Amazon Security Lake
Lacework can integrate with Amazon Security Lake, a security data lake that is based on the OCSF standard. Lacework integrates as a security data source and provides real-time security findings. These security findings include software and infrastructure-as-code (IaC) vulnerabilities, cloud resource security misconfigurations, and security threat detections.
How it Works
This solution sends Lacework security findings to Amazon Security Lake. Lacework security findings are sent to Amazon EventBridge and then delivered to Amazon SQS queue. A Lambda function receives these security findings from the queue and then transforms them into OCSF format for delivery to the Amazon Security Lake S3 bucket as Parquet formatted files. The Amazon Security Lake Service then ingest these files and their Lacework security findings. The following shows the architecture of this solution.
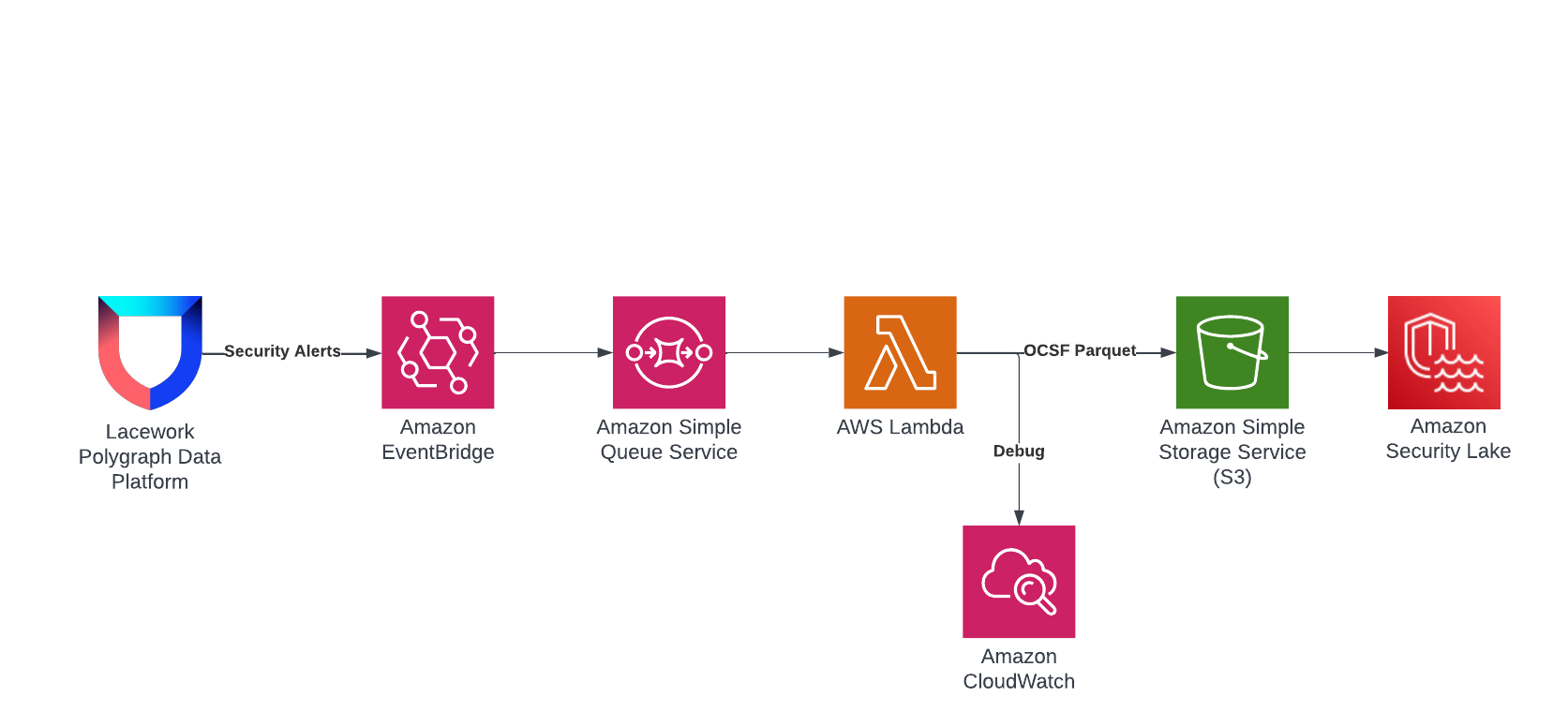
CloudFormation Deployment
CloudFormation is used to set up the Lacework integration with Amazon Security Lake. The CloudFormation template creates the EventBridge rules, IAM permissions, SNS topic, SQS queue, Lambda event transformation function and the Lacework outbound security alert channel.
Prerequisites
- Amazon Security Lake Custom Source for Lacework. Choose the Custom sources menu in the Amazon Security Lake console to set up a Lacework custom source.
- Administrator access to a Lacework instance
- Lacework Admin API Key and Secret
Deploy the CloudFormation Template
Click on the following Launch Stack button to go to your CloudFormation console and launch the template.

For most deployments, you only need the Basic Configuration parameters.
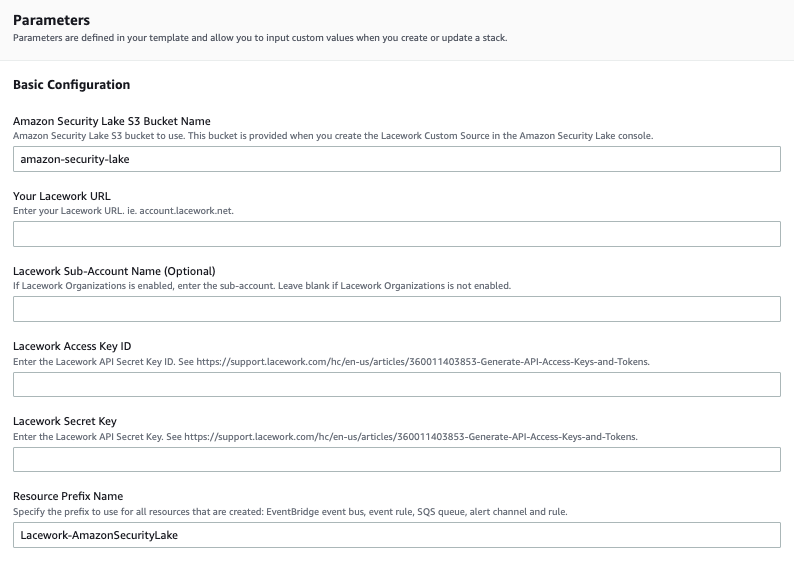
Specify the following Basic Configuration parameters:
- Enter a Stack name for the stack.
- Enter the Amazon Security Lake S3 Bucket Name. Enter the S3 bucket name that was provided to you when you set up the Amazon Security Lake Custom Source for Lacework.
- Enter Your Lacework URL.
- If your Lacework instance has the Organization feature enabled, enter the Lacework Sub-Account Name. Otherwise, leave this field blank.
- Enter your Lacework Access Key ID and Lacework Secret Key that you copied from your API Keys file. See Generate API Access Keys and Tokens.
Click Next through to your stack Review.
Accept the AWS CloudFormation terms and click Create stack.
S3 Data Retention
The Amazon Security Lake S3 bucket that is provided to you when you create your custom resource is created in your AWS account. You may want to configure a data retention policy and automatically delete data after a period of time. This can be achieved through a S3 Lifecycle expiration rule. Read S3 - Managing your storage lifecycle to learn how to configure this.
Troubleshooting
Troubleshooting this integration can be done by monitoring the CloudWatch logs for two Lambda functions. One Lambda function is responsible for the initial setup during the CloudFormation deployment. The second Lambda function transforms Lacework security alerts to the OCSF security findings for Amazon Security Lake. For additional assistance, contact your Lacework support contact or use the Lacework Support link above.
Initial Setup Troubleshooting
Some initial set up during the CloudFormation deployment is handled by a Lambda function stack-name-LaceworkAmazonSecurityLakeSetupFunction-xxxx. Specifically, it configures the Alert Channel and Alert Rules that are required to send Lacework Security Alerts to the second Lambda function for transformation into OCSF for Amazon Security Lake. To investigate any issues, use the following steps:
- Go to Lambda in your AWS management console.
- Find the Lambda function with the name stack-name-LaceworkAmazonSecurityLakeSetupFunction-xxxx.
- Click the Monitor tab.
- Click View logs in CloudWatch to launch CloudWatch into a new tab.
- View the Log stream debug for errors.
Security Findings Event Troubleshooting
If there are issues with Lacework Security Alerts being transformed to OCSF for Amazon Security Lake, investigate the Lambda function stack-name-LaceworkEventSetupFunction-xxxx. It transforms Lacework Security alerts into OCSF Security Findings format and delivers these in Parquet file format to the Amazon Security Lake S3 bucket. To investigate any issues, use the following steps:
- Go to Lambda in your AWS management console.
- Find the Lambda function with the name stack-name-LaceworkAmazonSecurityLakeEventFunction-xxxx.
- Click the Monitor tab.
- Click View logs in CloudWatch to launch CloudWatch into a new tab.
- View the Log stream debug for errors.
Updates
Updates to the integration including updates due to OCSF schema changes are provided through CloudFormation template updates. This may upgrade architecture and the Lambda functions.
AWS Infrastructure Costs
This integration utilizes S3, Lambda, EventBridge, SQS and Cloudwatch AWS Services. This integration will incur costs due to the use of the services. Costs will vary depending on the size of the environment and the number of security findings found in the environment. For reference, a typical environment with multiple AWS accounts will likely cost less than $1/day.