Exposure Polygraph
Overview
The Exposure Polygraph provides attack path analysis for investigation by adding another layer of risk context. Each instance can have an Exposure Polygraph that illustrates risks such as known vulnerabilities on the affected host, compliance violations related to the involved instance, internet exposure, discovered secrets like SSH keys, and a visual cloud context showing the path from the internet through the internet gateway and security group to the instance. Lacework bundles all information in a single view to ensure responders can respond quickly and with full context.
Limitations
The Exposure Polygraph has the following limitations:
- Support for AWS only
- The Exposure Polygraph currently supports EC2-backed services (Native EC2, ECS, and EKS) as the target of the path
- Support for single-hop attack paths
- Special network ACLs are not considered
- IAM role currently lists only trust policies
View Internet Exposed Vulnerabilities
The Exposure Polygraph derives a value for internet exposure (yes, no, unknown) that determines if a host is exposed to the internet, and then makes this information available as a filter for host vulnerabilities and includes it as context for the host vulnerability risk score.
View Alerts with Exposure Polygraphs
Alerts that have hosts exposed to the internet have the Exposure Polygraph risk context. The Exposure tab displays details about host reachability, critical vulnerabilities, exposed secrets, misconfigurations, and more.
- Select Alerts.
- If the Internet Exposure filter is not visible, click Show more to display additional filters.
- For the Internet Exposure filter, select Yes and show the results refined to show only alerts associated with instances that are exposed to the internet.
- Click the desired alert and then the Exposure tab.
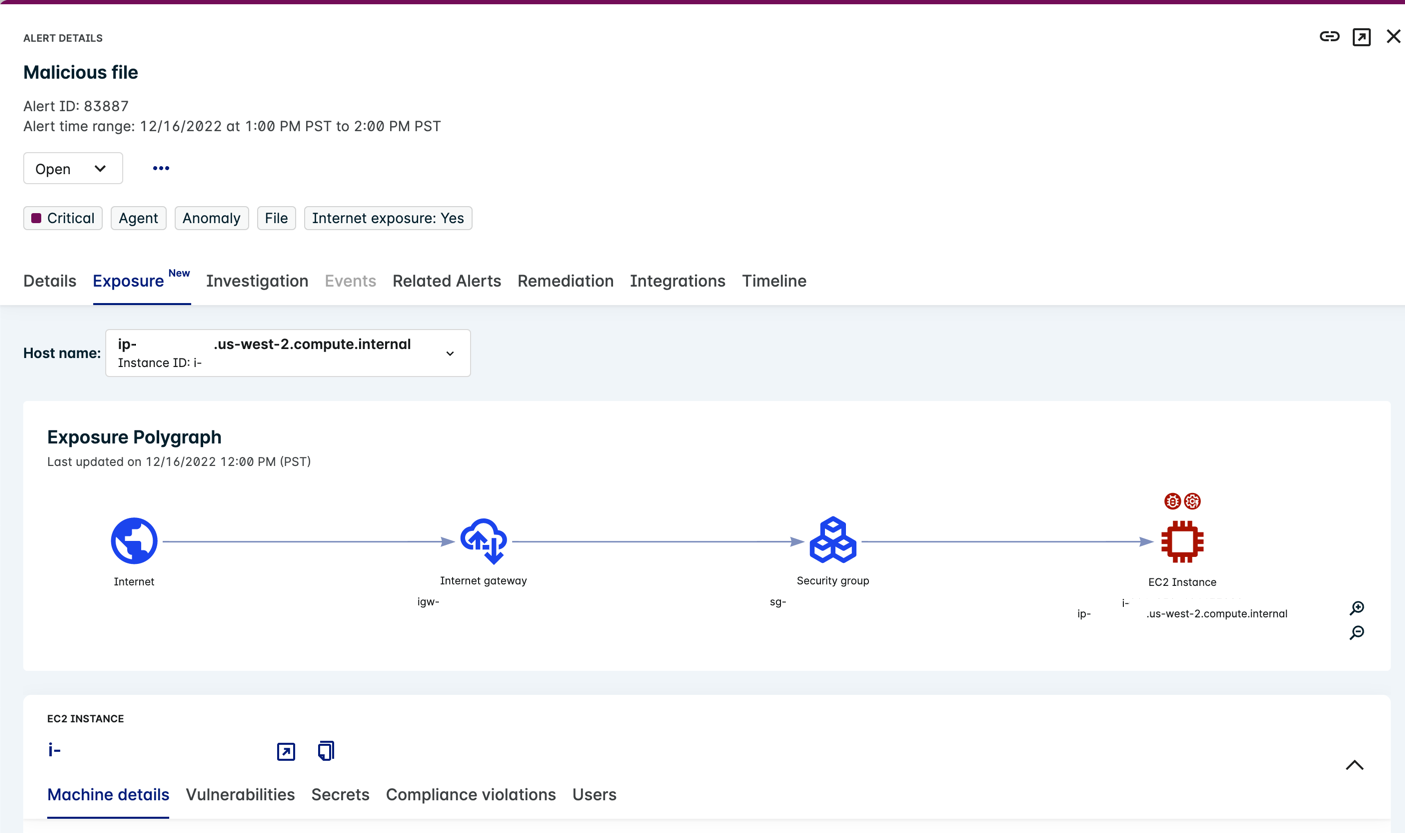
View Exposure Risk Context
When an alert is associated with multiple hosts and EC2 instances, you can search for and select a host/instance ID from the drop-down menu to view that instance's exposure information.
Exposure Polygraph
The Exposure Polygraph provides exposure analysis for the EC2 instance that is linked to the alert. The Exposure Polygraph visually displays the pathway from the internet through the internet gateway and security group to the EC2 instance. A timestamp indicates the time of the last update.
The Exposure Polygraph uses nodes to represent each step along the path. Badges depict the types of risks that make the path possible.

From the following risks in the Exposure Polygraph, you can see that if an attacker were to compromise this machine, they could leverage these coverage gaps to achieve privilege escalation or extend the compromise futher with lateral movement.
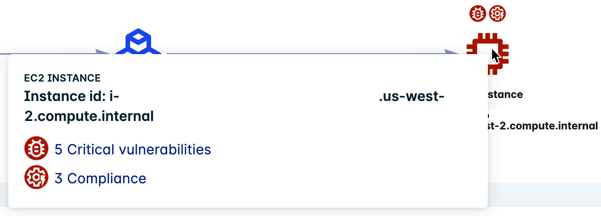
Hover over the EC2 node for additional information about the detected risks. Possible badges:
- Vulnerabilities
- Secrets
- SSH keys
- API keys
- Passwords
- Compliance/misconfiguration
When there isn't an Exposure Polygraph because Internet exposure = No or Unknown, but the host is part of an attack path, click View attack path to go to the Path investigation page.
EC2 Instance
This section provides tabs with the following contextualized information.
- Machine details - Separate tables for machine properties (hostname, IP address, and any associated vulnerabilities) and machine tag summary (tag name, tag value)
- Vulnerabilities - CVEs, severity, CVSS score, vulnerability impact score, and package name
- Secrets - Secret type (can be SSH key, API key, or password), identifier, file path, and number of connected resources
- Compliance violations - Failed policy, ID, status, and severity
- Users - Separate tables for user login activity, user authentication summary, and bad (failed) logins
Secrets Detection
note
Secrets detection is available only when agentless workload scanning (AWLS) integration is enabled.
Lacework logs details about any secret credentials and associated file metadata. The files are identified as secrets if they adhere to a common format (the format depends on the type of credential). The actual content of any secret credentials is not logged.
The table lists the types of credentials detected and example filesystem locations:
| Credential Type | Example Filesystem Locations |
|---|---|
| SSH private keys | /home/ec2-user/.ssh/id_rsa |
| AWS Access Key IDs (if a secret key is associated) | /home/ec2-user/.aws/credentials /root/.aws/credentials |
| GCP Service Account and User Credentials files | /etc/keys.json /home/user/.config/gcloud/keys.json |
| Kubernetes user tokens and certificate private keys | /root/.kube/config /home/user/.kube/config |
| Authorized Keys files | /home/user/.ssh/authorized_keys /root/.ssh/authorized_keys |
| Authentication log | /var/log/auth.log |
note
While the authorized_keys and auth.log files are not secrets, the data is used in combination with the detection of SSH private keys to determine whether keys are authorized and/or used on hosts.
Security Group
This section provides contextualized information related to security group configuration and CloudTrail logs. This provides full details for the security group to give additional context on exposed services. Separate tables for inbound and outbound rules contain the following information: type, protocol, port range, source, and description.
Load Balancer
This section provides contextualized information related to load balancer configuration and CloudTrail logs.