Create and Manage Vulnerability Exceptions
Add Vulnerability Exceptions
Add exceptions in two different ways:
To add your exceptions on the Vulnerability Exceptions page (Vulnerabilities > Exceptions), click + Add exception at the top-right of the page.
Use the Container Vulnerability (Vulnerabilities > Containers) and Host Vulnerability (Vulnerabilities > Hosts) pages to create contextual exceptions. For example, when you click on a CVE ID (when Group by CVE is active) in the Vulnerabilities List, then click Add exception, the contextual exception is automatically filled with the resource scope and vulnerability criteria based on the details of the vulnerability selected.
Define an exception by providing the Resource scope, Vulnerability Criteria, and Context. Click Save (or Cancel) once you have completed all of these fields.
info
Wildcards are not supported when defining scope or criteria for vulnerability exceptions.
Scope and criteria entries are case-sensitive.
Resource scope
Define which resources will be affected by the exclusion. The types of resources change depending on whether the exception is for a Container or Host.
Click the + Add Criteria button to provide additional resource types to constrain the scope of the exception depending on your requirements. For example, after selecting the Container domain, restrict the exception to a tag in a specific registry by including both the Image Tag and Registry criteria.
Container
Select Container from the Domain list. This will alter the available resource types.
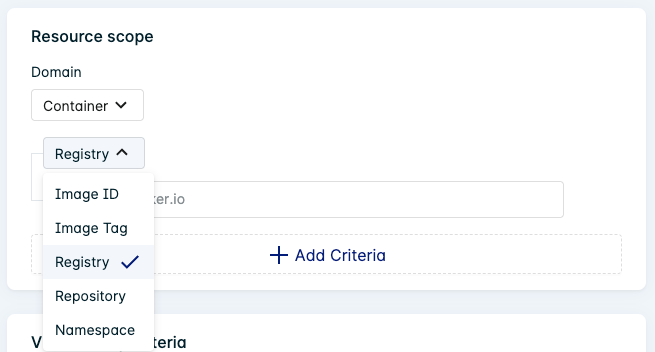
You can enter multiple values for each resource type. A description of each type is provided in the table below:
| Resource Type | Description | Example |
|---|---|---|
| Image ID | Enter the sha256 hash that was generated for the container image. | sha256:ex4ampl3 |
| Image Tag | Enter the container image tag. | 7.6 |
| Registry | Enter the container registry. | index.docker.io |
| Repository | Enter the container repository. | ecr_standard_images |
| Namespace | Enter the namespace for the package distribution (for example, an operating system or language package). | rhel:7 |
Host
Select Host from the Domain list. This will alter the available resource types.
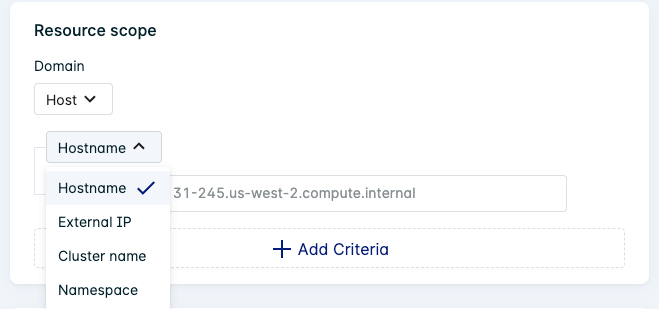
You can enter multiple values for each resource type. A description of each type is provided in the table below:
| Resource Type | Description | Example |
|---|---|---|
| Hostname | Enter the hostname for the machine. | ip-10-10-10-10.us-west-1.compute.internal |
| External IP | Enter the external IP address. | 101.102.103.104 |
| Cluster name | Enter the cluster name for the group of hosts. | PROD1 |
| Namespace | Enter the namespace for the package distribution (for example, an operating system or language package). | rhel:7 |
Vulnerability Criteria
Define the criteria of the vulnerability to be excluded. The criteria value changes depending on the type of criteria selected.
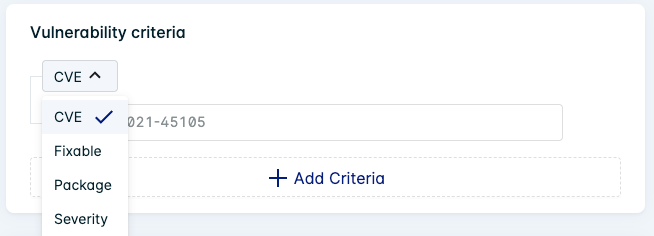
Click the + Add Criteria button to constrain the scope of the exception depending on your requirements. For example, restrict the exception to a non-fixable CVE by including both the CVE and Fixable=False criteria.
Each criteria option is described in the table below:
| Vulnerability Criteria | Description | Example |
|---|---|---|
| CVE | Enter the vulnerability (CVE) ID that you want to constrain the exception to. You can provide multiple IDs. | CVE-2021-2389 |
| Fixable | Select True or False to constrain the exception to a fixable or non-fixable vulnerability. | N/A |
| Package | Enter the package name (for example, an operating system or language package). This can include a version number. You can provide multiple package names. | commons-collections:commons-collections::3.2.1 |
| Severity | Select the severity of the vulnerability to constrain the exception to a Critical, High, Medium, Low, or Info vulnerability. You can provide multiple severity levels. | N/A |
Context
Define the context of the exception.
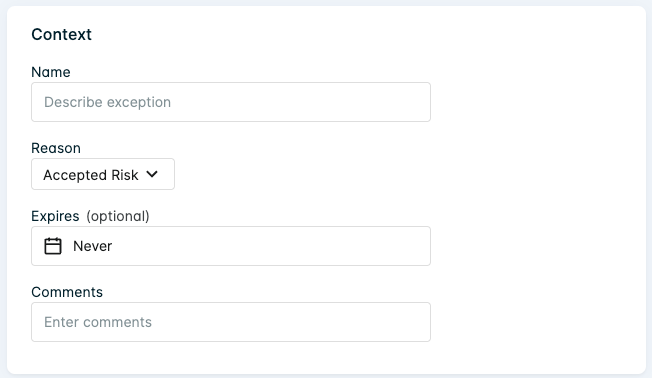
| Context | Description |
|---|---|
| Name | Provide a name for the exception. This will appear as the header for the exception when viewing the Exceptions list. |
| Reason | Select a reason for the exception from the list defined in Use Cases. You can also choose Other and provide a Comment. |
| Expires | Select an expiry date for the exception or leave it as Never. |
| Comment | Enter your own comments regarding the exception. |
Edit Vulnerability Exceptions
All exceptions can be edited in the Vulnerabilities > Exceptions page once they have been created.
Click to view an existing exception in the Exceptions list.
Click the Edit icons
to edit each field respectively.
Click Save (or Cancel) when done.
Delete Vulnerability Exceptions
Exceptions can be deleted in the Vulnerabilities > Exceptions page once they have been created.
Click to view an existing exception in the Exceptions list.
Click the Delete icon
to delete the exception.
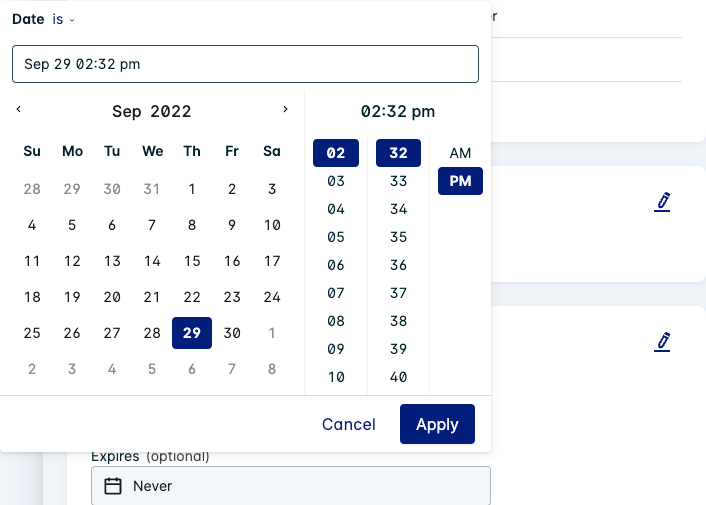
Disable an exception
Disable an exception (rather than deleting it) by changing the Expires date to the current date with a time set in the past. Then click Apply and Save.
For example, if today's date is 29th September 2022 2:32 PM, set the expiry date to 29th September 2022 2PM (or earlier).
Add Contextual Vulnerability Exceptions
Add contextual exceptions by clicking Add Exception when viewing any individual Host, Image, or CVE assessment. This can be done in both the Container and Host Vulnerability pages.
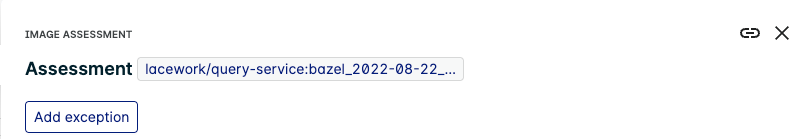
After clicking Add Exception, the exception form is filled in with the details based on the assessment viewed.
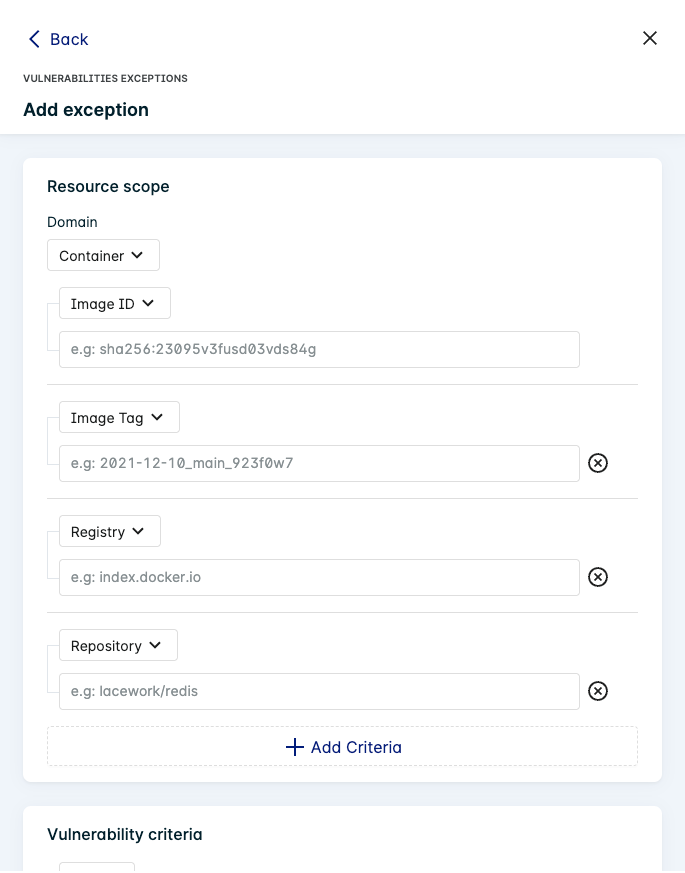
Add any additional criteria and the Context to complete the exception, then click Save.
You can also create contextual exceptions on the vulnerabilities list when filtering by certain groups.

When do changes to Vulnerability Exceptions become active?
When a vulnerability exception is added, changed, or deleted, the following timings apply:
- Platform, Proxy, and Inline Scanner: Changes to exceptions are active 5 minutes after the change is made.
- Container Assessment: If an exception change affects an active image, it will be reflected in the next continuous assessment.
- Host Assessment: The next daily re-evaluation will apply the changes to assessments on the respective online hosts.
Limit to Number of Vulnerability Exceptions
The total number of vulnerability exceptions that can exist in an environment is 100 for hosts and 150 for containers. This only includes active exceptions (expired/disabled exceptions are not counted).
You can delete or disable exceptions to reduce the number below the limit if urgent.
Contact Lacework Support if you want to discuss raising your vulnerability exception limits.
Create a Vulnerability Exception Using Terraform
For organizations using Terraform to manage their environments, Lacework maintains the Terraform Provider for Lacework which enables configuration of Lacework Vulnerability Exceptions using automation.
If you are new to the Lacework Terraform Provider, or Lacework Terraform Modules, read the Terraform for Lacework Overview to learn the basics on how to configure the provider, and more.
resource "lacework_vulnerability_exception_host" "example" {
name = "My Vuln Exception"
description = "This is a vulnerability host exception"
enabled = true
reason = "Accepted Risk"
vulnerability_criteria {
severities = ["critical"]
cves = ["cve-2021-11111", "cve-2021-22222"]
fixable = true
package {
name = "myPackage"
version = "1.0.0"
}
package {
name = "myOtherPackage"
version = "1.0.0"
}
}
resource_scope {
hostnames = ["host1", "host2"]
cluster_names = ["cluster1", "cluster2"]
namespaces = ["namespace1", "namespace2"]
}
}
resource "lacework_vulnerability_exception_container" "example" {
name = "My Vuln Exception"
description = "This is a vulnerability container exception"
enabled = true
reason = "Accepted Risk"
vulnerability_criteria {
severities = ["Critical", "High"]
cves = ["cve-2021-11111", "cve-2021-22222"]
fixable = true
package {
name = "myPackage"
version = "1.0.0"
}
package {
name = "myOtherPackage"
version = "1.0.0"
}
}
resource_scope {
image_ids = ["sha256:3b83d9104a4c4ccf76433756f14a2ad109e2aae15444b63339"]
image_tags = ["4.0", "1.0", "3.1", "5.0"]
namespaces = ["debian"]
registries = ["index.docker.io"]
repositories = ["lacework/lacework-cli"]
}
}
Additional information on the lacework_vulnerability_exception_host and lacework_vulnerability_exception_container resources can be found on the Terraform Registry.