Integrate the Lacework Inline Scanner with CI Pipelines
Overview
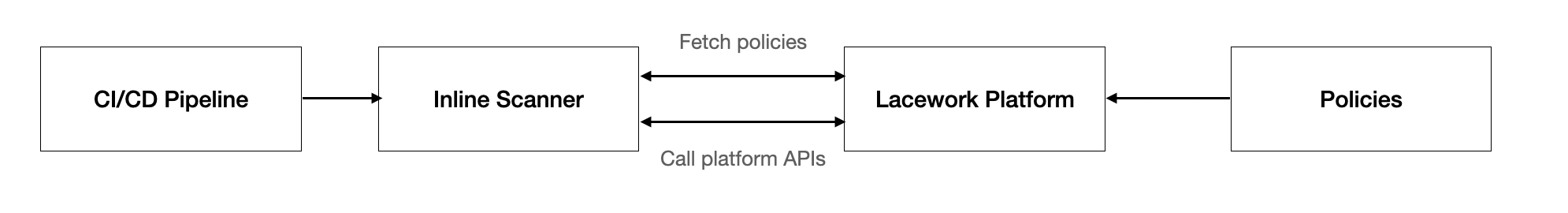
The Lacework inline scanner supports integration with Continuous Integration (CI) tooling to scan container images as part of the build process.
The Lacework inline scanner is written in Go and runs on Linux, macOS and Windows. For more information on installing and configuring the Lacework inline scanner, see Integrate Inline Scanner.
You can track your Continuous Integration runs by adding the build ID or build plan to your assessment reports:
lw-scanner image evaluate debian 10 --build-id YOUR_BUILD_ID --build-plan YOUR_BUILD_PLAN
You can find the build id and build plan values as Environment tags in the Lacework Console.
Upgrades
When installing a new version of the inline scanner, be aware of the following:
Existing configuration will not be overwritten, including environment variables. As such, any new default behavior will not become active unless you explicitly configure it after upgrading.
For example, from v0.2.4 onwards, language libraries are scanned by default. If this feature was previously disabled in your configuration, it will remain disabled. Use the LW_SCANNER_DISABLE_LIBRARY_PACKAGES_SCANNING=false environment variable to enable it.
Deleting Existing Configuration (Optional)
If you wish to install a new version of the inline scanner and remove any previous configuration, use the configure reset command before installing.
Saving Evaluation Results to Lacework Console
After upgrading the Lacework scanner from 0.1.x to 0.2, the inline scanner no longer saves evaluation results to the Lacework Console by default.
To keep the same behavior as before, perform one of the following options:
- Run the
configure datacommand and entertrueforSave results in platform. - Use the
LW_SCANNER_SAVE_RESULTS=trueenvironment variable on your local or CI/CD system. - Use the
--saveflag when running theimage evaluateorimage scancommands.
Support for Proxy Server
The Lacework inline scanner needs to communicate with the Lacework SaaS to evaluate images. The communication can be done via a proxy server. The scanner follows the HTTP_PROXY and HTTPS_PROXY environment variables if set in your Continuous Integration system.
Support for Language Library Packages
This feature is enabled by default. Find out more about this feature in the Language Libraries Support section.
note
Prior to v0.2.4, inline scanner releases do not have this feature enabled by default.
Disable Language Library Scanning
To disable scanning of language libraries, use the following environment variable or command flag (with image evaluate) in your CI/CD system:
LW_SCANNER_DISABLE_LIBRARY_PACKAGES_SCANNING=true
--disable-library-package-scanning
Sample Container Vulnerability Data from the Lacework Inline Scanner
Data returned from the Lacework inline scanner provides a wealth of information about vulnerabilities found in images, their severity, and what is fixable. The Lacework inline scanner is designed for individuals or teams responsible for tracking and remediating vulnerabilities. It provides relevant data to help with prioritization through the ability to sort assessments by what is actively running in the environment and by filtering vulnerabilities that have fixes.
The following example is the human-readable output of a container vulnerability assessment with 20 vulnerabilities from which only one of the vulnerabilities could be fixed.
lw-scanner-darwin-amd64 image evaluate debian 10 --fixable
CONTAINER IMAGE DETAILS VULNERABILITIES
------------------------------------------------------------------------------------------+---------------------------------
ID sha256:4a7a1f4017349067a21bd2de060dcf8b41e49fabf61b0dc3cf86a87e1f6dba9d SEVERITY COUNT FIXABLE
Digest sha256:acf7795dc91df17e10effee064bd229580a9c34213b4dba578d64768af5d8c51 -----------+-------+----------
Registry remote_scanner Critical 0 0
Repository debian High 3 1
Size 108.8 MB Medium 9 0
Created At 2021-05-12T01:21:03.936Z Low 13 0
Tags 10 Info 39 0
CVE ID SEVERITY PACKAGE CURRENT VERSION FIX VERSION INTRODUCED IN LAYER
----------------+----------+---------+-----------------+-----------------+------------------------------------------------------------------------
CVE-2021-3520 High lz4 1.8.3-1 1.8.3-1+deb10u1 ADD
file:1a1eae7a82c66d673971436ce2605e97d107e2934b7cdec876c64923ae6f4f85
in /
----------------+----------+---------+-----------------+-----------------+------------------------------------------------------------------------
info
You can switch the output of the inline scanner command to JSON format with the flag -v=false. You can also use the --html flag to generate a report in HTML format.
Configuration Options
The CI system examples use the image evaluate command to provide a human-readable output of container vulnerabilities. You can also use image scan command depending on your requirements.
Add additional flags to these command to suit your needs, see Image Evaluate Command and Image Scan Command for details about each flag.
Configuration using Environment Variables
Alternatively to command flags, set environment variables on your CI/CD system. The following table displays the available environment variables:
| Variable Name | Value | Default |
|---|---|---|
| LW_ACCOUNT_NAME (*) | Your Lacework account name. Examples: If your login URL is 'mycompany.lacework.net', the account name is mycompany.If your login URL is 'mycompany.fra.lacework.net', the account name is mycompany.fra. | N/A |
| LW_ACCESS_TOKEN (*) | Authorization token. Copy and paste the token from the inline scanner integration created in the Lacework Console. | N/A |
| LW_SCANNER_SAVE_RESULTS | When set to true, this will save evaluation results to the Lacework Console. This is not available for image scan. | false |
| LW_SCANNER_DISABLE_LIBRARY_PACKAGES_SCANNING | When set to true, this will disable image evaluations for non-OS library packages. | false |
| LW_SCANNER_DISABLE_UPDATES | When set to true, this will disable the update prompt at the end of the output if there is a new version of the Lacework scanner available. | false |
(*) = required variable.
See also Global Flags using Environment Variables.
info
The Lacework scanner will honor the standard Linux HTTP_PROXY and HTTPS_PROXY environment variables if they are set in your CI system.
Integrate with CI systems
The following are examples of integrating the Lacework inline scanner command into a few popular CI systems:
- Integrate with Jenkins
- Integrate with Azure DevOps
- Integrate with TravisCI
- Integrate with GitHub Actions
- Integrate with Gitlab
- Integrate with Bitbucket Pipelines
- Integrate with AWS CodeBuild
- Integrate with Circle CI
Integrate with Jenkins
The following is an example of Jenkins pipeline using Docker to pull an image and the Lacework inline scanner to evaluate the image.
You can use the executable or the Docker container. See Docker Image for Inline Scanner.
This simple Jenkins pipeline takes IMAGE_NAME, IMAGE_TAG, and BUILD_ID as inputs.
Every Jenkins slave that executes this pipeline must have the following installed:
- curl
- docker cli
Add the following variables to your Jenkins Credentials as Secret Text:
- LW_ACCESS_TOKEN: See Integrate Inline Scanner to get your access token.
- LW_ACCOUNT_NAME
pipeline {
agent any
environment {
LW_ACCESS_TOKEN = credentials('LW_ACCESS_TOKEN')
LW_ACCOUNT_NAME = credentials('LW_ACCOUNT_NAME')
}
parameters {
string (name: 'IMAGE_NAME',
description: "Specify Image Name",
defaultValue: '')
string (name: 'IMAGE_TAG',
description: "Specify Image Tag",
defaultValue: '')
}
stages {
stage('Pull') {
steps {
echo 'Pulling image ...'
sh "docker pull ${IMAGE_NAME}:${IMAGE_TAG}" //Pull the image to scan
}
}
stage('Scan') {
steps {
echo 'Scanning image ...'
sh "curl -L https://github.com/lacework/lacework-vulnerability-scanner/releases/latest/download/lw-scanner-linux-amd64 -o lw-scanner"
sh "chmod +x lw-scanner"
sh "./lw-scanner image evaluate ${IMAGE_NAME} ${IMAGE_TAG} --build-id ${BUILD_ID}"
}
}
}
}
Optionally, you can implement the exit codes to prevent container images from being deployed due to a policy violation, see Exit codes for Policy Violations
You need to create container vulnerability policies before implementing the exit codes. To create vulnerability policies, see Vulnerability Policy Management
For more details on integrating Lacework with Jenkins, see the blog post Up and Running with Lacework and Jenkins.
Integrate with Azure DevOps
This sample azure-pipelines.yml file demonstrates building a sample image azure.devops/app:latest and scanning it with Lacework:
trigger:
- up_and_running
pool:
vmImage: 'ubuntu-latest'
steps:
- script: |
docker build -t azure.devops/app:latest .
displayName: 'Build a docker image'
- script: |
apt-get update
apt-get -y install curl
curl -L https://github.com/lacework/lacework-vulnerability-scanner/releases/latest/download/lw-scanner-linux-amd64 -o lw-scanner
chmod u+x lw-scanner
./lw-scanner image evaluate azure.devops/app latest
displayName: 'Scan the image'
env:
LW_ACCESS_TOKEN: $(LW_ACCESS_TOKEN)
LW_ACCOUNT_NAME: $(LW_ACCOUNT_NAME)
Add the variables LW_ACCESS_TOKEN and LW_ACCOUNT_NAME to your pipeline in Azure DevOps. See Integrate Inline Scanner to retrieve the values.
You can use the executable or the Docker container. See Docker Image for Inline Scanner.
Integrate with TravisCI
This sample .travis.yml file demonstrates scanning an image with Lacework.
services:
- docker
# Environment variables. These can be set up once in Travis instead of .travis.yml
env:
global:
- LW_ACCESS_TOKEN=YourAccessToken
- LW_ACCOUNT_NAME=YourAccountName
script: ->
docker run
-e LW_ACCOUNT_NAME=$LW_ACCOUNT_NAME
-e LW_ACCESS_TOKEN=$LW_ACCESS_TOKEN
-v /var/run/docker.sock:/var/run/docker.sock
lacework/lacework-inline-scanner:latest image evaluate YourImageNameToScan YourImageTagToScan
--build-id $TRAVIS_BUILD_ID --build-plan $TRAVIS_JOB_NAME
Integrate with GitHub Actions
Add the variables LW_ACCESS_TOKEN and LW_ACCOUNT_NAME to your pipeline in GitHub Actions. See
Configure Authentication Using Environment Variables
and GitHub Environments Documentation
- uses: lacework/lw-scanner-action@v1.0.0
name: Scan container image for vulnerabitilies using Lacework
with:
LW_ACCOUNT_NAME: ${{ secrets.LW_ACCOUNT_NAME }}
LW_ACCESS_TOKEN: ${{ secrets.LW_ACCESS_TOKEN }}
IMAGE_NAME: YourImageName
IMAGE_TAG: YourImageTag
For more information about other available options, see Github Action for using the Lacework inline scanner.
You can use the executable or the Docker container. See Docker Image for Inline Scanner.
Integrate with Gitlab
The following is an example of a gitlab.yaml file using Docker to build an image and the Lacework inline scanner to evaluate the image.
You can use the executable or the Docker container. See Docker Image for Inline Scanner.
stages:
- build
docker:image:
stage: build
image: docker:1.11
services:
- docker:dind
script:
- docker build -t image_name:tag .
- apt-get update &&
- apt-get -y install curl &&
- curl -L https://github.com/lacework/lacework-vulnerability-scanner/releases/latest/download/lw-scanner-linux-amd64 -o lw-scanner
- chmod u+x lw-scanner &&
- ./lw-scanner image evaluate image_name tag
- echo "Performing Vulnerability Scan powered by Lacework"
- Add the following variables to your Gitlab project through the Gitlab console.
- Go to your project’s Settings > CI/CD and select Variables.
- Click Add Variable.
- Add
LW_ACCESS_TOKENwith the token value. - Add
LW_ACCOUNT_NAMEwith the name value.
Integrate with Bitbucket Pipelines
The Lacework Scan Bitbucket Pipe lets you integrate Lacework container security capabilities into your Bitbucket Pipeline's CI/CD. It allows you to scan and assess Docker container images and software packages for vulnerabilities during the build stage. Optionally, you can stop and fail the build when issues are detected to prevent vulnerable software from being deployed.
Container vulnerability policies must be set in Lacework in order to block CI/CD builds. Learn how to create a policy and attach the policy to the inline scanner integration.
Here's a full example Bitbucket Pipeline using the Lacework Scan pipe.
Add the following snippet to the script section of your bitbucket-pipelines.yml file:
script:
- pipe: lacework/lacework-scan:1.1.6
variables:
LW_ACCOUNT_NAME: "<string>" # Required
LW_ACCESS_TOKEN: "<string>" # Required
IMAGE_NAME: "<string>" # Required
IMAGE_TAG: "<string>" # Required
Pipe Variables
Use the following variables to control the Lacework Scan Bitbucket pipe behavior.
| Variable | Usage |
|---|---|
| LW_ACCOUNT_NAME (*) | Your Lacework account name. For example, if your login URL is mycompany.lacework.net, the account name is mycompany. |
| LW_ACCESS_TOKEN (*) | Authorization token. Copy and paste the token from the inline scanner integration created in the Lacework Console. |
| IMAGE_NAME (*) | The local Docker image to scan. |
| IMAGE_TAG (*) | The local Docker image tag . |
(*) = required variable.
Integrate with AWS CodeBuild
AWS CodeBuild is a fully managed cloud CI service that can build your source code and test and deploy your applications. You can integrate the Lacework inline scanner into the AWS CodeBuild build stage to discover software vulnerabilities. Optionally, you can use AWS CodeBuild with AWS CodePipeline to orchestrate multiple AWS CodeBuild projects that build and deploy. An example of using Lacework with AWS CodePipeline and CodeBuild can be found in this repository.
To add the Lacework inline scanner to your AWS CodeBuild project, follow this AWS CodeBuild buildspec example that performs a Docker build, Lacework vulnerability scan and then a Docker push to Amazon Elastic Container Registry (ECR).
You can use the executable or the Docker container. See Docker Image for Inline Scanner.
This example shows you how to pull the Lacework inline scanner account and token from the SSM parameter store, set environment variables, and install and run the Lacework inline scanner. Vulnerability results appear in the AWS CodeBuild build logs.
version: 0.2
env:
parameter-store:
LW_ACCOUNT_NAME: "LWAccountName" # pull Lacework inline scanner parameters from SSM parameter store
LW_ACCESS_TOKEN: "InlineScannerToken"
phases:
build:
commands:
- docker build -t "$DOCKER_REG/$IMAGE_NAME:$CODEBUILD_BUILD_NUMBER" -t "$DOCKER_REG/$IMAGE_NAME:latest" .
post_build:
commands:
- export LW_ACCOUNT_NAME=$LW_ACCOUNT_NAME #Set Lacework inline scanner environment variables
- export LW_ACCESS_TOKEN=$LW_ACCESS_TOKEN
- export LW_SCANNER_DISABLE_UPDATES=true
- export LW_SCANNER_SAVE_RESULTS=true
- rm -rf ./evaluations/$IMAGE_NAME/$CODEBUILD_BUILD_NUMBER/evaluation_*.json || true
- curl -L https://github.com/lacework/lacework-vulnerability-scanner/releases/latest/download/lw-scanner-linux-amd64 -o lw-scanner # install
- chmod +x lw-scanner
- ./lw-scanner image evaluate $DOCKER_REG/$IMAGE_NAME $CODEBUILD_BUILD_NUMBER --build-id $CODEBUILD_BUILD_NUMBER --data-directory . # execute
- aws ecr get-login-password --region $AWS_REGION | docker login --username AWS --password-stdin $DOCKER_REG
- docker image push -a "$DOCKER_REG/$IMAGE_NAME"
Integrate with Circle CI
CircleCI is a continuous integration and delivery platform that you can use to implement DevOps practices.
The following example shows you how to run a container vulnerability scan with Lacework.
orbs:
lacework: lacework/lacework@x.y
version: 2.1
workflows:
scan_my_container:
jobs:
- lacework/ctr-vuln-scan:
registry: index.docker.io
repository: lacework/lacework-cli
The following example shows you how to generate the container vulnerability assessment in HTML format and store the artifact automatically with Lacework.
orbs:
lacework: lacework/lacework@x.y
version: 2.1
workflows:
scan_container_and_generate_html_artifact:
jobs:
- lacework/ctr-vuln-scan:
html: true
registry: index.docker.io
repository: lacework/lacework-cli
Optionally, you can implement exit codes to stop the pipelines when the scan returns fixable vulnerabilities, see Exit codes for Policy Violations.
To enable the exit codes, set fail_on_fixable attribute to true.
orbs:
lacework: lacework/lacework@x.y
version: 2.1
workflows:
scan_container_and_terminate_pipeline_on_fixable_vuln:
jobs:
- lacework/ctr-vuln-scan:
fail_on_fixable: true
html: true
registry: index.docker.io
repository: lacework/lacework-cli
The following example shows you how to scan an image with Lacework.
orbs:
lacework: lacework/lacework@x.y
version: 2.1
workflows:
scan_my_container:
jobs:
- lacework/inline-scanner-scan:
image_name: lacework/lacework-cli
image_tag: latest
The following example shows you how to scan a package manifest with Lacework.
orbs:
lacework: lacework/lacework@x.y
version: 2.1
workflows:
scan_my_container:
jobs:
- lacework/scan-pkg-manifest:
manifest: >-
{ "os_pkg_info_list": [ { "os":"Ubuntu", "os_ver":"18.04", "pkg":
"openssl", "pkg_ver": "1.1.1-1ubuntu2.1~18.04.5" } ] }
You can use the executable or the Docker container. See Docker Image for Inline Scanner.
Docker Image for Inline Scanner
The inline scanner is also distributed in a Docker image and you can use it as an alternative to the binary in CI systems.
Run the Docker image to start a Docker daemon on your host using the default daemon socket (/var/run/docker.sock). This creates a single container that can perform the following commands:
All other commands are disabled.
info
If you want to run the Docker image inside another Docker image, ensure that the host image is running Docker before deployment.
CPU and Memory Resources
See Inline Scanner - CPU and Memory Resources for resource recommendations.
Download the Image
Pull the image from the Lacework repository:
docker pull lacework/lacework-inline-scanner:latest
Use the Image
The configure commands are disabled for the Docker image. See Configuration using Environment Variables for environmental configuration options.
note
LW_SCANNER_DISABLE_UPDATES is set to true by default for the docker image which provides a cleaner output.
image evaluate
Provide the LW_ACCOUNT_NAME and LW_ACCESS_TOKEN environment variables to authenticate with Lacework.
docker run \
-e LW_ACCOUNT_NAME=myCompany \
-e LW_ACCESS_TOKEN=_myAccessToken123 \
-v /var/run/docker.sock:/var/run/docker.sock \
lacework/lacework-inline-scanner:latest \
image evaluate ubuntu latest \
--build-id myBuildId123 --build-plan myBuildPlan
Add or remove image evaluate flags depending on your requirements.
image scan
Provide the LW_ACCOUNT_NAME and LW_ACCESS_TOKEN environment variables to authenticate with Lacework.
docker run \
-e LW_ACCOUNT_NAME=myCompany \
-e LW_ACCESS_TOKEN=_myAccessToken123 \
-v /var/run/docker.sock:/var/run/docker.sock \
lacework/lacework-inline-scanner:latest \
image evaluate ubuntu latest
Add or remove image scan flags depending on your requirements.
version
Provide the LW_ACCOUNT_NAME and LW_ACCESS_TOKEN environment variables to authenticate with Lacework.
docker run \
-e LW_ACCOUNT_NAME=myCompany \
-e LW_ACCESS_TOKEN=_myAccessToken123 \
-e LW_SCANNER_DISABLE_UPDATES=false \
-v /var/run/docker.sock:/var/run/docker.sock \
lacework/lacework-inline-scanner:latest \
version
In this example, setting LW_SCANNER_DISABLE_UPDATES=false prompts you if a new version of the inline scanner is available.