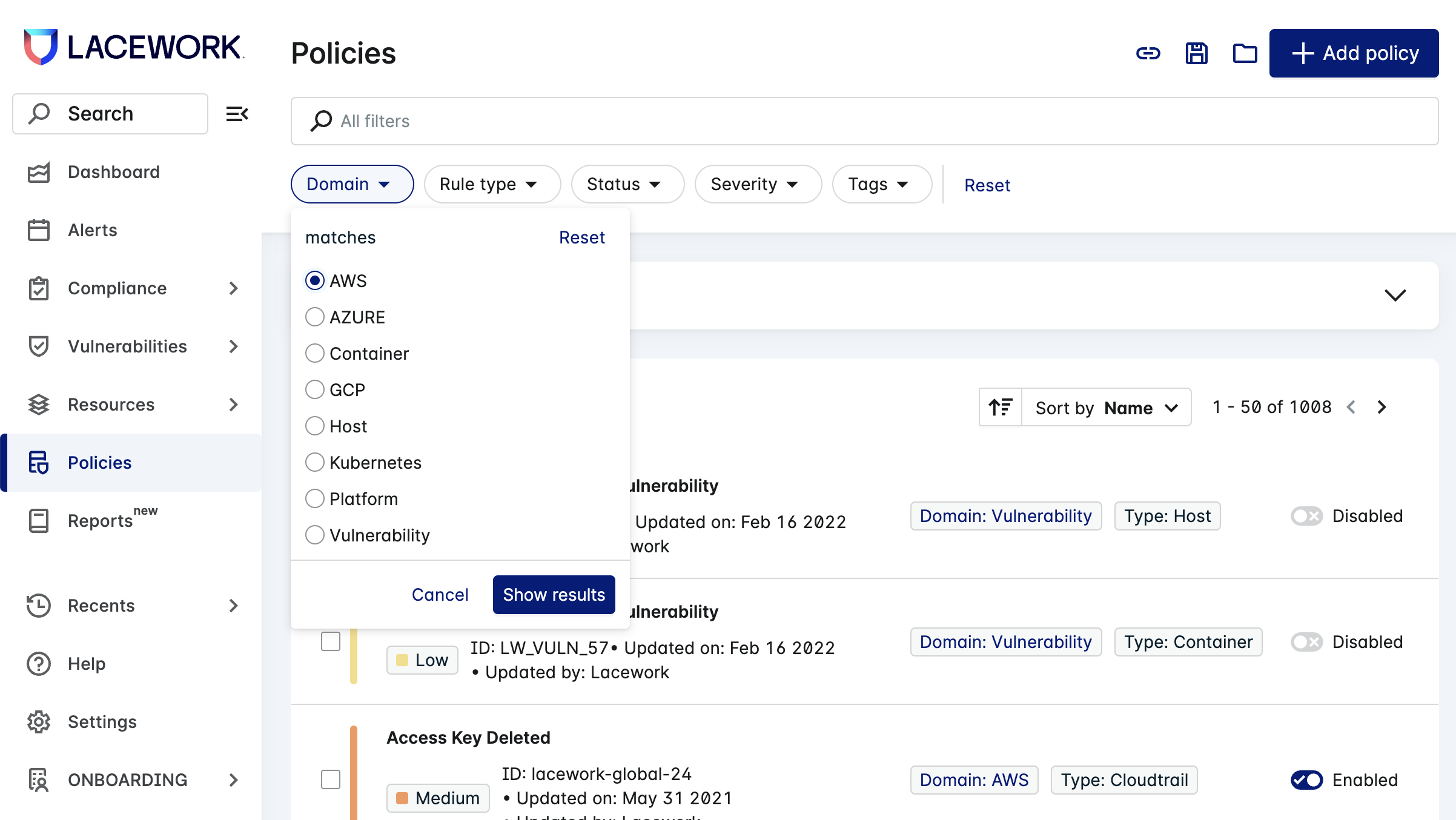
For the Rule type, choose Legacy and click Show results.
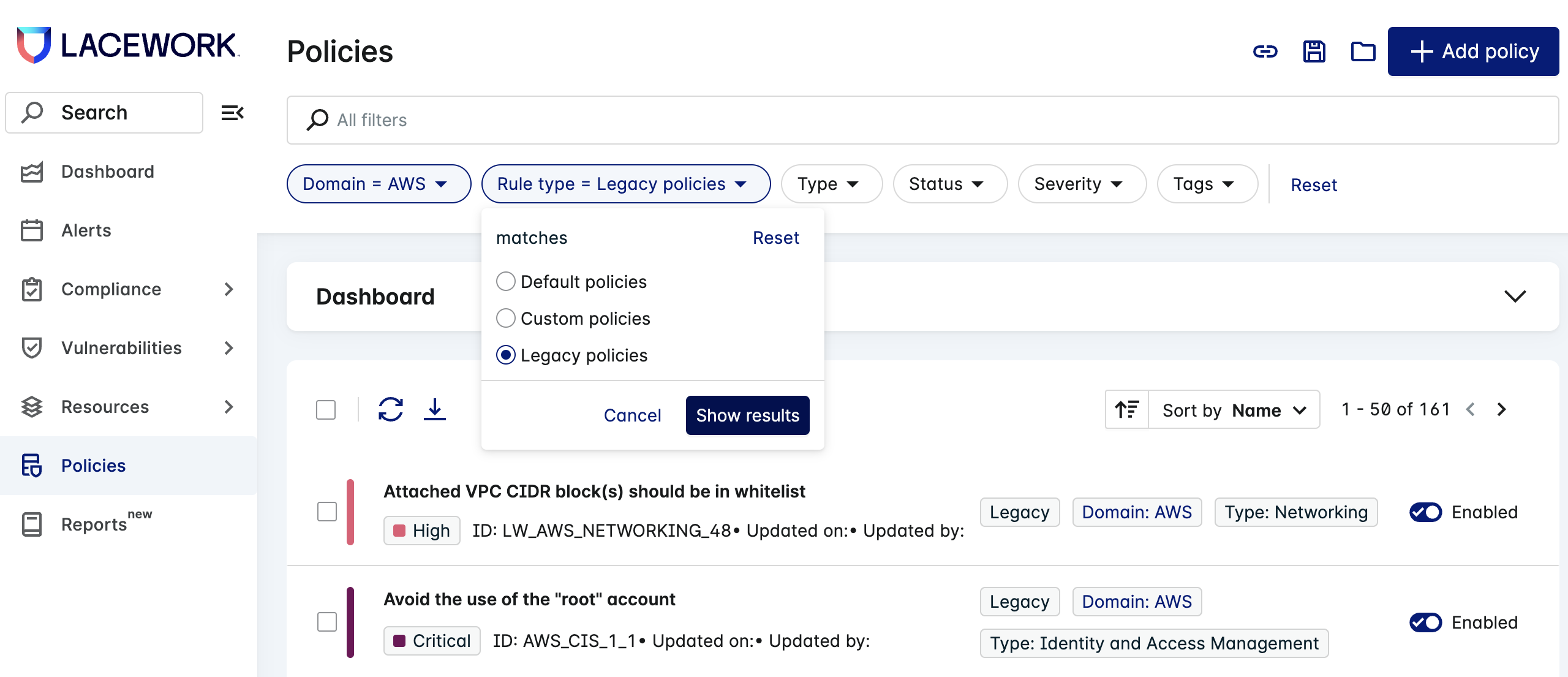
For the Status, choose Enabled. Notice that the policy list shows 50 policies of about 160.
You can choose the 50 policies that appear on the page using the multi-select checkbox, or click the down arrow next to the checkbox and choose Select all to select all 160.
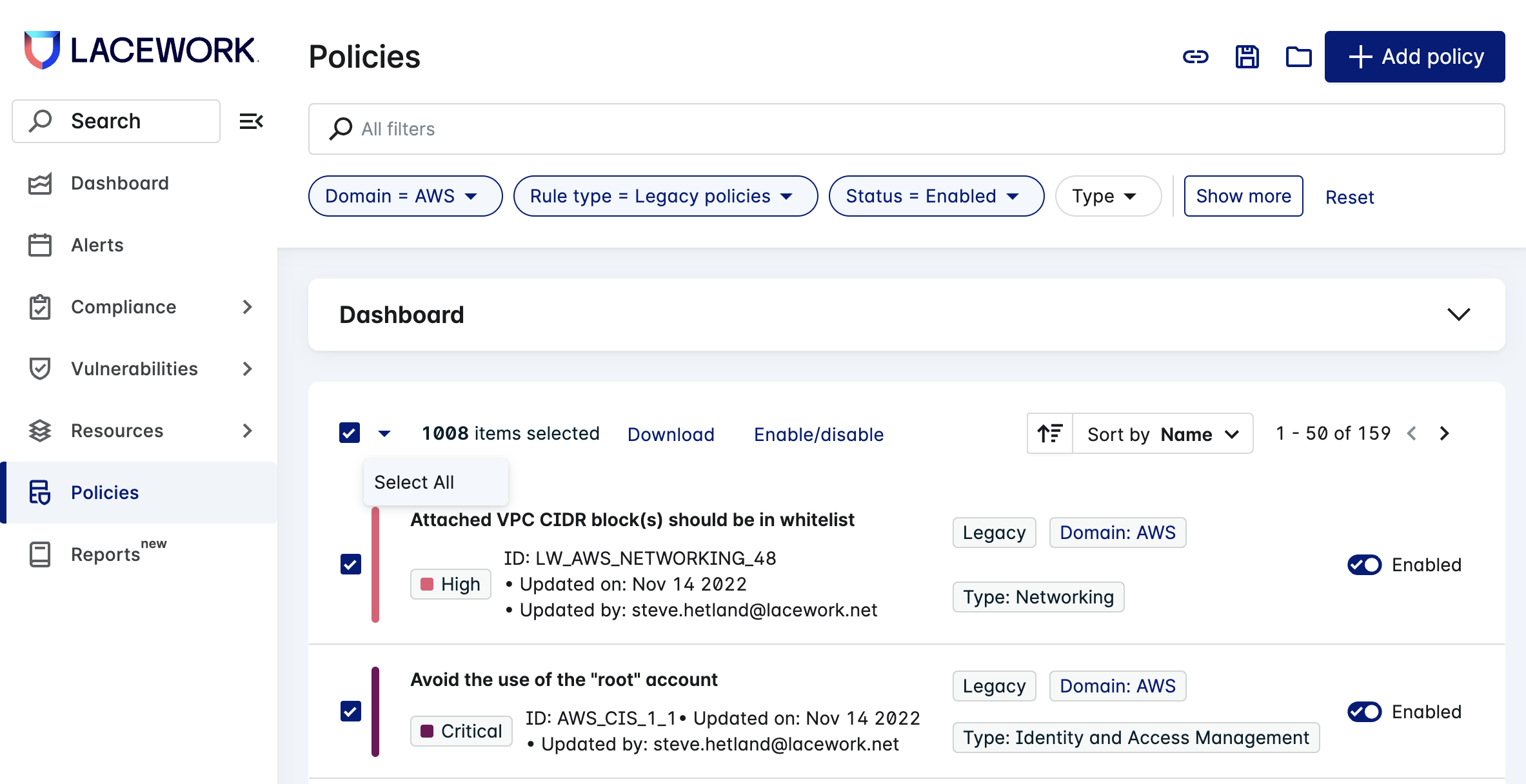
Click Enable/Disable.
Click Disable assessments for all n selected policies and Save changes in the following dialog:
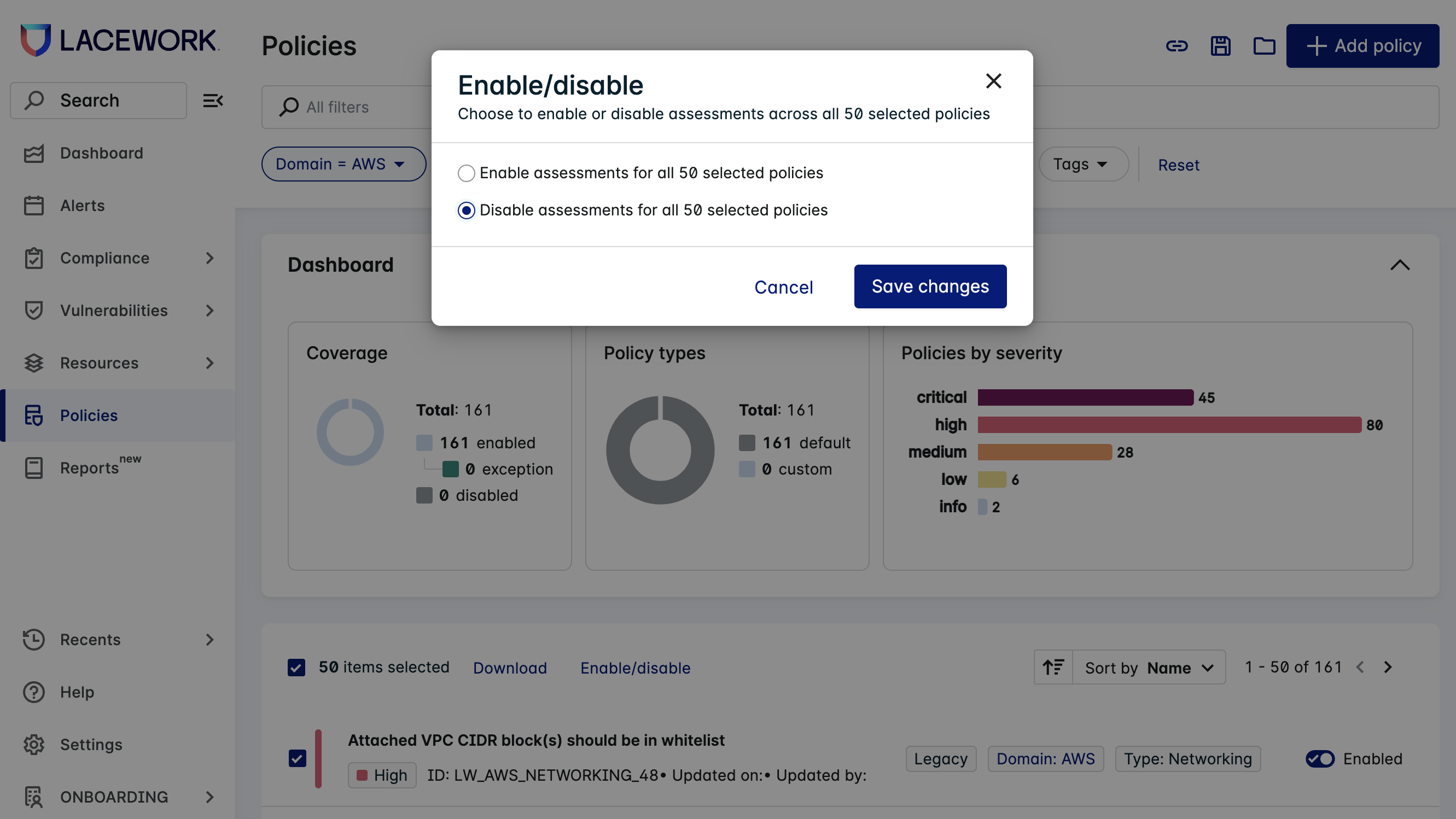
If you have selected any policies to which the operation cannot be applied, they are listed, giving you the option to cancel or proceed to apply the change to the remaining policies.
Policy Details
Click a policy to display its details. The policy's domain and type determine the available details.
Potential Summary tab information:
- The number of alerts in the past 7 days
- Description: Additional policy details
- Frequency: The frequency of assessment
- Severity: The severity of an event triggered by the policy
- Domain: The highest level policy category
- Type: A policy's subcategory
- Action on failure: The action to take when a policy failure occurs
- Scope: The registries associated with the container vulnerability policy
- Created by: The user who created the policy
- Updated on: The last date the policy was updated
- Updated by: The user who last updated the policy
Potential additional tabs:
- Query
- For Lacework Query Language (LQL) policies, the tab contains the entire LQL query.
- For non-LQL-based policies, the tab contains the expressions and result of the expressions.
- Exceptions
- For compliance policies, the tab contains fields to set exceptions.
- For vulnerability policies, the tab contains a link to the Vulnerability Exceptions page.
- Context: Remediation steps