Product Enhancements for Log4j
Overview
Lacework adds a new Beta capability to directly address log4j detection requirements. With a combination of agent v5.1 and platform v4.42, Lacework now detect instances of long-running, vulnerable log4j processes on both hosts and containers at runtime. If a vulnerable processes is detected, it is presented as a High Severity event in the Lacework Platform. Most importantly, Lacework now correlates abnormal application activity with vulnerable log4j packages, generating composite events with increased severity, making it easier for you to find exploit activity.
This Beta capability is designed to enhance Lacework's ability to detect log4j attacker behavior.
Agent Configuration
Enhanced log4j capabilities are enabled by default with Lacework Agent v5.1 (Agent Release Notes)
New Event Types
The following event types have been added to reflect activity associated with vulnerable log4j processes.
| Existing Event Type | New Event Type with Vulnerability Addition | Severity |
|---|---|---|
| NewExternalServerBadDNSConn | NewExternalServerBadDNSConnFromVuln | Critical |
| NewExternalClientBadIpConn | NewExternalClientBadIpConnToVuln | Critical |
| NewExternalServerBadIPConn | NewExternalServerBadIPConnFromVuln | Critical |
| NewChildLaunched | NewChildLaunchedFromVulnParent NewVulnChildLaunched | High |
| NewExternalClientConn | NewExternalClientIpConnToVuln | High |
| NewExternalServerDNSConn | NewExternalServerDNSConnFromVuln | High |
| NewExternalServerIPConn | NewExternalServerIPConnFromVuln | High |
| UserLaunchedNewBinary | UserLaunchedNewVulnBinary | High |
| NewBinaryType | NewVulnBinaryType | Medium |
| NewInternalConnection | NewVulnInternalConnection | Medium |
The following is an example new event type (shown for reference):
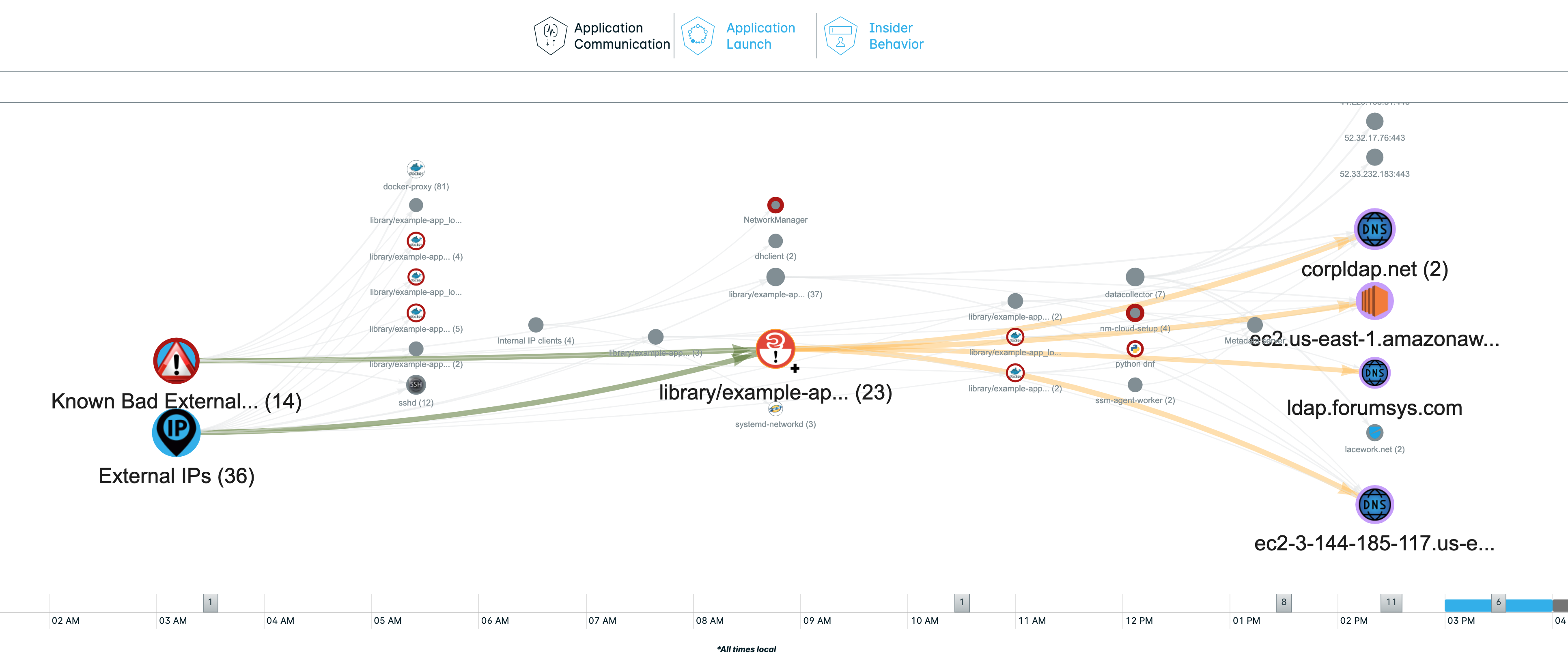
How to change the set of hashes that are monitored for log4j vulnerability
If the file /var/lib/lacework/config/log4j.config.json is present in your system, the Lacework agent reads it and uses this information as well
as the built-in set of hashes.
The log4j.config.json file must be a well formed json file with a single array element, where each array member is an object that describes a single hash.
Each object should have the fields:
- Sha256 - Cryptographic hash function
- Version - This field is optional - it provides additional information when the issue is detected.
- Name - This field is required if
Enabled: trueand optional ifEnabled: false. - Enabled - If
Enabledistrue, then the Lacework agent looks for files with this Sha256 hash. If it isfalse, then it does not look for the hash, even if it is a built-in hash.
See the following example:
{"Sha256":"ABC","Version":"2.16.0","Name":"JndiContextSelector.class","Enabled":true},
{“Sha256":"DEF","Version":"2.16.0","Name":"JndiContextSelector.class","Enabled":true},
{"Sha256":"XYZ","Version":"2.0-alpha1","Name":"LoggerContext.class","Enabled":false}
note
For v5.4.1 and earlier, you must restart the agent after updating the set of hashes in the configuration file to enable the changes to take effect.
FAQs
Which Log4j CVEs does Lacework detect?
All three CVEs published as of Tuesday, December 21st. CVE-2021-44228, CVE-2021-45046, and CVE-2021-4104
Does the agent look for environment variable and configuration-based log4j vulnerability mitigations to prevent false positive detection?
No, the agent will detect vulnerable version of log4j and use this data in combination with polygraph detection. Various configuration-based mitigations have been found to be ineffective, so polygraph data is used to reduce the potential for false positives.
How do I know exactly where log4j is installed?
The agent detects if a vulnerable log4j exists anywhere in a process. If Lacework is detecting an anomaly related to a vulnerable log4j installation, please work with your customer support representative to help find the root cause of the detection.
What are the visibility gaps associated with this detection method?
The main visibility gaps are timing-related (if a process is executed and then terminated prior to the agent scan).
How often does the agent scan processes for vulnerabilities?
Every 12 hours, but this setting is configurable to enable you to make your own tradeoffs between performance and efficacy.