AWS GovCloud Integration
info
Lacework now provides AWS GovCloud support for Resource Inventory which allows GovCloud customers to migrate to the new CSPM Compliance engine based on LPP/LQL.
AWS GovCloud (US-East and US-West) are isolated regions within AWS for customers to host sensitive data for supporting their regulated workflows. The configuration workflows described below differ from AWS standard regions and are relevant for monitoring only AWS GovCloud environments within the Lacework application.
Creating an integration between Lacework and an AWS GovCloud requires running steps in the AWS GovCloud console followed by running additional steps in the Lacework Console.
The steps below configure AWS CloudTrail (US GovCloud) with AWS Config (US GovCloud) integration.
If you want to integrate AWS GovCloud using Terraform, see Configuration (US GovCloud) Integration with Terraform or CloudTrail and Configuration (US GovCloud) Integration with Terraform.
AWS Setup
Create the Lacework AWS GovCloud CloudFormation Template
You must create an AWS GovCloud CloudFormation template file that creates a new AWS GovCloud CloudFormation stack.
To download and customize the template file:
Open a text editor.
Click the following link: https://raw.githubusercontent.com/lacework/lacework-cloudformation/main/aws-govcloud-template/lacework-aws-gov-cloud-ct-cfg.json
The Lacework AWS GovCloud CloudFormation template file displays in GitHub.Select all text in the GitHub window of the browser. (In Chrome, select Edit > Select All.)
Copy the text. (In Chrome, select Edit > Copy.)
Paste the text into the text editor.
In the text editor, replace the %acnt string with the name of your AWS account.
"Parameters": {
"ResourceNamePrefix":
{
...
"Default": "%acnt",
...
},Save the file as lacework-aws-gov-cloud-ct-cfg.json in the text editor.
Create a Stack in CloudFormation Using the Customized CloudFormation Template
To create a new stack in the AWS GovCloud:
Log in to an AWS account on the AWS GovCloud with administrative credentials. The AWS account used to create the stack must use a role with the aws:policy/SecurityAudit permission.
Select the CloudFormation service.
In the AWS console, select Services > Management Tools > CloudFormation. The Create Stack panel displays.From the Region drop-down located in the top left of the menu bar, select the appropriate region for your environment.
Click Create Stack.
The Select Template panel displays.Under Choose a template, select Upload a template to Amazon S3. Browse for the Lacework AWS GovCloud template file that you previously created and click Open.
Click Next.
The Specify Details page displays.In the Stack name field, enter a unique value.
On the Create stack > Specify Details page, you can either create a new trail and S3 bucket or use an existing trail. Follow the appropriate procedure for your AWS GovCloud environment:
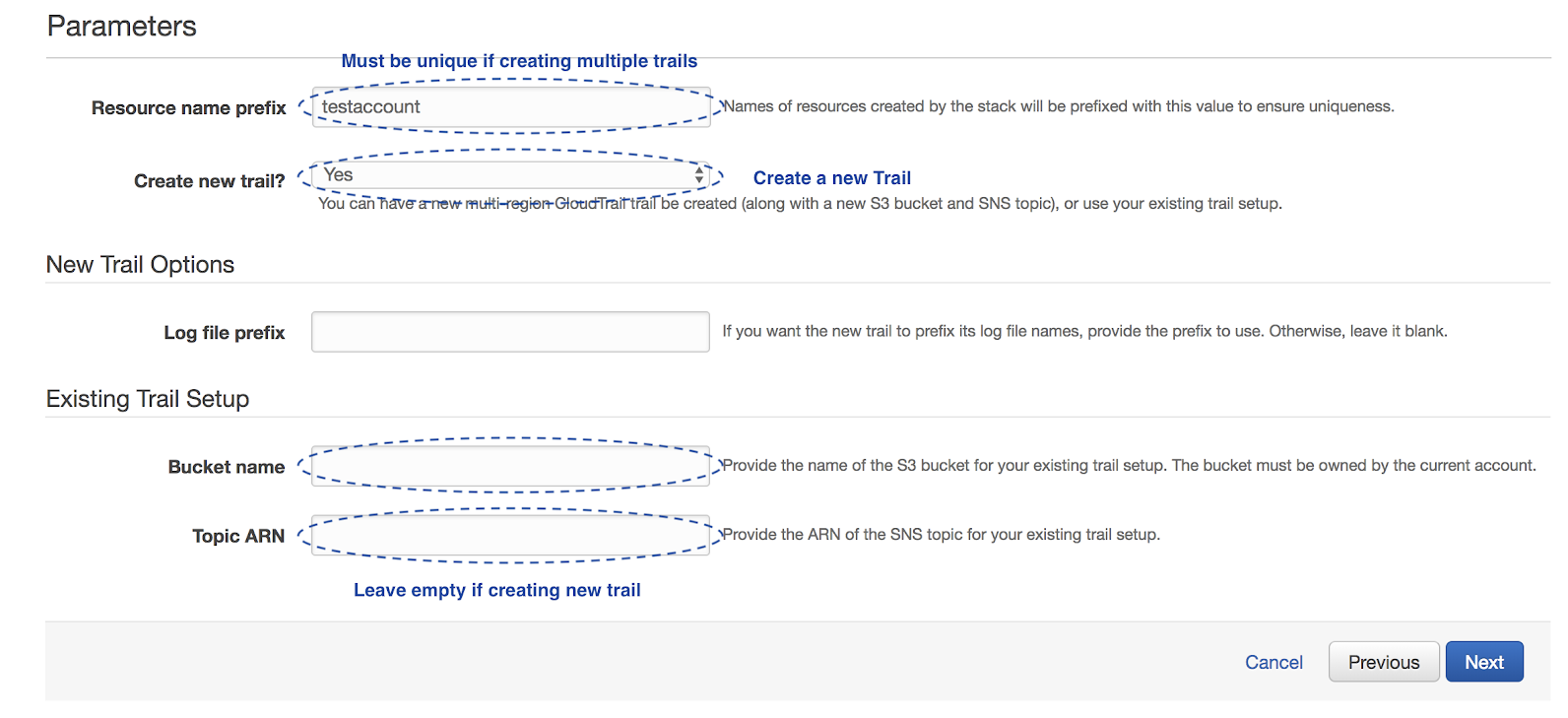
Option 1 - Create a New Trail and S3 Bucket
If you plan to separately integrate multiple accounts, the Resource Name Prefix must be different for each account because S3 bucket names are globally unique.
- Resource name prefix should be pre-populated with your account name. The value does not need to change unless:
- you are creating a stack for each account—For this case, the value must be unique for each account because the S3 bucket namespace is global.
- you are creating multiple stacks—For this case, the value must be unique to avoid a resource collision.
- Set Create a new trail? to Yes.
- If you want a specific S3 bucket path for your logs, add a Log file prefix.
- Leave the values for Bucket name and Topic ARN blank.
- Click Next.
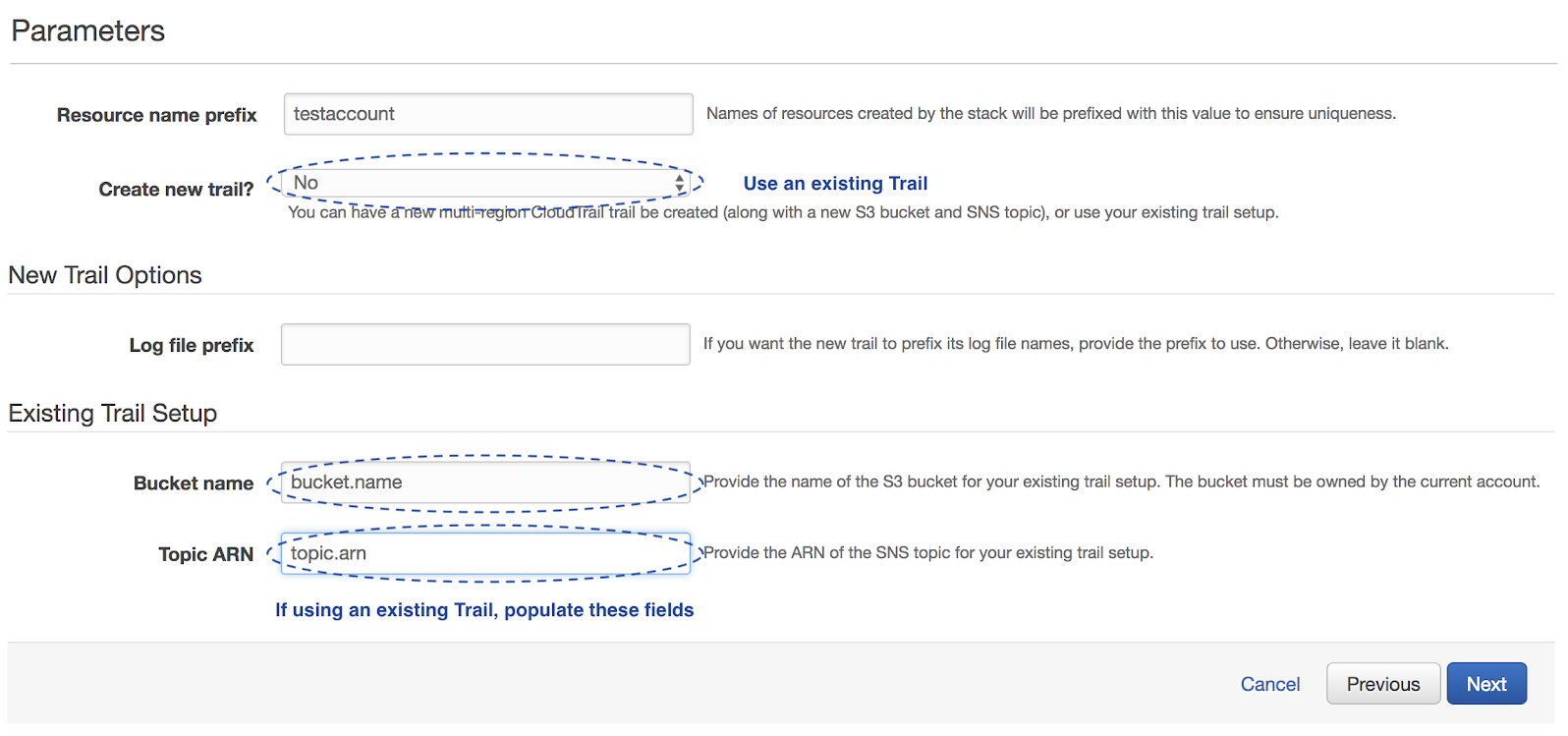
Option 2 - Use an Existing Trail
- Resource name prefix should be pre-populated with your account name.
- Set Create a new trail? to No.
- The Log file prefix is not applicable because you are not creating a new trail.
- Enter the Bucket name associated with your existing trail.
- Add the SNS Topic ARN of your existing trail into Topic ARN. If the trail does not already have an SNS topic, you must create one.
- Click Next.
note
If you are integrating an existing trail, you may be using server-side encryption. If using Server-Side Encryption with Amazon S3-Managed Keys (SSE-S3), key management is local to S3, and therefore no changes are required. If you are using Server-Side Encryption with AWS KMS-Managed Keys (SSE-KMS), key management requires access to the AWS KMS service, so you must give the Lacework-created role the required permission. See Integration with S3 Buckets Using SSE-KMS for instructions on how to update the inline policy associated with the Lacework-created role. If you are manually integrating Lacework, you will need to grant this same permission.
Continue Stack Creation and Gather Settings
Complete the creation of the stack in the AWS console and gather the required settings as described by the following steps.
- In the Create stack > Options page, no changes are required. Click Next.
- In the Create Stack > Review page, select the acknowledgment and click Create. After clicking Create, you are redirected back to the CloudFormation page.
- If you do not see your new stack in the table, refresh the page. Keep refreshing the page until the status of the stack is CREATE-COMPLETE.
- After the stack status is CREATE-COMPLETE, click the stack name link.
- Expand Outputs.
- Leave the AWS console open to this page so you can copy the following values about the stack:
- AccountId
- AccessKeyId
- SecretAccessKey
- SQSQueueURL
Use the Lacework Console
You can use the Lacework Console for AWS GovCloud manual configuration.
- Log in to the Lacework Console.
- Go to Settings > Integrations > Cloud accounts.
- Click + Add New.
- Click Amazon Web Services and select Manual configuration.
- Click Next.
- Select a GovCloud integration type and follow the corresponding steps.
- Configuration (US GovCloud) to analyze AWS configuration compliance.
- CloudTrail and Configuration (US GovCloud) to analyze CloudTrail activity for monitoring cloud account security and AWS configuration compliance.
Configuration (US GovCloud) Manual Integration
Ensure you have completed AWS setup as described in AWS Setup.
- For Name, specify a unique name that displays in the Lacework Console.
- For Account ID, enter your AWS account identifier or alias.
- For Access Key ID, enter the AccessKeyId value from the AWS console.
- For Secret Access Key, enter the SecretAccessKey value from the AWS console.
- Click Save to finish the AWS integration and save your onboarding progress.
The integration appears in the list of cloud accounts under Cloud accounts.
CloudTrail and Configuration (US GovCloud) Manual Integration
Ensure you have completed AWS setup as described in AWS Setup.
- For Name, specify a unique name that displays in the Lacework Console.
- For Account ID, enter your AWS account identifier or alias.
- For Access Key ID, enter the AccessKeyId value from the AWS console.
- For Secret Access Key, enter the SecretAccessKey value from the AWS console.
- For, SQSQueueURL, specify the Amazon Simple Queue Service (SQS) URL value.
- Click Save to finish the AWS integration and save your onboarding progress.
The integration appears in the list of cloud accounts under Cloud accounts.
Use Terraform
Configuration (US GovCloud) Integration with Terraform
For organizations using Terraform to manage their environments, Lacework maintains the Terraform provider for Lacework, which enables configuration of Lacework integrations using automation.
If you are new to the Lacework Terraform Provider or Lacework Terraform Modules, read the Terraform for Lacework Overview to learn the basics on how to configure the provider and more.
- Ensure you have the Lacework CLI installed and configured to the Lacework account you plan to integrate.
- Install the AWS CLI. For details on how to install the AWS CLI, see Configuring your AWS CLI.
- Open an editor (such as Vim) and create a new Terraform file called main.tf.
- Edit the Terraform file to specify the Lacework AWS US GovCloud Terraform provider by copying and pasting the code under Use Provider in the Lacework Terraform provider for AWS Config US GovCloud into your Terraform file.
- Add the
lacework_integration_aws_govcloud_cfgTerraform resource and its related parameters, such as the name, account_id and credentials, into your Terraform file. For an example of this Terraform resource and parameters to use for AWS US GovCloud, see Example Usage and GovCloud Terraform Example. - Open a Terminal and change directories to the directory that contains the Terraform file and run
terraform initto initialize the project and download the required modules. - Run
terraform planto validate the configuration and review pending changes. - After you review the pending changes,
run terraform applyto execute changes.note
This Lacework Terraform provider has a number of inputs for customization. Visit the documentation on the lacework_integration_aws_govcloud_cfg for the complete list of inputs.
- After Terraform finishes applying changes, use the Lacework CLI or log in to the Lacework Console to validate the integration.
- Go back to the Lacework Console onboarding page and click Exit to finish the AWS integration and save your onboarding progress. The integration appears in the list of cloud accounts under Cloud accounts.
CloudTrail and Configuration (US GovCloud) Integration with Terraform
For organizations using Terraform to manage their environments, Lacework maintains the Terraform provider for Lacework, which enables configuration of Lacework integrations using automation.
If you are new to the Lacework Terraform Provider or Lacework Terraform Modules, read the Terraform for Lacework Overview to learn the basics on how to configure the provider and more.
- Ensure you have the Lacework CLI installed and configured to the Lacework account you plan to integrate.
- Install the AWS CLI. For details on how to install the AWS CLI, see Configuring your AWS CLI.
- Open an editor (such as Vim) and create a new Terraform file called main.tf.
- Edit the Terraform file to specify the Lacework AWS US GovCloud Terraform provider by copying and pasting the code under Use Provider in the Lacework Terraform provider for AWS Config US GovCloud into your Terraform file.
- Add the
lacework_integration_aws_govcloud_cfgTerraform resource and its related parameters, such as the name, account_id and credentials, into your Terraform file. For an example of this Terraform resource and parameters to use for AWS US GovCloud, see Example Usage and GovCloud Terraform Example. - Add the
lacework_integration_aws_govcloud_ctTerraform resource and its related parameters, such as the name, account_id, queue_url and credentials, into your Terraform file. For an example of this Terraform resource and parameters to use for AWS CloudTrail US GovCloud, see Example Usage and GovCloud Terraform Example. - Open a Terminal and change directories to the directory that contains the Terraform file and run
terraform initto initialize the project and download the required modules. - Run
terraform planto validate the configuration and review pending changes. - After you review the pending changes,
run terraform applyto execute changes.note
This Lacework Terraform provider has a number of inputs for customization. Visit the documentation on the lacework_integration_aws_govcloud_cfg and lacework_integration_aws_govcloud_ct for the complete list of inputs.
- After Terraform finishes applying changes, use the Lacework CLI or log in to the Lacework Console to validate the integration.
- Go back to the Lacework Console onboarding page and click Exit to finish the AWS integration and save your onboarding progress. The integration appears in the list of cloud accounts under Cloud accounts.
Terraform GovCloud Examples
# Configure AWS GovCloud Config integration in Lacework
resource "lacework_integration_aws_govcloud_cfg" "example" {
name = "AWS gov cloud config integration example"
account_id = "553453453"
credentials {
access_key_id = "AWS123abcAccessKeyID"
secret_access_key = "AWS123abc123abcSecretAccessKey0000000000"
}
}
# Configure AWS GovCloud CloudTrail integration in Lacework
resource "lacework_integration_aws_govcloud_ct" "example" {
name = "AWS gov cloud cloudtrail integration example"
account_id = "553453453"
queue_url = "https://sqs.us-gov-west-1.amazonaws.com/123456789012/my_queue"
credentials {
access_key_id = "AWS123abcAccessKeyID"
secret_access_key = "AWS123abc123abcSecretAccessKey0000000000"
}
}
You can find additional information on the lacework_integration_aws_govcloud_cfg and lacework_integration_aws_govcloud_ct resources in the Terraform Registry.