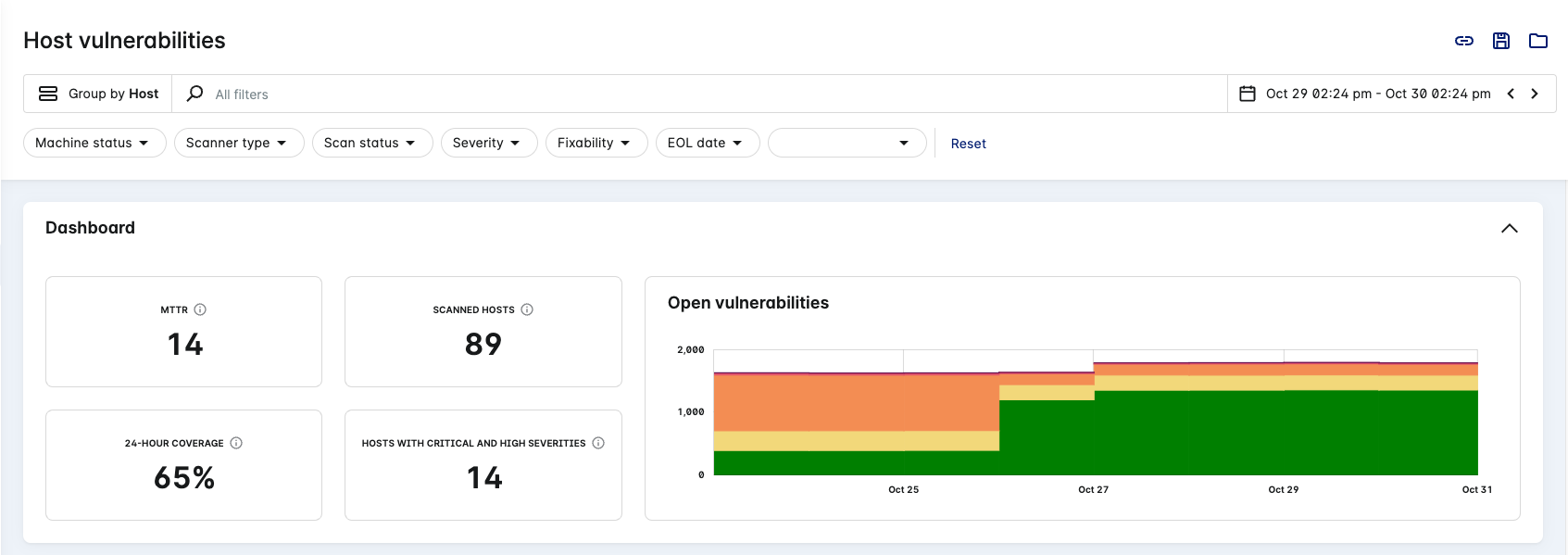
Lacework Console - Host Vulnerability
View Vulnerabilities
The host vulnerability page contains current vulnerabilities and previous vulnerabilities that were fixed. Select Vulnerabilities > Hosts in the Lacework Console to view this page.
note
AWS Fargate containers do not show on the host vulnerability page.
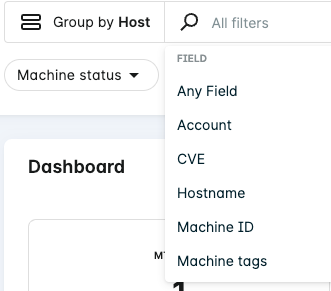
Groups
By default, the list displays vulnerabilities that are grouped by host and from the past day.
To change how the list groups vulnerabilities, select a different grouping from the drop-down:
- Host
- AMI ID
- Account
- Zone
- CVE
- Package Name
- Package Namespace
Search
Use the search function at the top of the page to find specific text in any of the details available on the page. You can also click the search field to select values and operators to filter your search (these vary depending on the Group by option).
Apply an operator that helps refine your search (these vary depending on the type of filter).
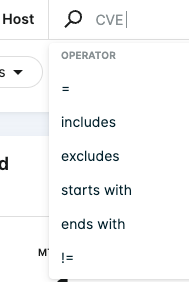
For example, when Group by Host is active, search for all hosts affected by a CVE matching ALAS2-2022-1780:
Package Name Search
When searching for package names on hosts, the results contain both vulnerable and non-vulnerable packages.
Filters
By default, the page is grouped by host and the following filters are active:
- Machine status = Online
- Scan status = Successful
- Severity = High or Critical
- Fixabilty = Yes
- Internet exposure = Yes or Unknown
- Package status = Active, Unknown, or N/A (Public Preview)
When switching to Group by CVE, the following filters are active by default:
- Vulnerability status = New, Unpatched, or Reopened
- Package status = Active, Unknown, or N/A (Public Preview)
You can use the following methods to refine the list of vulnerabilities displayed:
- Use filters to display a subset of specific vulnerabilities. Click the filter dropdowns along the top of the page, select your desired matches and then click Show results to make them active. To remove an active filter, deselect the checkbox in the corresponding filter dropdown and then click Show results. You can also click Reset in the filter dropdowns or in the row of filters to reset all filters. Or, click the filter icon and select the filters you want to display. EOL filters don't display at the top of the page by default.
- Use the search function at the top of the page to find specific text.
Fixability
tip
When grouped by Host, this filter functions as an AND operator when paired with one or more Severity levels.
For example, Fixability = Yes and Severity = Critical lists hosts with at least one CVE that is critical and fixable.
Group by Host fixable filter definitions:
- Yes - The hosts listed contain fixable packages for the vulnerabilities found.
- No - The hosts listed contain unfixable packages for the vulnerabilities found.
Group by CVE fixable filter definitions:
- Yes - The vulnerabilities listed are for fixable packages.
- No - The vulnerabilities listed are for unfixable packages.
Severity
tip
When grouped by Host, this filter functions as an AND operator when paired with one or more Fixability levels.
For example, Severity = Critical and Fixability = Yes lists hosts with at least one CVE that is critical and fixable.
- Group by Host: Display hosts that have vulnerabilities at the selected severity level (for example: Critical, High).
- Group by CVE: Display vulnerabilities (found in your environment) with the selected severity level (for example: Critical).
Machine Status
Lacework bases the machine status on the last hour’s Agent heartbeat. This lets you filter out ephemeral machines that are currently offline and helps you to understand fleet risk.
- Online - The Lacework Agent sent a heartbeat in the last hour.
- Offline - The Lacework Agent did not send a heartbeat in the last hour.
Scan Status
Group by Host scan status filter definitions:
- Successful Scan - Matches hosts that were successfully scanned.
- Failed Scan - Matches hosts that couldn't be scanned due to an error.
- Unsupported Scan - Matches hosts that couldn't be scanned due to running an unsupported operating system.
Scanner Type
Group by Host scanner type filter definitions:
- Agent - The vulnerability assessment data has been collected by a Lacework Agent installed on the host.
- Agentless - The vulnerability assessment data has been collected through an Agentless Workload Scanning integration.
EOL Date
Group by Host OS end of life (EOL) filter definitions:
- Currently EOL – Matches all hosts where the EOL date is in the past.
- EOL within 30 days – Matches all hosts where the EOL is within 30 days from now.
- EOL within 90 days – Matches all hosts where the EOL is within 90 days from now.
Internet Exposure
The vulnerability's internet exposure value is derived from the Exposure Polygraph / Attack Path Analysis feature.
Group by Host internet exposure filter definitons:
- Yes - Matches all hosts that have been determined as exposed to the internet during the latest Agentless or Agent scan.
- No - Matches all hosts that have been determined as not exposed to the internet during the latest Agentless or Agent scan.
- Unknown - Matches all hosts where the internet exposure status could not be determined.
Each host assessment contains tags for the internet exposure status and when the status was last updated. The internet exposure status depends on the last update in a given time range (including up to 24 hours prior to the start time).
note
Internet exposure deprecates the public facing filter.
Account
Filter for certain cloud accounts by using this Group by Host filter. Apply an operator (for example: matches) to help constrain your search.
CVE
Filter for certain vulnerability IDs (CVEs) by using this Group by Host filter. Apply an operator (for example: includes) to help constrain your search.
Hostname
Filter for certain hostnames by using this Group by Host filter. Apply an operator (for example: excludes) to help constrain your search.
Machine ID
Filter for certain machine IDs by using this Group by Host filter. Apply an operator (for example: does not match) to help constrain your search.
The Machine ID (or MID) is a Lacework generated identifier for the machine when it is first discovered.
Machine Tags
Filter for certain machine tags by using this Group by Host filter. Search for specific tag values or check the tags you want to display.
Machine tags are metadata associated with the host (for example: AWS Instance metadata).
Vulnerability Status
Group by CVE vulnerability status filter definitions:
- New - Vulnerability was detected for the first time during the last assessment.
- Unpatched - Vulnerability was detected and has been active longer than a day (since the last assessment).
- Fixed - Vulnerability was not detected in consecutive assessments.
- Reopened - Vulnerability was fixed, but has been detected again.
Package Status
info
This feature is in Preview as of Linux Agent v6.4.
Group by Host package status filter definitions:
- Active - The Lacework Agent on the host detected that a process accessed a file in the package (in the specified timeframe).
- Inactive - The Lacework Agent on the host did not detect any process accessing a file in the package (in the specified timeframe).
- Unknown - The host has a Lacework Agent installed, but package status detection is not enabled on the agent. Therefore, the package status cannot be determined.
- N/A - The host does not have a Lacework Agent installed, therefore, the package status cannot be determined.
Group by CVE (including Package Name/Namespace) package status filter definitions:
- Active - The Lacework Agent on at least one host detected that a process accessed a file in the vulnerable package (in the specified timeframe).
- Inactive - The Lacework Agents installed on all the hosts did not detect any process accessing a file in the vulnerable package (in the specified timeframe).
- Unknown - The hosts shown for this vulnerability have a Lacework Agent installed, but package status detection is not enabled on the agents. Therefore, the package status for this vulnerability cannot be determined on these hosts.
- N/A - The hosts shown do not have a Lacework Agent installed, therefore, the package status for this vulnerability cannot be determined on these hosts.
Additional information on Package status detection can be found in Host Vulnerability - FAQs.
note
The time range for a package status query should be at least 24 hours, see Host Vulnerability - FAQs for further explanation.
Kernel Status
Group by CVE kernel status filter definitions:
- Active Kernel - Vulnerability has been found on a kernel package for an active kernel.
- Inactive Kernel - Vulnerability has been found on a kernel package for an inactive kernel.
note
If the Kernel Status field value is empty, it indicates that Kernel Status field is not applicable because the vulnerability exists on a non-kernel package.
Package Name
Filter for package names by using this Group by CVE filter. Apply an operator (for example: starts with) to help constrain your search.
Package Namespace
Filter for package namespaces by using this Group by CVE filter. Apply an operator (for example: ends with) to help constrain your search.
Package Version
Filter for package versions by using this Group by CVE filter. Apply an operator (for example: matches) to help constrain your search.
Fixed Version
Filter for fixed versions (of packages) by using this Group by CVE filter. Apply an operator (for example: includes) to help constrain your search.
Time Range
To change the time period, select a different one from the drop-down or use the horizontal arrows to move to the next/previous period. Select from the following past periods: hour, day, three days, week, month, or a Custom range.
Only information found during assessment of the specified date range is reported.
Save View
When the page displays your required vulnerabilities, click the Save view icon in the top right corner to save the current view. You can access the saved view later through the Open view icon. When you open a saved view, its name displays in the page title as Host vulnerabilities/view name.
Click the icon adjacent to this name to access additional actions such as delete and duplicate. You can also copy the link to the current view by clicking the Copy link icon. You can then share the link with others so they can see the same view. You cannot save searches and sorting in views or copy them as links.
Statistics
The statistics depict data for the current view:
- MTTR = Mean Time to Resolve (MTTR) in days.
- Scanned hosts = Number of hosts that have been successfully scanned and evaluated.
- 24-hour coverage (percentage) = (Number of hosts successfully scanned for vulnerabilities / Number of hosts discovered through Agents, Agentless and Cloud integrations) x 100. This figure is based on the last 24 hours.
- Hosts with Critical and High Severities = Number of scanned hosts with critical and/or high severity vulnerabilities.
Charts
The page displays the following charts:
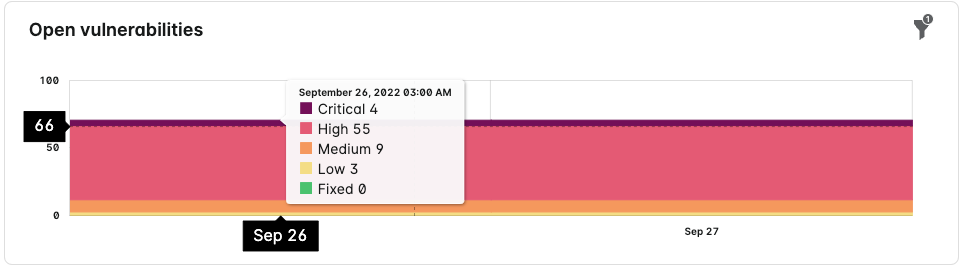
- An open vulnerabilities trend-line chart.
- Hover over the filter icon (
) to see the active filters that are influencing the chart.
- Hover over the filter icon (
- A severity chart for each hostname row.
- A severity detail chart under the CVE tab, which appears when you click a hostname.
- A sunburst chart for each CVE row.
- A CVE sunburst chart under the Hosts tab, which appears when you click a CVE.
Hover your mouse over the trend-line chart to see the critical, high, medium, and low vulnerabilities.
Vulnerabilities List
Below the overview is the vulnerabilities list. The information displayed depends on how the vulnerabilities are grouped.
The vulnerability list allows you to Refresh data, Download CSV, and sort.
Click a tag link to reload the vulnerability list with the tag as the filter.
Download CSV
note
Hosts with zero vulnerabilities are not listed in the CSV report.
There is a limit of 500,000 rows per report.
Click on the Download icon to generate a vulnerability report in CSV format.
The following options are available depending on which Group by option is selected:
- When grouped by CVE, the Download option (
) provides the Simplified CSV.
- When grouped by Host, choose from Simplified, Detailed, or Custom for your CSV report.
Once you have confirmed any additional options (such as for Custom CSV), click Start the download.
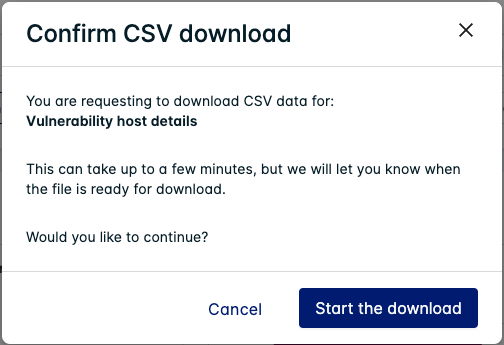
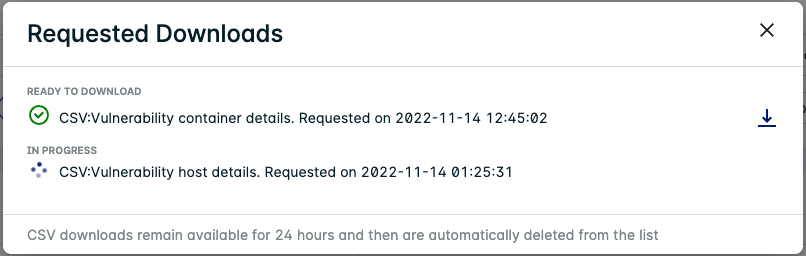
A popup appears once the report is ready to download. You can also view available and in-progress downloads on the Downloads page:
Some reports are compressed in Gzip format, you can decompress them using the following command:
gzip -d 'Host Vulnerabilities Simplified CSV.csv.gz'
Do not use tar as the format will be unrecognized.
Simplified CSV
Your active filters or tags control which Hosts or CVEs are listed in the CSV report.
Both types list when the last assessment was performed on the Host/CVE.
Group by Host: The CSV is indexed by Hostname and provides details about the host and a summary on the number vulnerabilities found (categorized into severity and fixability).
CSV Column Description MID The Machine ID for the host. LAST_EVAL_TIME The last time the host was evaluated for vulnerabilities. EVAL_GUID Lacework internal. EVAL_CTX Lacework internal. COLLECTOR_TYPE The Scanner Type for the host. HOST_NAME The hostname of the machine. EXTERNAL_IP The external IP of the host (if applicable). INTERNAL_IP The internal IP of the host. MACHINE_TAGS The Machine Tags of the host. ACCOUNT The cloud account identifier associated with the host. HOST_TYPE The Machine Status of the host. NUM_VULNERABILITIES Total number of vulnerabilities found on the host. NUM_FIXES Total number of fixable vulnerabilities found on the host. NUM_EXCEPTION Total number of vulnerability exceptions applied to the host. NUM_VULNERABILITIES_SEVERITY_1 Number of Critical vulnerabilities found on the host. NUM_VULNERABILITIES_SEVERITY_2 Number of High vulnerabilities found on the host. NUM_VULNERABILITIES_SEVERITY_3 Number of Medium vulnerabilities found on the host. NUM_VULNERABILITIES_SEVERITY_4 Number of Low vulnerabilities found on the host. NUM_VULNERABILITIES_SEVERITY_5 Number of Info vulnerabilities found on the host. NUM_VULNERABILITIES_FIX_SEVERITY_1 Number of Critical and Fixable vulnerabilities found on the host. NUM_VULNERABILITIES_FIX_SEVERITY_2 Number of High and Fixable vulnerabilities found on the host. NUM_VULNERABILITIES_FIX_SEVERITY_3 Number of Medium and Fixable vulnerabilities found on the host. NUM_VULNERABILITIES_FIX_SEVERITY_4 Number of Low and Fixable vulnerabilities found on the host. NUM_VULNERABILITIES_FIX_SEVERITY_5 Number of Info and Fixable vulnerabilities found on the host. NUM_VULNERABILITIES_EXCEPTION_SEVERITY_1 Number of Critical vulnerabilities found on the host that have an exception applied. NUM_VULNERABILITIES_EXCEPTION_SEVERITY_2 Number of High vulnerabilities found on the host that have an exception applied. NUM_VULNERABILITIES_EXCEPTION_SEVERITY_3 Number of Medium vulnerabilities found on the host that have an exception applied. NUM_VULNERABILITIES_EXCEPTION_SEVERITY_4 Number of Low vulnerabilities found on the host that have an exception applied. NUM_VULNERABILITIES_EXCEPTION_SEVERITY_5 Number of Info vulnerabilities found on the host that have an exception applied. NUM_VULNERABILITIES_EXCEPTION_FIX_SEVERITY_1 Number of Critical and Fixable vulnerabilities found on the host that have an exception applied. NUM_VULNERABILITIES_EXCEPTION_FIX_SEVERITY_2 Number of High and Fixable vulnerabilities found on the host that have an exception applied. NUM_VULNERABILITIES_EXCEPTION_FIX_SEVERITY_3 Number of Medium and Fixable vulnerabilities found on the host that have an exception applied. NUM_VULNERABILITIES_EXCEPTION_FIX_SEVERITY_4 Number of Low and Fixable vulnerabilities found on the host that have an exception applied. NUM_VULNERABILITIES_EXCEPTION_FIX_SEVERITY_5 Number of Info and Fixable vulnerabilities found on the host that have an exception applied. UP_TIME_MINS The uptime of the host in minutes. EVAL_STATUS Whether the host was successfully evaluated or not (equivalent to Scan Status). EVAL_MSG The reason for the evaluation failure on the host (if applicable). OS_NAMESPACE The operating system namespace in <os>:<version>format (for example:ubuntu:18.04).EOL_DATE The EOL Date for the operating system on the host. RISK_SCORE LW Risk Score for the host. RISK_INFO Lacework internal. PUBLIC_FACING Deprecated - see INTERNET_EXPOSURE. INTERNET_EXPOSURE Whether the host has been exposed to the internet or not. INTERNET_EXPOSURE_LAST_UPDATED The last time internet exposure was determined on the host. Group by CVE: The CSV is indexed by Vulnerability (CVE) ID and provides details on the vulnerability and affected package.
CSV Column Description Vulnerability ID The identifier for the vulnerability. PACKAGE Details about the vulnerability for the affected package. PACKAGE_TAGS Same as PACKAGE. LAST ASSESSMENT The time and date when the vulnerability was last found on an affected host during a scan. Impact Score LW Risk Score for the vulnerability.
Detailed CSV
note
The report always contains at least 3 days of data prior to the end time (unless the start time/date is older than 3 days).
Your active filters or tags control which Hosts or CVEs are listed in the CSV report.
The Detailed CSV is indexed by Machine ID (MID) and lists details on all the CVEs applicable to the Host in each row.
| CSV Column | Description |
|---|---|
| MID | The Machine ID for the host. |
| VULN_ID | The identifier for the vulnerability. |
| SEVERITY | The severity of the vulnerability. |
| STATUS | Status of the vulnerability: New - Vulnerability was detected for the first time during the last assessment. Active - Vulnerability was detected in consecutive assessments. Reopened - Vulnerability was fixed, but has been detected again. Fixed - Vulnerability was not detected in consecutive assessments. Exception - A vulnerability exception has been applied to this vulnerability, or the vulnerability was found on an inactive kernel. |
| FIX_AVAILABLE | Whether a fix is available for the vulnerability: "1" = Fix available. "0" = No fix available. |
| PACKAGE_NAME | The package name where the vulnerability was found. |
| PACKAGE_ACTIVE | The package status on the host: 1 = Active. 0 = Unknown. -1 = Inactive. -2 = N/A (No agent available). |
| VERSION_INSTALLED | The current version of the affected package. |
| FIXED_VERSION | The fixed version of the affected package. |
| ACCOUNT | The cloud account identifier associated with the host. |
| HOSTNAME | The internal hostname of the machine. |
| EXTERNAL_IP | The external IP of the host (if applicable). |
| INTERNET_EXPOSURE | Whether the host has been exposed to the internet or not. |
| MACHINE_TAGS | The Machine Tags of the host. |
| START_TIME | The start time of the latest scan of the host. |
| END_TIME | The end time of the latest scan of the host. |
Custom CSV
note
The report always contains at least 3 days of data prior to the end time (unless the start time/date is older than 3 days).
Define which type of CVEs are listed in the report by filtering for the Severity, Package status, Package name, Fixability, and/or CVE(s).
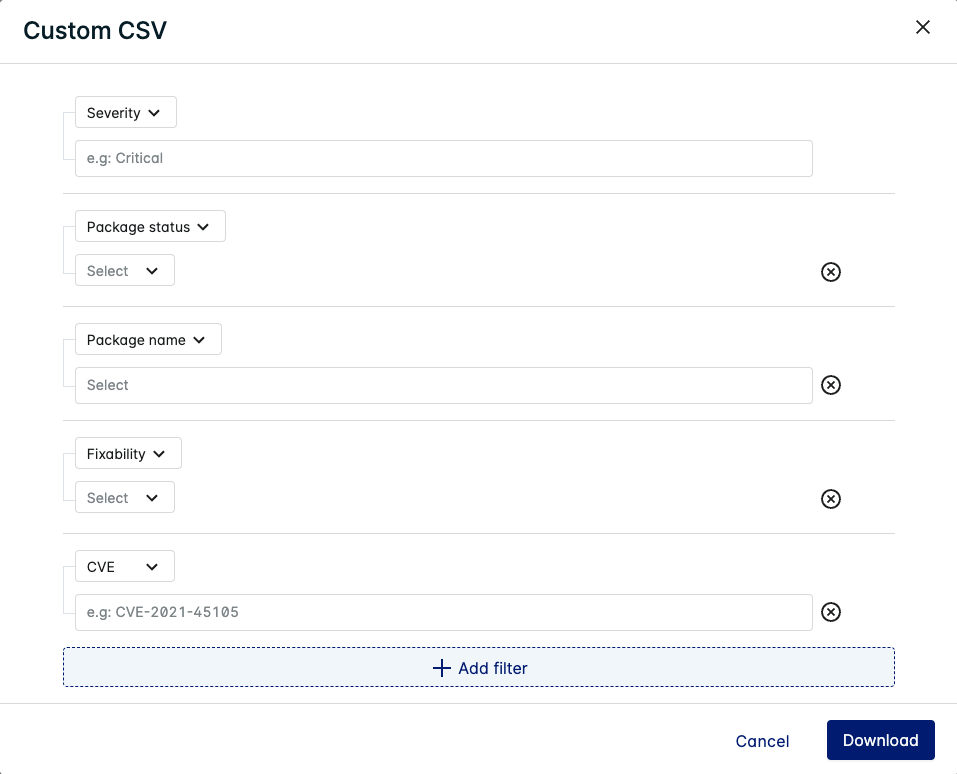
Click Download once you have specified your filters.
The Custom CSV is indexed by Machine ID (MID) and lists details on the CVEs applicable to the Host in each row (depending on which filters you have applied).
See Detailed CSV for information about the other columns used in the Custom CSV.
Group by Host
When grouped by Host, AMI ID, Account, or Zone, the list displays the following information:
- Hostname
- Uptime
- Host Risk
- Number of vulnerabilities
- Failure displays if the assessment failed. Potential reasons for failure include the following: host is unavailable, package data not found. For the reasons why package data may not be found, see Package Data Not Found.
- Unsupported displays if the host is running an unsupported operating system.
Host Assessment Drawer
Click a hostname to display its risk assessment where you can see an expandable view of host details and any vulnerabilities in the CVE tab (viewed in the table).
Host Assessment - Details
The Details tab contains descriptive information about the host. Click on any of the tags to filter the vulnerabilities list with that tag.
Host Assessment - CVE (default)
The CVE tab displays a list of vulnerabilities for the host with additional information in columns. This table lets you refresh data, download a report in CSV or PDF format, select which columns to display, filter, and search.
Click the filter icon to view the active filters on the table.
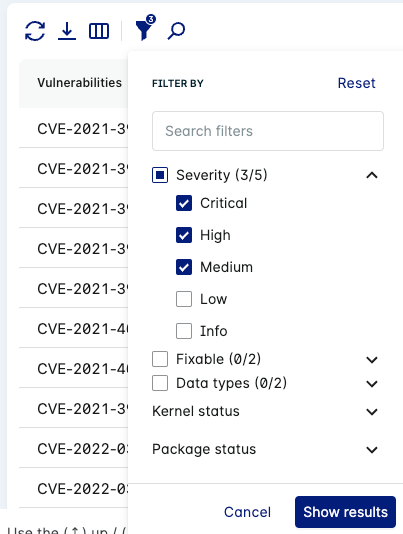
You can search for, add, and remove filters to adjust the list of vulnerabilities displayed in the table.
The available columns in the CVE tab are listed below:
| Column | Description |
|---|---|
| Vulnerabilities | Displays the common vulnerabilities and exposures (CVE) code assigned to this vulnerability by the CVE Numbering Authority. Click the More Info icon |
| Severity | Displays the CVE’s severity ranking, which is assigned by the vendor or computed from CVSS v3 or CVSS v2 scores (in that order of precedence). |
| CVSS Score | Displays the CVSS (Common Vulnerability Scoring System) severity rankings score for the vulnerability. Hover over the score for the CVSS version. For both CVSS v3 and CVSS v2, the severity ranking is a scale from 0 - 10, where 10 is the highest severity. Defaults to CVSS v3 scores or CVSS v2 if v3 scores are not available. |
| Vulnerability impact | Displays the Lacework risk score for the vulnerability. |
| Package Name | Displays the operating system package or language package that the vulnerability was found in. Click the package name to reload and filter the vulnerability list for this package. |
| Package Namespace | The namespace of the vulnerable package. |
| Current Version | Displays the current version of the package found on the host. |
| Fix Version | Displays the version of the package where the issue is fixed. |
| Package status | Displays active if there was an active process linked to this package. Only Agent assessments can determine whether a package is active or not. Agentless assessments will mark all packages as inactive. |
| Kernel Status | Displays Active if the vulnerability was found on a running kernel. See Kernel Status for other possible values. |
| File Path (hidden by default) | If applicable, displays the filesystem path to the vulnerable package source. |
| First Seen | When the vulnerability was first seen during a scan. |
| Last Status Update | Displays the last time the status of this package was updated in the Lacework Console. |
| Time to Resolve (hidden by default) | Displays how long it took for the vulnerability to be fixed. This is the time between when the vulnerability was First Seen and the Last Status Update. |
| Vulnerability Status (hidden by default) | Displays the status of the vulnerability. The status can be one of the following: New - Vulnerability was detected for the first time during the last assessment. Active - Vulnerability was detected in consecutive assessments. Reopened - Vulnerability was fixed, but has been detected again. Fixed - Vulnerability was not detected in consecutive assessments. Exception - A vulnerability exception has been applied to this vulnerability, or the vulnerability was found on an inactive kernel. |
Host Assessment - Packages
The Packages tab displays a list of vulnerable packages found on the host with additional information in columns. This table lets you refresh data, download CSV/PDF, add/remove columns, filter, and search.
Click the filter icon to view the active filters on the table. You can search for, add, and remove filters to adjust the list of packages displayed in the table.
note
If there is more than one vulnerability found on a package, use the dropdown icon to view each vulnerability found on that package.
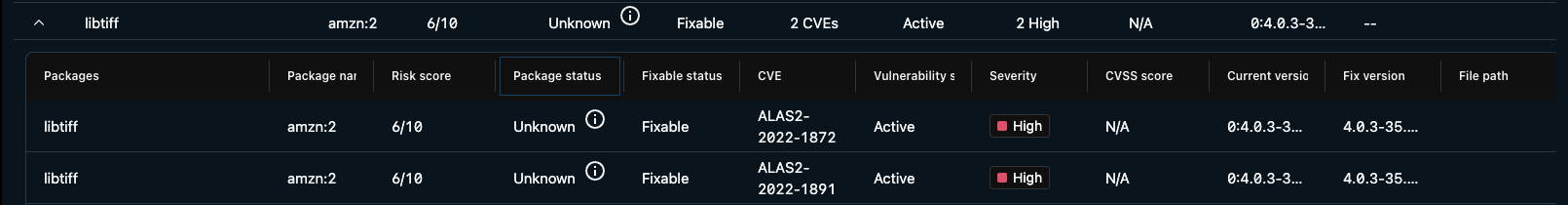
The available columns in the Packages tab are listed below:
| Column | Description |
|---|---|
| Packages | Displays the vulnerable operating system package or language package that was found on the host. |
| Package namespace | Displays the vulnerable package namespace that was found on the host. |
| Risk Score | Displays the Lacework risk score for the vulnerable package. |
| Package status | Displays active if there was an active process linked to this package. Only Agent assessments can determine whether a package is active or not. Agentless assessments will mark all packages as inactive. |
| Fixable Status | Displays whether the package is fixable or not (whether there is a new or patched version of the package available). |
| CVE | Displays the common vulnerabilities and exposures (CVE) code assigned to this vulnerability by the CVE Numbering Authority. |
| Vulnerability Status | Displays the status of the vulnerability. The status can be one of the following: New - Vulnerability was detected for the first time during the last assessment. Active - Vulnerability was detected in consecutive assessments. Reopened - Vulnerability was fixed, but has been detected again. Fixed - Vulnerability was not detected in consecutive assessments. Exception - A vulnerability exception has been applied to this vulnerability. |
| Severity | Displays the CVE’s severity ranking, which is assigned by the vendor or computed from CVSS v3 or CVSS v2 scores (in that order of precedence). |
| CVSS Score | Displays the CVSS (Common Vulnerability Scoring System) severity rankings score for the vulnerability. Hover over the score for the CVSS version. For both CVSS v3 and CVSS v2, the severity ranking is a scale from 0 - 10, where 10 is the highest severity. Defaults to CVSS v3 scores or CVSS v2 if v3 scores are not available. |
| Current Version | Displays the current version of the package found on the host. |
| Fix Version | Displays the version of the package where the issue is fixed (when a patch is available). |
| File Path | If applicable, displays the filesystem path to the vulnerable package source. |
Group by CVE
When grouped by CVE, Package Name, or Package Namespace, the list displays the following information:
- Vulnerability Impact / Package Risk
- Chart depicting hosts and their status
- Number of hosts impacted
- Number of hosts unimpacted
CVE Assessment Drawer
Click a vulnerability ID to display its risk assessment where you can see an expandable view of vulnerability details and affected or unaffected hosts (click the < icon to expand this view to full screen).
If there is a CVSS v3 score available for the vulnerability, additional information will be displayed that is derived from CVSS Metrics (such as Attack Vector, Access Complexity, etc).
CVE Assessment - Details
The Details tab contains descriptive information about the vulnerability.
CVE Assessment - Hosts
The Hosts tab displays a list of hosts where the vulnerability was found with additional information in columns. This table lets you refresh data, download as a CSV/PDF, select which columns to display, filter, and search.
The available columns in the Hosts tab are listed below:
| Column | Description |
|---|---|
| MACHINE ID (hidden by default) | Displays the Machine ID for the host. |
| Host | Displays the hostname for the machine. |
| Uptime | Displays the uptime for the machine. |
| Host Status | Displays the most recent agent status, either Online or Offline, based on the last hour’s agent heartbeat. Online means the Lacework agent sent a heartbeat the last hour. Offline means the Lacework agent did not send a heartbeat the last hour. |
| Host Risk | Displays the Lacework risk score for the host. A higher score indicates more risk/impact from discovered vulnerabilities. |
| Vulnerability Status | Displays the status of the vulnerability. The status can be one of the following: New - Vulnerability was detected for the first time during the last assessment. Active - Vulnerability was detected in consecutive assessments. Reopened - Vulnerability was fixed, but has been detected again. Fixed - Vulnerability was not detected in consecutive assessments. Exception - A vulnerability exception has been applied to this vulnerability. |
| Collector (hidden by default) | The Scanner Type used to perform the assessment. |
Package Data Not Found
Package data not found occurs under two circumstances:
- Package collection was intentionally disabled
- Package collection did not occur due to timing
If package collection was not disabled, then timing prevented package collection.
Scans do not occur on the host. An enumeration of packages is sent as a manifest to Lacework and any scanning activity occurs in the Lacework backend based on that host's manifest.
Package collection on a host does not occur immediately after the agent is installed. Package collection is delayed to limit the impact on host resources (CPU, Memory) and occurs after the core HIDS functionality is started. If the host shuts down after it registers with Lacework but before it transports package data, the package data will not be found.
You can use the /scan endpoint to supply a manifest (os, os_ver, package name, package version) and get a response. You can do this 20 times an hour for up to 1k packages each time. This action does not directly result in an assessment in the Lacework Console, but it does help to get an assessment.