AWS Integration Using CloudFormation
Overview
Lacework integrates with AWS to analyze CloudTrail for monitoring cloud account security, and for cloud resource configuration compliance.
AWS CloudFormation gives you an easy way to model a collection of related AWS and third-party resources, provision them quickly and consistently, and manage them throughout their lifecycles, by treating infrastructure as code. A CloudFormation template describes your resources and their dependencies so you can launch and configure them together as a stack. You can use a template to create, update, and delete an entire stack as a single unit, as often as you need to, instead of managing resources individually. You can manage and provision stacks across multiple AWS accounts and AWS regions.
For details about AWS CloudFormation, see AWS CloudFormation.
This document describes how to integrate Lacework with AWS CloudFormation with one of the following configurations:
- Configuration to analyze AWS configuration compliance
- CloudTrail+Configuration to analyze CloudTrail activity for monitoring cloud account security and AWS configuration compliance
Navigate to CloudFormation
Follow these steps to integrate using CloudFormation:
- Log in to the Lacework Console.
- Go to Settings > Integrations > Cloud accounts.
- Click + Add New.
- Click Amazon Web Services and select one of the following options:
- Configuration to analyze AWS configuration compliance
- CloudTrail+Configuration to analyze CloudTrail activity for monitoring cloud account security and AWS configuration compliance
- Click Next.
- Click CloudFormation.
- Follow the steps in the section corresponding to your previous choice:
AWS Configuration Compliance with CloudFormation
The procedures in this section configure an integration to analyze AWS configuration compliance only.
During initial Lacework account setup, you can add a single AWS account to Lacework. Later you can add additional accounts from the Lacework Console using a CloudFormation template that launches the AWS console. However, integrating multiple AWS accounts using the AWS console is not efficient because each integration requires you to log in to each account with administrative privileges and ensure there are no resource conflicts when creating the CloudFormation stack. Instead, you can integrate multiple AWS accounts using Terraform.
During integration, Lacework creates an IAM role with the least privileges. To grant Lacework permission to create this role, you must log in to your AWS account as a user with administrator credentials [arn:aws:iam::aws:policy/AdministratorAccess]. You cannot complete the integration without the required credentials.
AWS Configuration
- Choose either Run CloudFormation Template or Download Cloud Formation Template to select a CloudFormation option. After performing the steps outlined in the referenced documentation, click Next.
- Specify Details on the Create Stack - Specify Details page. After performing these steps, click Next.
- No changes are required on the Create stack - Options page. Click Next.
- Review and click Create stack on the Create stack - Review page.
- Select your stack to see the event log as it is being created.
- Return to the Lacework Console onboarding page and click Exit to finish the AWS integration and save your onboarding progress. The integration appears in the list of cloud accounts under Cloud accounts.
For detailed information on AWS integration using CloudFormation templates, see AWS Configuration Compliance with CloudFormation.
Choose an Integration Method
You can either run or download the CloudFormation template. The download option is helpful if you need to distribute the template to different account owners. For the initial setup, Lacework recommends using the Run CloudFormation Template option. Follow the steps for the option you choose.
Option 1: Run CloudFormation Template
This option requires fewer steps and less user interaction. For this option, disable your browser pop-up blocker.
- Click Run CloudFormation template.
You are redirected to the AWS Create stack > Select Template page. The Lacework script populates the Specify an Amazon S3 template URL for you. - Review the page and click Next.
Option 2: Download CloudFormation Template
This option requires more user interaction, but may be useful if you have multiple accounts with distributed ownership.
- Click Download CloudFormation Template.
- Log in to your AWS account.
- Select the CloudFormation service and click Create New Stack. The Create stack > Select Template page displays.
- Upload the Lacework template and click Next.
For more information on Selecting a Stack Template, refer to the AWS Documentation library.
Specify Details
On the Create Stack - Specify Details page:
- Create a Stack name [for example, Lacework-AWS-Config] or use the default.
- Resource name prefix is populated with the account name of the first account configured to use Lacework for AWS Config if the direct configuration method was chosen. When adding accounts, you can keep this prefix or enter a different prefix to ensure account uniqueness. If you chose to upload the template during initial installation, Resource name prefix is empty. Enter a prefix such as an account name.
- ExternalID is populated by Lacework. It is not editable if you used the Run CloudFormation Template option in the Lacework Console.
After completing the above steps, click Next.
Options
No changes are required on the Create stack - Options page. Click Next.
Review
On the Create stack - Review page, complete the following steps:
- Check I acknowledge that AWS CloudFormation might create IAM resources with custom names.
- Click Create stack.
CloudFormation Page
After clicking Create, you are redirected back to the CloudFormation page. If you do not see your new stack in the table, refresh the page. Select your stack to see the event log as it is being created. When the stack is CREATE-COMPLETE, Security Audit integration for a single account is complete.
AWS CloudTrail and Configuration Compliance with CloudFormation
The procedures in this section configure an integration that analyzes CloudTrail activity for monitoring cloud account security and AWS configuration compliance.
Account setup configures Lacework for CloudTrail analysis and Security Audit. After completion, a single CloudFormation stack is added to your account. If you have multiple accounts and you forward CloudTrail logs to a single S3 bucket, CloudTrail integration completes after the account setup. If you use multiple buckets, you can use the Lacework Console to add accounts after the account setup.
To analyze CloudTrail activity for monitoring cloud account security, Lacework requires that accounts be integrated individually. You can use the Lacework Console to add accounts after account setup.
During the account setup, the option to integrate with AWS follows the option to add users.
During integration, Lacework creates the least privilege IAM role. To grant Lacework permission to create this role, you must log in to your AWS account as a user with administrator credentials [arn:aws:iam::aws:policy/AdministratorAccess]. You cannot complete the integration without the required credentials.
note
AWS S3 object-level APIs are excluded from CloudTrail analysis. This means that AWS CloudTrail data events are not analyzed. CloudTrail management events, however, are analyzed.
AWS CloudTrail and Configuration
- Choose either Run CloudFormation Template or Download CloudFormation Template to select a CloudFormation option. After performing these steps, click Next.
- Create a new trail and S3 bucket or use an existing trail and specify the details of the stack. Click Next.
- No changes are required on the Create stack - Options page. Click Next.
- Review and click Create stack on the Create stack - Review page.
- Select your stack to see the event log as it is being created.
- Return to the Lacework Console onboarding page and click Exit to finish the AWS integration and save your onboarding progress. The integration appears in the list of cloud accounts under Cloud accounts.
For detailed information on AWS integration using CloudFormation templates, see AWS CloudTrail and Configuration Compliance with CloudFormation.
Run or Download the CloudFormation Template
You can either run or download the CloudFormation template. The download option is helpful if you need to distribute the template to different account owners. For the initial setup, Lacework recommends the Run CloudFormation Template option. Follow the steps for the option you choose.
Option 1: Run CloudFormation Template
This option requires fewer steps and less user interaction. For this option, disable your browser pop-up blocker.
- Click Run CloudFormation template.
You are redirected to the AWS Create stack > Select Template page. The Lacework script populates the Specify an Amazon S3 template URL for you. - Review the page and click Next.
Option 2: Download CloudFormation Template
This option requires more user interaction, but may be useful if you have multiple accounts with distributed ownership.
- Click Download CloudFormation Template.
- Log in to your AWS account.
- Select the CloudFormation service and click Create New Stack. The Create stack > Select Template page displays.
- Upload the Lacework template and click Next.
For more information on Selecting a Stack Template, refer to the AWS Documentation library.
New Trail or Existing Trail
On the Create stack > Specify Details page, you can either create a new trail and S3 bucket or use an existing trail. First, create a Stack name or choose the default.
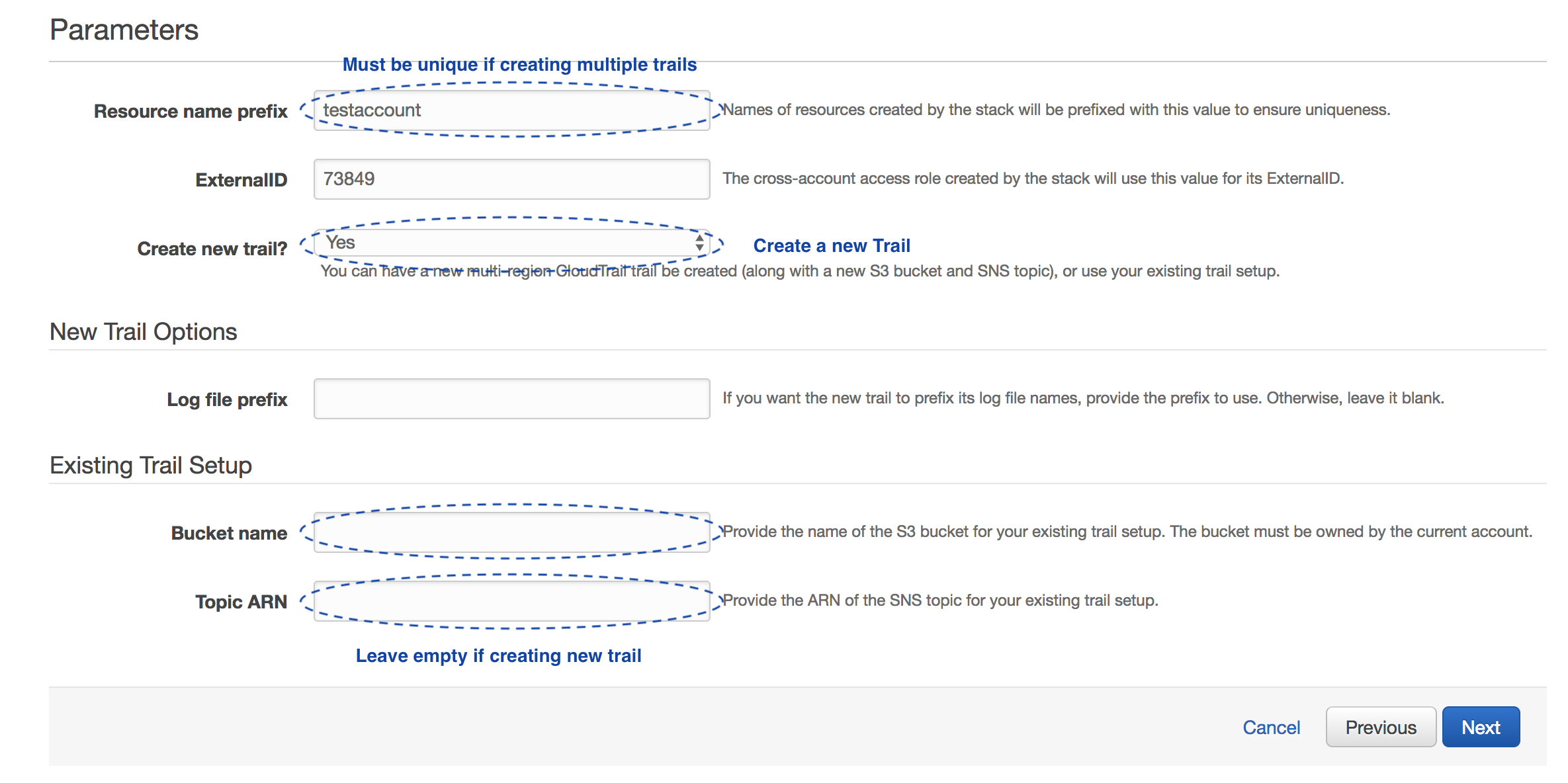
Option 1: Create a new trail and S3 bucket
If you plan to integrate multiple accounts separately, the Resource Name Prefix must be different for each account because S3 bucket names are globally unique.
- Resource name prefix should be pre-populated with your account name. It doesn't need to change unless:
- You are creating a stack for each account, in which case it must be unique for each account as the S3 bucket namespace is global, or
- You are creating multiple stacks, in which case it must be unique to avoid resource collision
- ExternalID is populated by Lacework. It is not editable if you used the Run Cloud Formation Template option in the Lacework Console.
- Set Create a new trail? to Yes.
- A Log file prefix can be added if you want a specific S3 bucket path for your logs.
- Bucket name and Topic ARN should be left blank.
- Click Next.
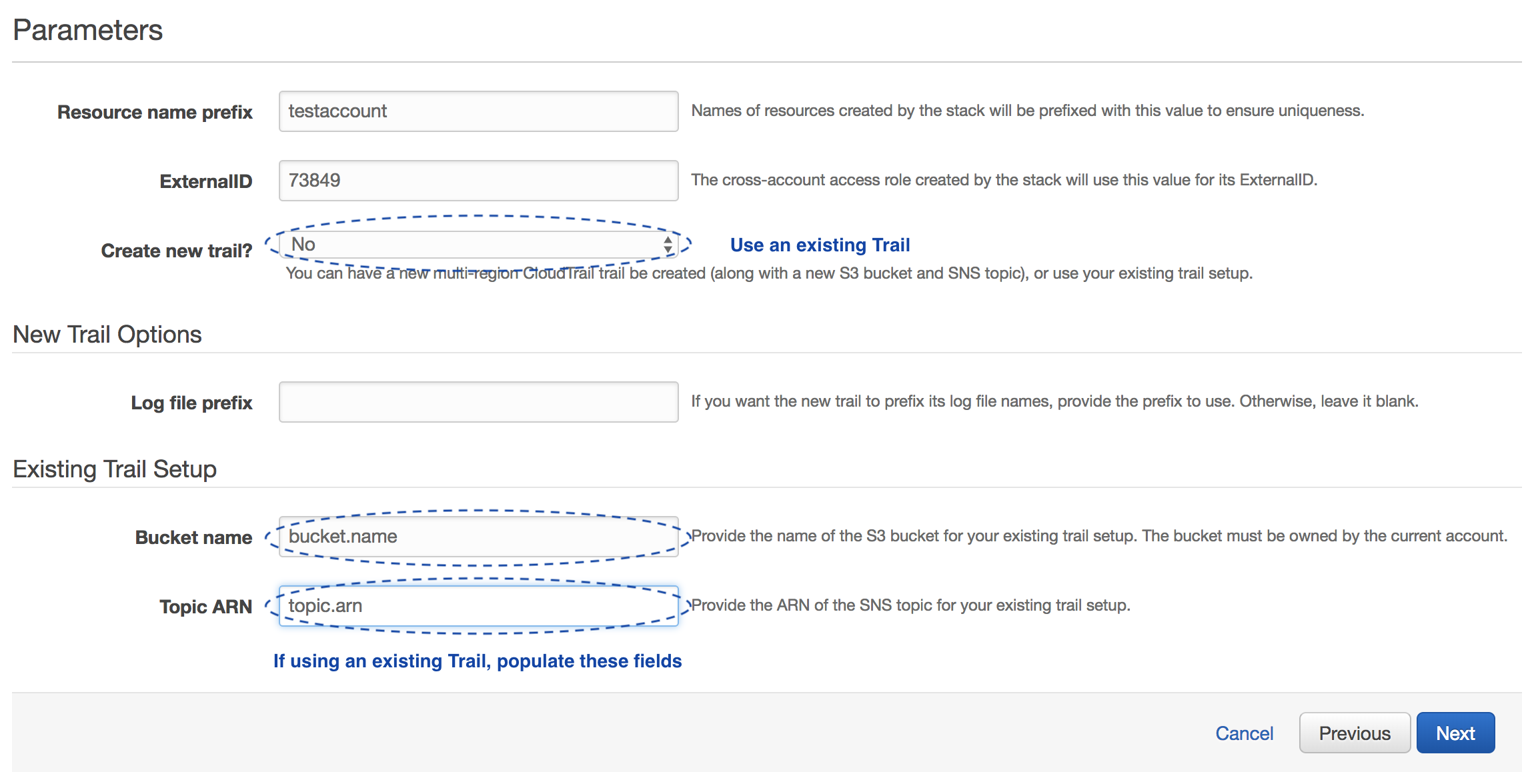
Option 2: Use an existing trail
- Resource name prefix should be pre-populated with your account name.
- ExternalID is populated by Lacework. It is not editable if you used the Run Cloud Formation Template option in the Lacework Console.
- Set Create a new trail? to No.
- A Log file prefix is not applicable as you are not creating a new trail.
- Enter the Bucket name (not ARN) associated with your existing trail.
- Add the SNS Topic ARN of your existing trail into Topic ARN. If the trail does not already have an SNS topic, create one.
- Click Next.
note
If you are integrating an existing trail, you may be using server-side encryption. If using Server-Side Encryption with Amazon S3-Managed Keys (SSE-S3), key management is local to S3, so no changes are required. If you are using Server-Side Encryption with AWS KMS-Managed Keys (SSE-KMS), key management requires access to the AWS KMS service, so you must give the Lacework-created role the required permission. See this topic for instructions on how to update the inline policy associated with the Lacework-created role. If you are manually integrating Lacework, you must grant this same permission.
Options Page
The Create stack > Options page displays. This page does not need changes. Click Next.
Review Page
The Create stack > Review page displays.
- Check I acknowledge that AWS CloudFormation might create IAM resources with custom names.
- Click Create stack.
CloudFormation Page
After clicking Create, you are redirected back to the CloudFormation page. If you do not see your new stack in the table, refresh the page. Select your stack to see the event log as it is being created. When the stack is CREATE-COMPLETE, integration of both CloudTrail and Config for a single account is complete. If you consolidate CloudTrail logs in one S3 bucket, no additional CloudTrail configuration is required.