Critical Apache Log4j Vulnerability
Overview
On Dec 9, 2021, a Critical Day 0 vulnerability was disclosed by Apache that affects Apache Log4j2 (CVE-2021-44228). This document describes the vulnerability, what Lacework is doing to provide you with the appropriate coverage, and what you should be doing to protect your organization.
important
The Apache Log4j remote code execution (RCE) vulnerability is of critical severity and should be remediated immediately wherever possible.
What is the Apache Log4j2 JNDI Vulnerability?
From the NIST National Vulnerability Database: "Apache Log4j2 <= 2.14.1 JNDI features used in configuration, log messages, and parameters do not protect against attacker-controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled. From log4j 2.15.0, this behavior has been disabled by default."
important
UPDATE: Apache updated its guidance on December 18, 2021. Log4j v2.15.0 and v2.16.0 are still affected. Upgrade to v2.17.0.
What has Lacework been doing to protect you since the vulnerability was announced?
As of the morning of December 10, 2021, all active images and active hosts for all customers have been re-evaluated for this vulnerability. If this vulnerability was identified in your environment, it appears as a Critical vulnerability (CVE-2021-44228) in your vulnerability dashboard, and Lacework recommends that you take action as soon as possible to remediate it.
As of December 10, 2021 morning, new scans will detect CVE-2021-44228. In addition, due to the severity of this threat, Lacework is in the process of automating re-evaluation of ALL images from the last seven days that include the vulnerable packages on behalf of our customers (regardless of active status).
What should you be doing?
How to find this vulnerability on live containers using the Lacework Console
- Under Vulnerabilities > Containers, select Group by Image ID and search CVE includes, CVE-2021-44228. If it's not already selected, select Active.
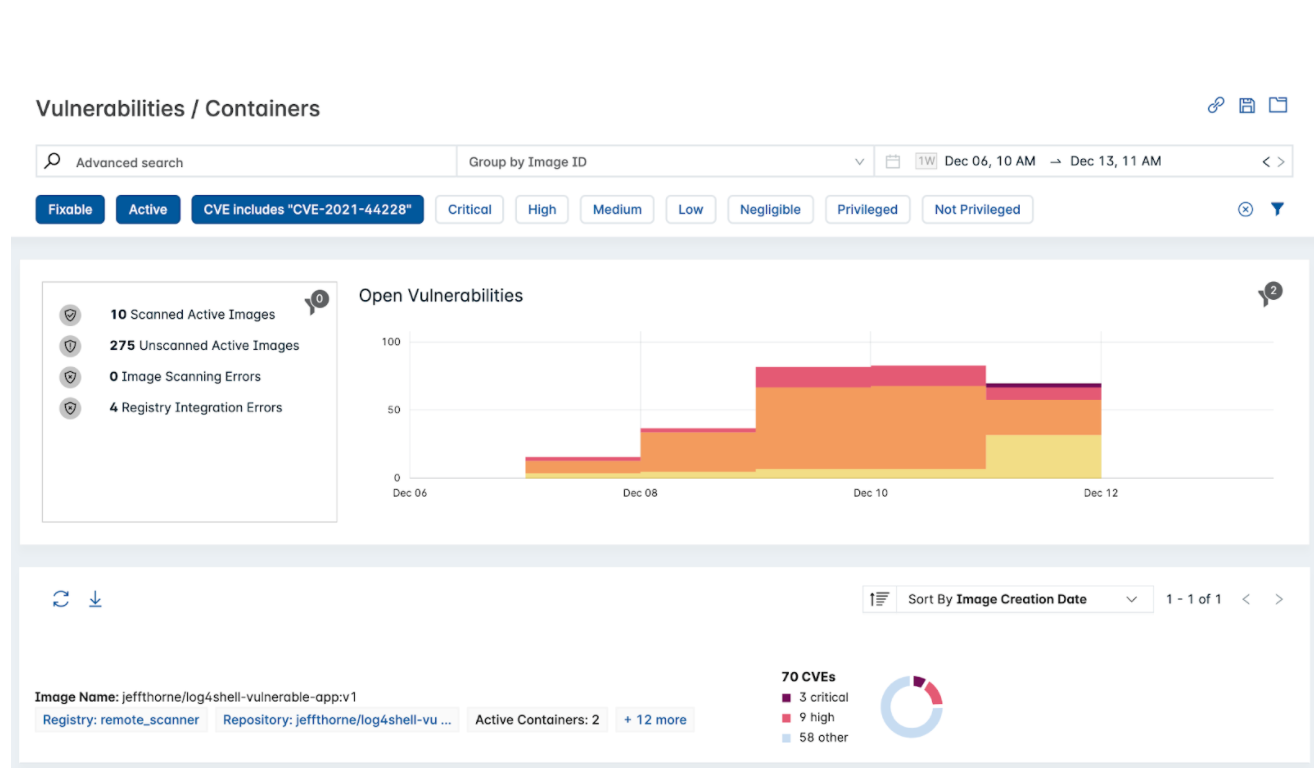
- Select an item from the results and click Details.
- Copy the Image ID and click Active Containers at the bottom.
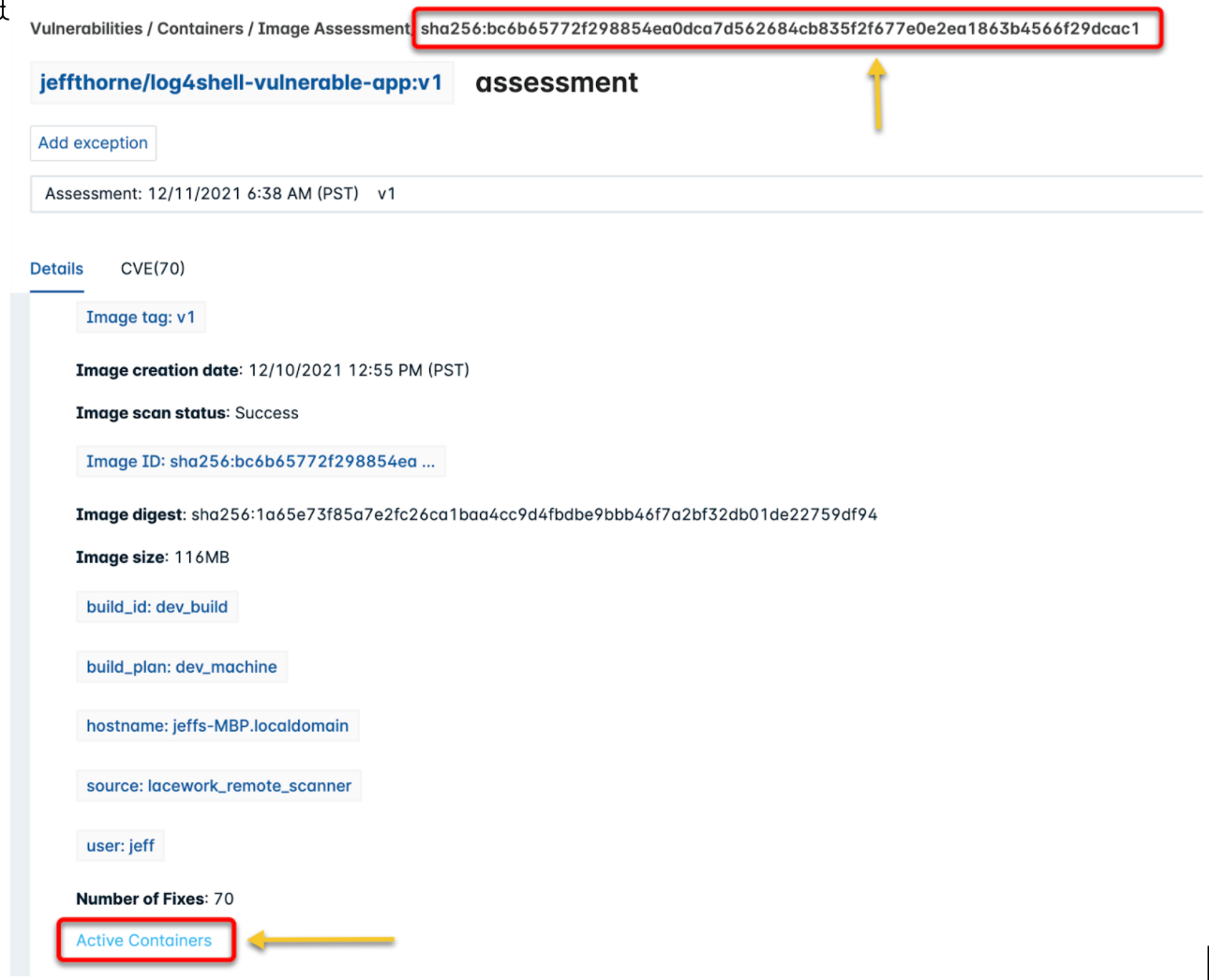
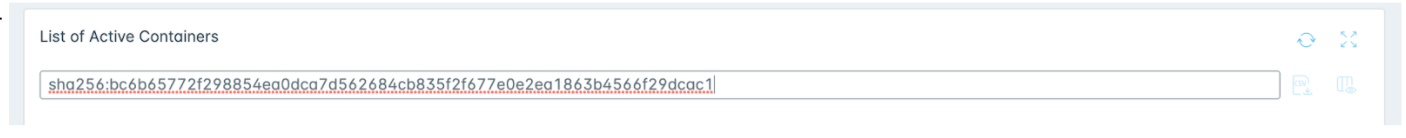
- Scroll down to the List of Active Containers card and paste the Image ID into the search field.
How to find this vulnerability on hosts using the Lacework Console
The simplest way to determine if your environment is vulnerable is to go to Vulnerabilities > Hosts, select Group by CVE and search Any Value, includes, CVE-2021-44228.
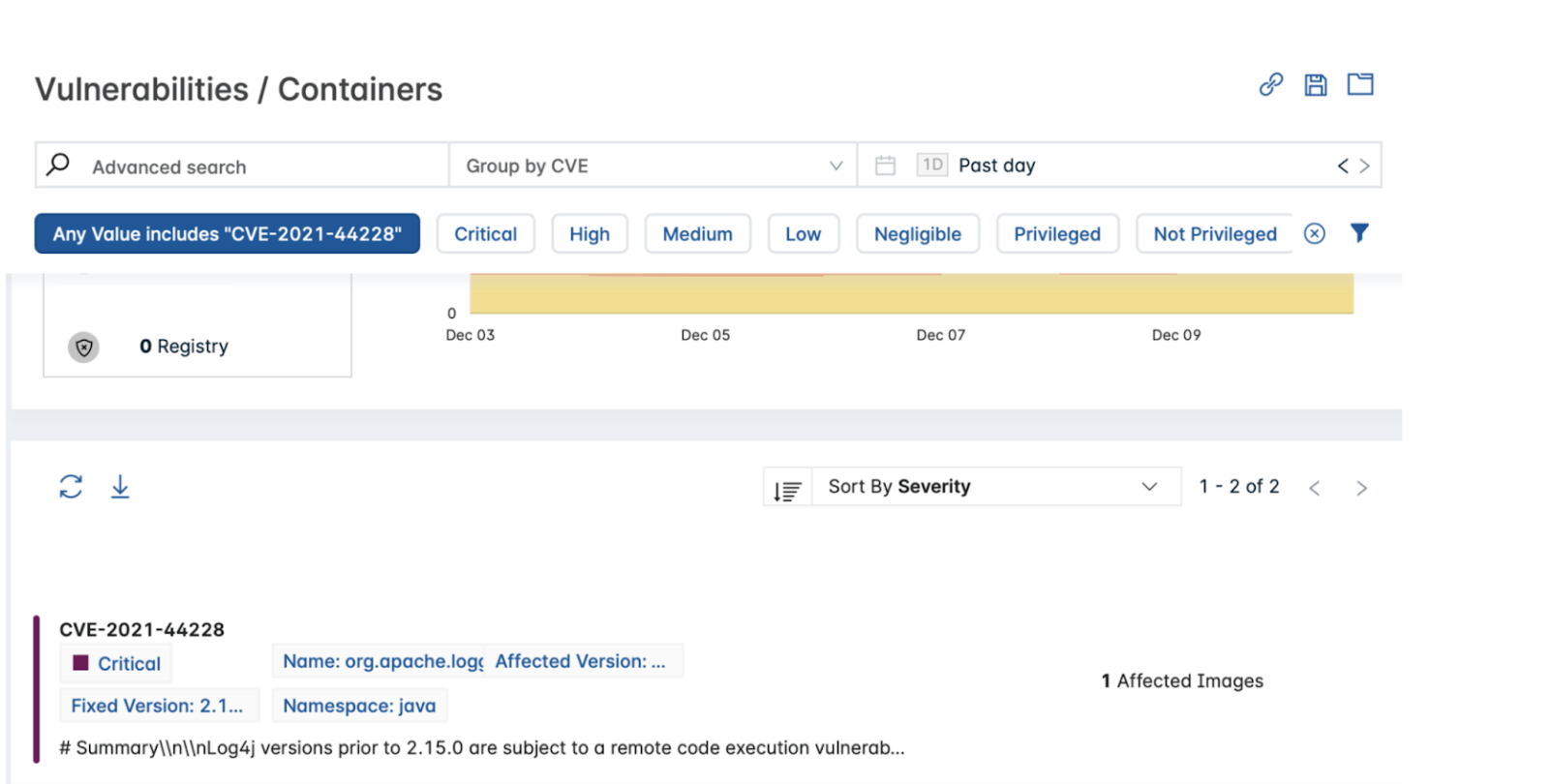
There are multiple ways that this vulnerable package can be installed, either through the OS vendor itself (for example, apache-log4j2 in Debian), or directly within Java (for example, org.apache.logging.log4j:log4j-core).
The Github Security Advisory states that the previous version "Log4J v1 is End Of Life (EOL) and will not receive patches for this issue. Log4J v1 is also vulnerable to other remote code execution (RCE) vectors and we recommend you migrate to Log4J v2.15.0 where possible."
important
UPDATE: Apache updated its guidance on December 18, 2021. Log4j v2.15.0 and v2.16.0 are still affected. Upgrade to v2.17.0.
Detecting this vulnerability in containers
- Ensure registry integrations have Non-OS Package Support enabled. As of v4.42 (December 16), all registry integrations were enabled for non-OS package support.
- Ensure that in Settings > General, you have enabled Reassess active images.
- Ensure that for proxy scanner configurations, you are setting
disable_non_os_package_scanning: false. If this field is omitted, the default is false. - Ensure that your Inline Scanner(s) are configured to scan non-OS programming languages. The
--scan-library-packagesflag can also be used when running theimage evaluatecommand.
note
If you have images older than 30 days and had not enabled non-os package scanning, we recommend you re-trigger scans for those older images via on-demand scan or inline scanner. With the v4.42 release (December 16th), all images that were active in the past 7 days and created after November 16th were automatically re-scanned on your behalf.
Detecting this vulnerability in hosts
Lacework will detect CVE-2021-44228 if the package was installed through the OS package manager. However, if the package is a Java dependency, Lacework will NOT detect it. We recommend checking the installed packages on your hosts.
Detecting potential resulting exploits in run time
CVE-2021-44228 is a remote code execution (RCE) vulnerability and, at run time, exploits can be used to take complete control of applications as well as containers. However, an exploited workload will show signs of network activity from unknown servers or could show unusually heavier activity from known sources.
Lacework's anomaly detection techniques allow customers to identify unusual network activities that can be investigated with the Polygraph visual representations, or through events originating from hosts or containers impacted by such vulnerabilities.
Lacework Labs will be monitoring for post-exploit activity, including historical data. We will provide specific recommendations to customers if a compromise is detected.
What is the recommended remediation?
It is critical that you upgrade Apache Log4j to version v2.17.0 as soon as possible to remediate this vulnerability.