Custom Compliance Policies
This walkthrough takes you through the steps to use the Lacework CLI to create a custom compliance policy and adding that policy to a custom report. A compliance policy evaluates resource configuration in your integrated cloud environments with results appear in a daily report. For more information about compliance policies, see Custom Policy Types.
The following steps provide a basic end-to-end workflow to create a custom compliance policy. For additional options when creating queries and policies, see LQL Queries and Policies. Also, this walkthrough omits steps for exploring the data. For a complete end-to-end walkthrough, see CLI Custom Policies.
Create a Query
Open your text editor, create a new file, and add the following content:
Compliance queryqueryId: LW_Custom_UnrestrictedIngressToTCP3349
queryText: |-
{
source {
LW_CFG_AWS_EC2_SECURITY_GROUPS securityGroup,
array_to_rows(securityGroup.RESOURCE_CONFIG:IpPermissions) as ip_permissions,
array_to_rows(ip_permissions:IpRanges) as ip_ranges
}
filter {
ip_permissions:IpProtocol = 'tcp'
and ip_permissions:FromPort = 3349
and ip_permissions:ToPort = 3349
and ip_ranges:CidrIp = '0.0.0.0/0'
}
return distinct {
'This is the compliance reason' as COMPLIANCE_FAILURE_REASON
}
}Save the file as YAML with the filename LW_Custom_UnrestrictedIngressToTCP3349.yaml. Note the file's location.
In the Lacework CLI, run this command:
lacework query create -f <path_to>/LW_Custom_UnrestrictedIngressToTCP3349.yamlThe following response appears:
The query LW_Custom_UnrestrictedIngressToTCP3349 was created.
Create a Policy
In your text editor, create a new file, and add the following content:
Compliance policy---
title: Security Groups Should Not Allow Unrestricted Ingress to TCP Port 3349
enabled: true
policyType: Compliance
alertEnabled: true
queryId: LW_Custom_UnrestrictedIngressToTCP3349
description: Security groups should not allow unrestricted ingress to TCP port 3349
remediation: Policy remediation
severity: mediumSave the file as YAML with the filename LW_Custom_UnrestrictedIngressToTCP3349_Policy.yaml. Note the file's location.
In the Lacework CLI, run this command:
lacework policy create -f <path_to>/LW_Custom_UnrestrictedIngressToTCP3349_Policy.yamlThe following response appears:
The policy dev-default-75 was created.
Enable Reports
The policy you just created is not a part of any report yet. Add it to a custom report as follows.
In your text editor, create a new file, and add the following content:
Custom report{
"reportName": "Test AWS Compliance 1.0 based on NIST 800-171 v2",
"reportType": "COMPLIANCE",
"subReportType": "AWS",
"reportDefinition": {
"sections": [
{
"category": "3.1.1",
"policies": [
"dev-default-75",
"lacework-global-40",
"lacework-global-45",
"lacework-global-485",
"lacework-global-88"
],
"title": "3.1.1: Limit system access to authorized users, processes acting on behalf of authorized users, and devices (including other systems)"
},
{
"category": "3.1.2",
"policies": [
"lacework-global-34",
"lacework-global-45",
"lacework-global-485",
"lacework-global-486"
],
"title": "3.1.2: Limit system access to the types of transactions and functions that authorized users are permitted to execute"
},
{
"category": "3.1.4",
"policies": [
"lacework-global-44",
"lacework-global-70"
],
"title": "3.1.4: Separate the duties of individuals to reduce the risk of malevolent activity without collusion"
}
]
}
}The report definition includes a name and a report type, COMPLIANCE in this case. Notice that custom policy listed in the first section,
dev-default-75. This generated report will include the custom policy along with the listed default policies. For descriptions of the other fields in this request body, see the Reports Definition API.Save the file with the filename LW_Custom_UnrestrictedIngressToTCP3349_Report.json. Note the file's location.
In the Lacework CLI, run this command:
lacework api post '/ReportDefinitions' -d "$(cat LW_Custom_UnrestrictedIngressToTCP3349_Report.json)"
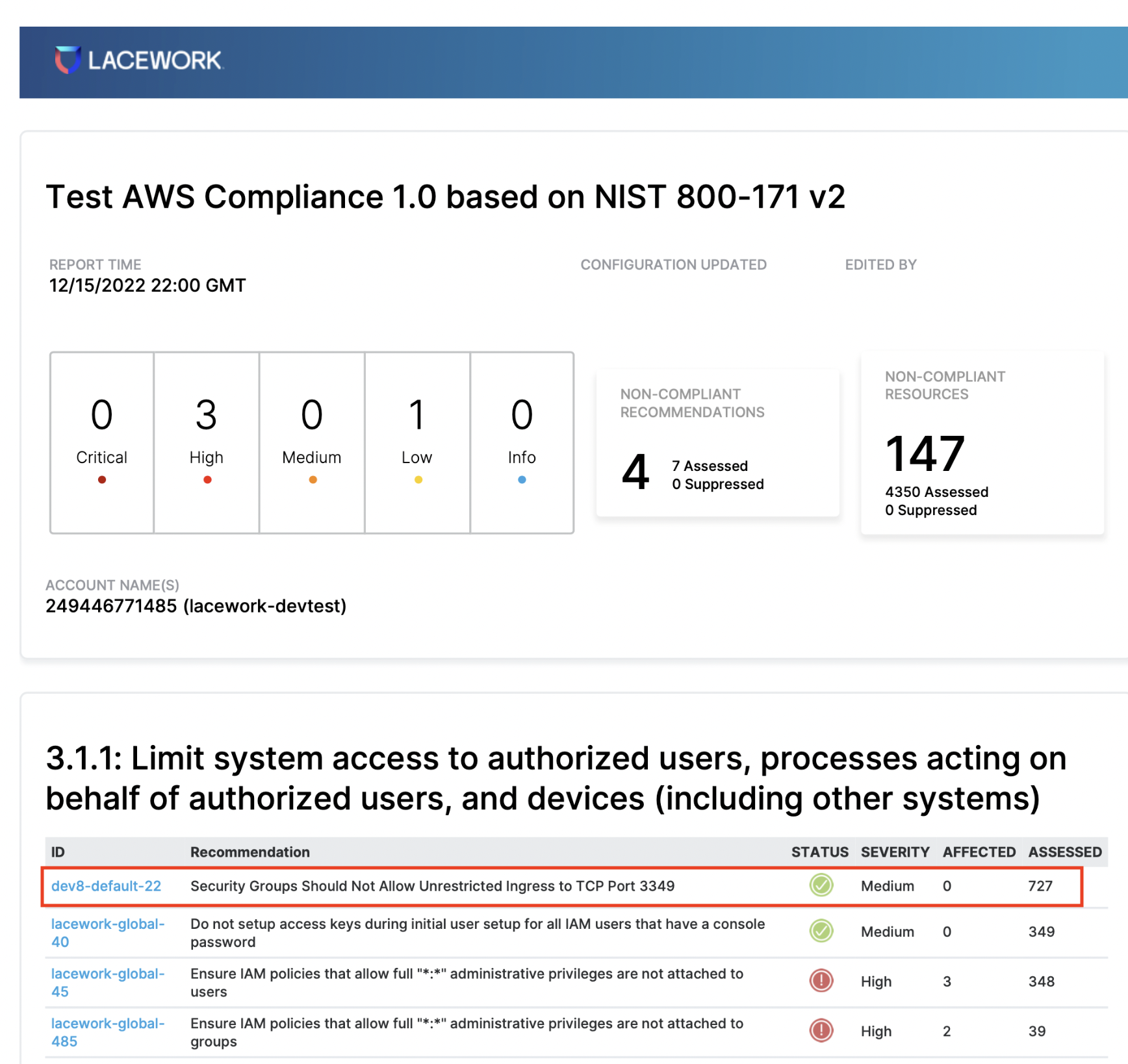
The compliance policy is now listed in the cloud compliance page, and appears in the next daily compliance report: