Create a GCP Service Account and Grant Access
The following procedure provides steps to create a Service Account within Google Cloud Platform (GCP) to use in a Lacework integration.
Do not start with this topic.
For instructions on creating the entire integration, see the topics in GCP Terraform or GCP Console.
Recommendations
When integrating at the Organization level, Lacework recommends creating a Project specifically to contain Lacework resources.
When integrating at the Project level, you can provision all required resources for Lacework within the Project that is being integrated.
Prerequisites
The account that will be used to create and configure the integration resources must have certain privileges. Those privileges are mentioned in the following articles:
Additionally, the Project where the resources will reside must have billing enabled.
Steps
- Create a Service Account
- (Compliance Only) Create the Lacework Compliance Custom Role
- Grant the Required Roles to the Service Account
Create a Service Account
note
For more information, see Creating and managing Service Accounts.
Follow these steps to manually create a Service Account:
Log in to the GCP Console.
Navigate to IAM & Admin page, then click Service Accounts > + Create Service Account.
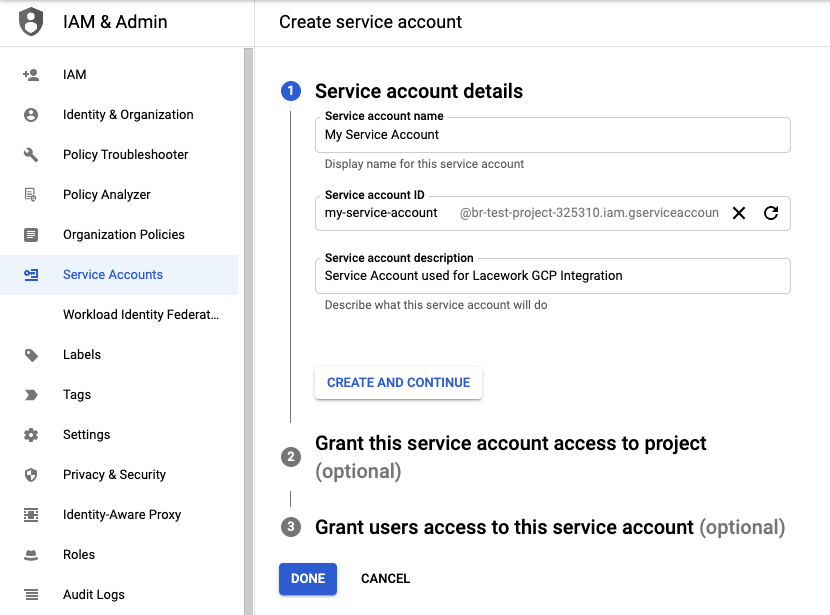
In the Service account details step, enter values in the fields, then click Create and Continue.
Skip the optional sections and click Done.
On the Services Accounts page, find the newly created service account, click the kebab menu under Actions, and then click Manage keys.
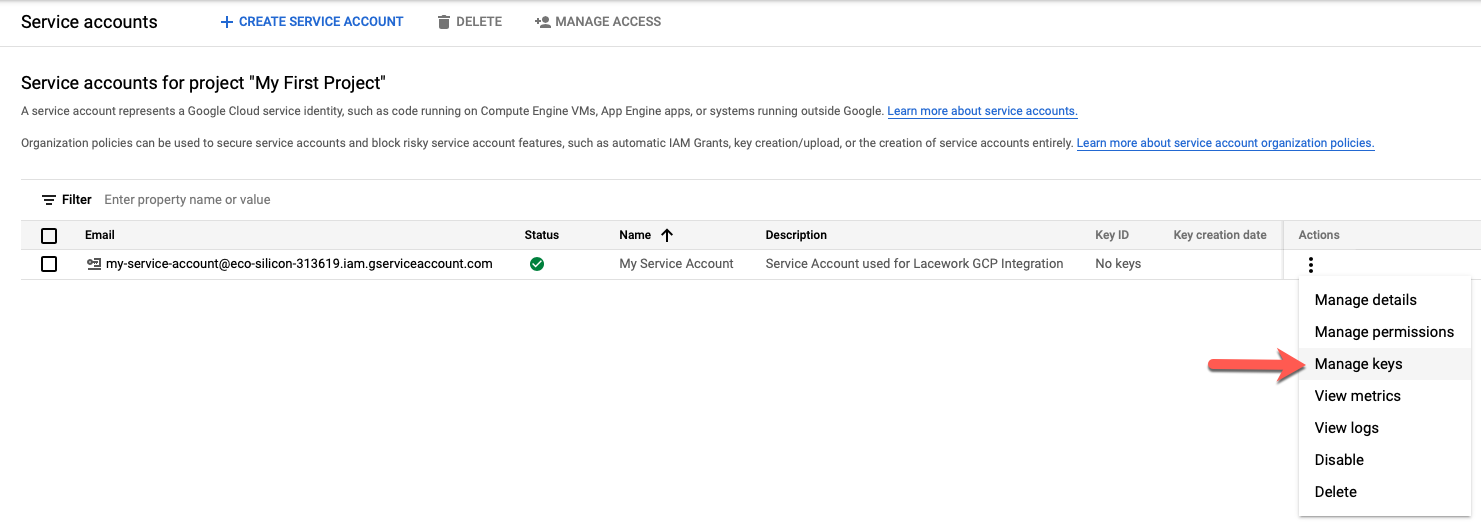
Click Add Key > Create new key.
Select the JSON key type, then click Create. A JSON key file downloads to your system.
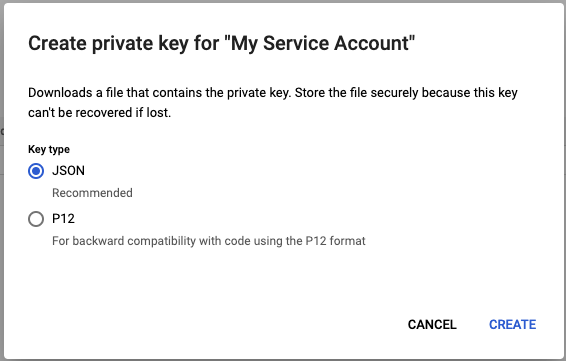
note
After you download the key file, you cannot download it again.
In the Details tab, find the email address of the new service account and copy it to your clipboard.
Click the menu icon located at the top right of the page to exit the Service Accounts page.
(Compliance Only) Create the Lacework Compliance Custom Role
info
This step is required only when creating a Lacework Compliance integration.
Select IAM & Admin > Roles from the cloud console navigation menu.
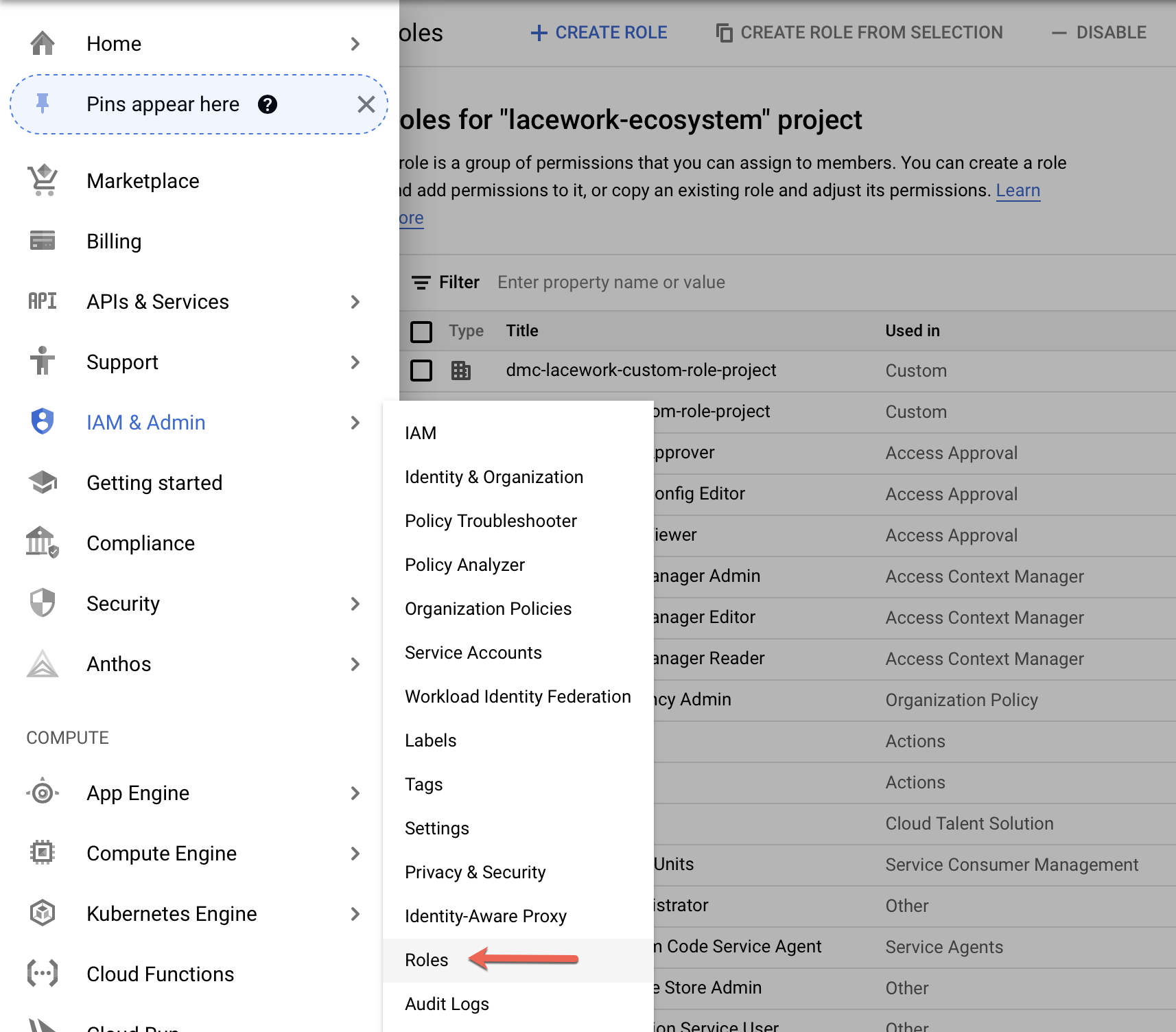
Click the down arrow in the top menu bar for the project.
The Select from dialog appears.
From the Select from drop-down, select an Organization that contains the GCP resources that you want the integration to monitor, or select
No Organizationif selecting a Project that does not reside within an Organization.
In the Select from dialog, click the All tab to display the list of all entities. Select the Organization or Project where the Custom Role shall be created, then click Open.
Click Create Role on the top toolbar.

In the Create Role page, enter a title, description, and account identifier to the fields. From the Role launch stage drop-down, select General Availability.
Lacework suggests naming similar to below.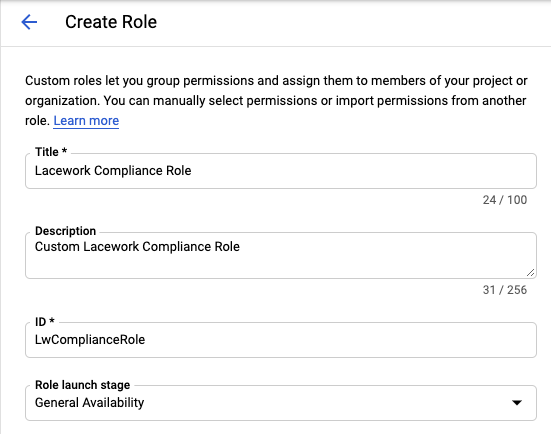
Add the required permissions by clicking + Add Permissions.
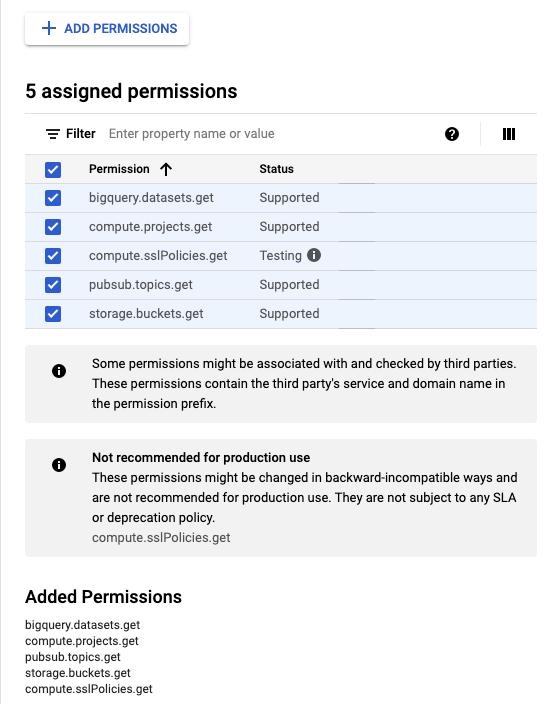
Click Create.
Grant the Required Roles to the Service Account
Grant the required Roles to the Service Account created in the previous section:
Select IAM & Admin > IAM from the cloud console navigation menu.
Click the down arrow in the top menu bar for the project.
The Select from dialog appears.
From the Select from drop-down, select an Organization that contains the GCP resources that you want the integration to monitor, or select
No Organizationif selecting a Project that does not reside within an Organization.
In the Select from dialog, click the All tab to display the list of all entities. Select the Organization or Project where the IAM Roles will be granted, then click Open.

Click Add.
note
You must have permission to add members to the Organization or Project IAM Policy for the Add button to be active.

Add a member and roles to a Project or Organization. In the New members field, paste the email address of the Service Account copied in an earlier step.
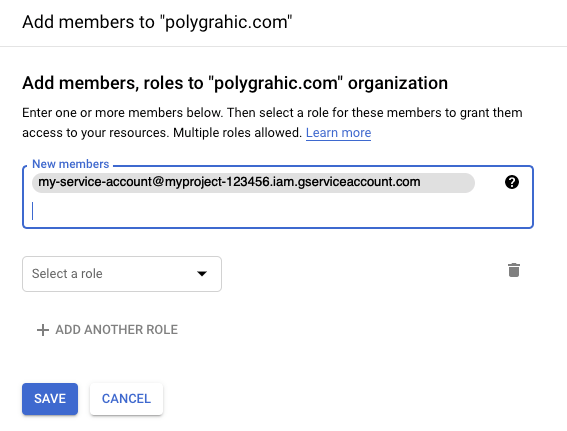
From the Select a role drop-down, select the appropriate roles depending on the integration type.
(Compliance Only): Add the Custom Role created from the Create the Lacework Compliance Custom Role section.
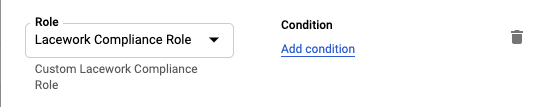
Click Save.
Service Account Roles
These are the specific Roles required by the Service Account being used for the integrations, depending on the integration level and type.
| Role Name | Role ID | Integration Type | Integration Level |
|---|---|---|---|
| Organization Viewer | roles/resourcemanager.organizationViewer | Audit Log Compliance | Organization level only. |
| Browser | roles/browser | Audit Log Compliance | Project or Organization level depending on the integration. |
| Cloud Asset Viewer | roles/cloudasset.viewer | Compliance | Project or Organization level depending on the integration. |
| Security Reviewer | roles/iam.securityReviewer | Compliance | Project or Organization level depending on the integration. |
| Lacework Compliance Custom Role | Role created in Create the Lacework Compliance Custom Role | Compliance | Project or Organization level depending on the integration. |
Lacework Compliance Role Permissions
In addition to the above GCP roles, Lacework also requires a Custom Role for the Compliance integration. The permissions required are outlined in the following table:
| Role Name | Permissions | Usage |
|---|---|---|
| Lacework Compliance Role | bigquery.datasets.get | Read access to retrieve dataset metadata, such as encryption keys and access permissions. |
compute.projects.get | Read access to project metadata, such as the resources contained within. | |
pubsub.topics.get | Read access to Pub/Sub topics metadata. | |
storage.buckets.get | Read access to bucket metadata, excluding IAM policies. Can also list or read Pub/Sub notification configurations on a bucket. | |
compute.sslPolicies.get | Read access to SSL Policy resources. |