Configure iacbot
IaC Security provides the ability to view policy violations without blocking Pull Request/Merge Requests (PR/MR) despite failed policy checks. This capability can be configured at the organization level, where it applies to all repositories, or at the repository level (through settings within the repository's .lacework/config.yml file, which take precedence over the organization configuration).
At the repository level, you can customize the Configuration Options and Configuration Mode by editing the .lacework/config.yml file in your repository’s root directory. The repository Configuration Mode can also be updated through the UI. At the organization level, you can select a Configuration Mode through the UI.
Configuration Modes
Lacework IaC Security allows you to choose between two configuration modes: Audit and Enforce Status Check. Either mode scans repos and posts comments to PR/MRs. Audit Mode, the default mode, does not block pipelines or PR/MRs, whereas Enforce Status Check Mode blocks pipelines or PR/MRs.
note
Changes to the .lacework/config.yml file take precedence over the Lacework IaC Organization UI configuration. If there are differences between the two methods of choosing a mode, Lacework IaC Security is configured by the .lacework/config.yml file.
note
The configuration you see in the UI is the Organization-level config. The contents of the .lacework/config.yml file in the repository are not reflected in the UI.
Change the Configuration Mode Using the UI
- Go to app.soluble.cloud.
- Click Settings.
- Click Organization.
- On the right, select your desired configuration mode.
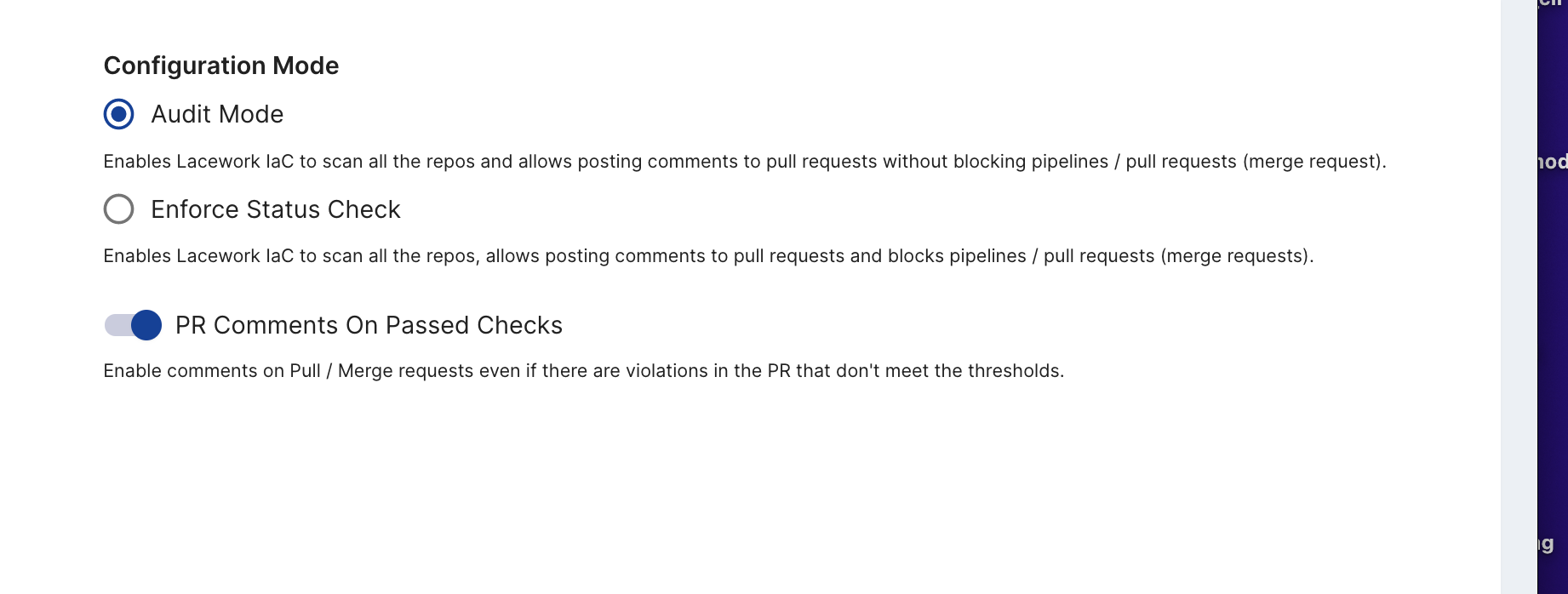
- Click the toggle to enable or disable comments on pull/merge requests.
- For new customers, this setting is enabled by default.
note
In earlier releases, comments were only made for Critical/High violations. The current release creates comments, if enabled, for all violations regardless of severity. This informs you of new violations even when they do not block your PR/MR.
Change the Configuration Mode by Editing the .lacework/config.yml File
Audit Mode (default)
Audit mode enables the Lacework IaC bot to scan all repositories and allow posting comments to Pull Requests without blocking pipelines or Pull/Merge Requests.
The values in this yaml file override the defaults, so you need not specify all values in each repository. You can just edit the values that you want to override.
# Not all values need to be explicitly set.
# Should iacbot update your PR Status Check
pr_status_enabled: true
# Maximum allowable findings, above which
# PR status check will fail
pr_status_thresholds:
critical: 0
high: 0
medium: 999
low: 999
# Force the status check to pass. Checks will still be run.
# Effectively the same as raising thresholds to high values.
pr_status_force_pass_enabled: true
# Set to true if you want iacbot to add PR comments
pr_comments_enabled: true
# If set to true, a PR comment will be added, even if
# the status check passes.
pr_comments_on_passed_check_enabled: true
Enforce Status Check Mode
Enforce Status Check mode enables Lacework IaC Security to scan all repos and post comments to pull requests. This mode blocks pipelines and PR/MRs.
The values in the config.yaml file override the defaults, so you need not specify all values in each repository. You can just edit the values that you want to override.
# Not all values need to be explicitly set.
# Should iacbot update your PR Status Check
pr_status_enabled: true
# Maximum allowable findings, above which
# PR status check will fail
pr_status_thresholds:
critical: 0
high: 0
medium: 999
low: 999
# Force the status check to pass. Checks will still be run.
# Effectively the same as raising thresholds to high values.
pr_status_force_pass_enabled: false
# Set to true if you want iacbot to add PR comments
pr_comments_enabled: true
# If set to true, a PR comment will be added, even if
# the status check passes.
pr_comments_on_passed_check_enabled: true
IaC Bot Status Check & PR Comments
The following table details iacbot behavior on pull/merge requests. For example, if you run the iacbot in Audit Mode with 3 violations of differing severity, the pull/merge request will "pass" but will notify you through PR comments that there were 3 violations. In Enforce Status Check for the same scenario, the pull/merge will fail but still notify you of the 3 violations.
| Number | Mode | Scenarios | PR Status | PR Status Message | PR Comments | Config |
|---|---|---|---|---|---|---|
| 1 | Audit Mode | Critical: 0, High: 0, Medium: 0, Low: 0. | (Audit Mode) No violations found | No | C: 0, H: 0, M:99999, L: 99999 | |
| 2 | Enforce Static Check | Critical: 0, High: 0, Medium: 0, Low: 0. | No violations found | No | C: 0, H: 0, M:99999, L: 99999 | |
| 3 | Audit Mode | Critical: 1, High: 1, Medium: 1, Low: 0. | (Audit Mode) Failed - Found 3 violations in this pull request | Yes | C: 0, H: 0, M:99999, L: 99999 | |
| 4 | Enforce Static Check | Critical: 1, High: 1, Medium: 1, Low: 0. | Failed - Found 3 violations in this pull request | Yes | C: 0, H: 0, M:99999, L: 99999 | |
| 5 | Audit Mode | Critical: 0, High: 0, Medium: 1, Low: 0. | (Audit Mode) Passed - Found 1 violations in this pull request | Yes | C: 0, H: 0, M:99999, L: 99999 | |
| 6 | Enforce Static Check | Critical: 0, High: 0, Medium: 1, Low: 0. | Passed - Found 1 violations in this pull request | Yes | C: 0, H: 0, M:99999, L: 99999 | |
| 7 | Audit Mode | Critical: 0, High: 0, Medium: 1, Low: 0. | (Audit Mode) Failed - Found 1 violations in this pull request | Yes | C: 0, H: 0, M:0, L: 99999 | |
| 8 | Enforce Static Check | Critical: 0, High: 0, Medium: 1, Low: 0. | Failed - Found 1 violations in this pull request | Yes | -C: 0, H: 0, M:0, L: 99999 |
Examples of IaC Bot Status Check & PR Comments
In the following examples, both pull/merge requests include the same medium severity violation. In Audit Mode, the PR will pass regardless of its violation(s). The PR comments will alert you to how many violations exist, but you can still merge the PR. In Enforce Status Check Mode, the pull/merge request will fail and block the pull/merge request if any critical or high violation(s) exist in the PR. PR comments will detail the violations
GitLab
| Mode | PR Comments |
|---|---|
| Audit Mode (default) | 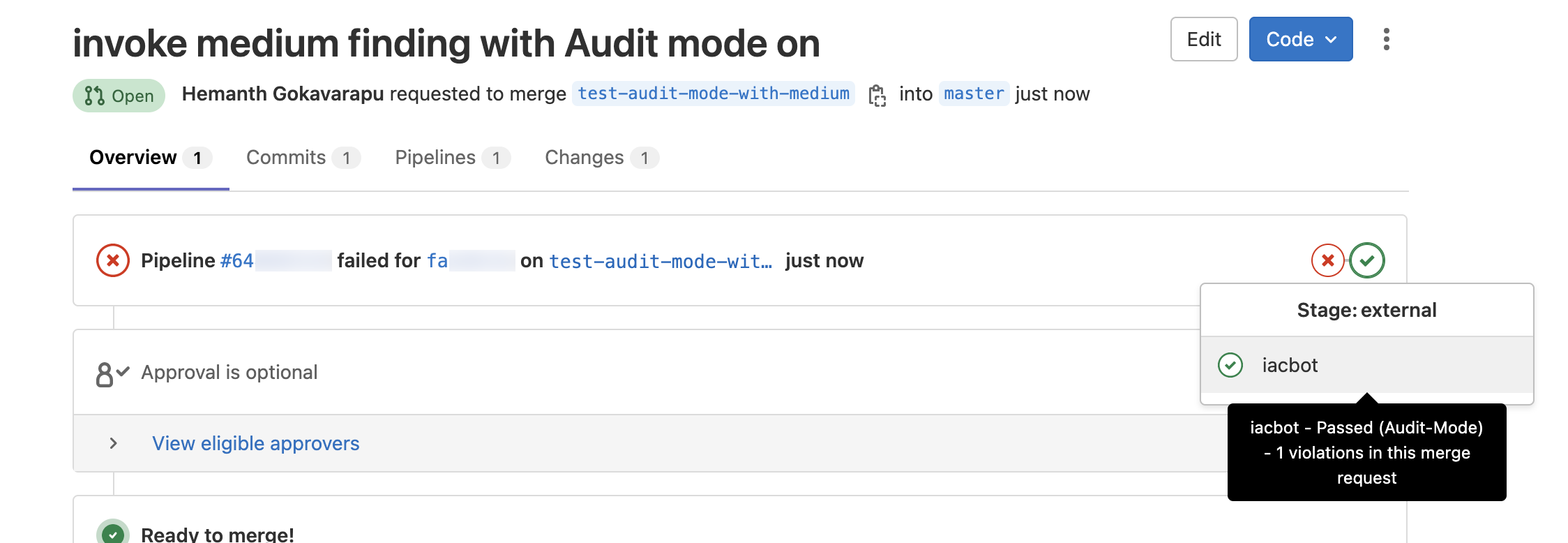 |
| Enforce Status Check Mode | 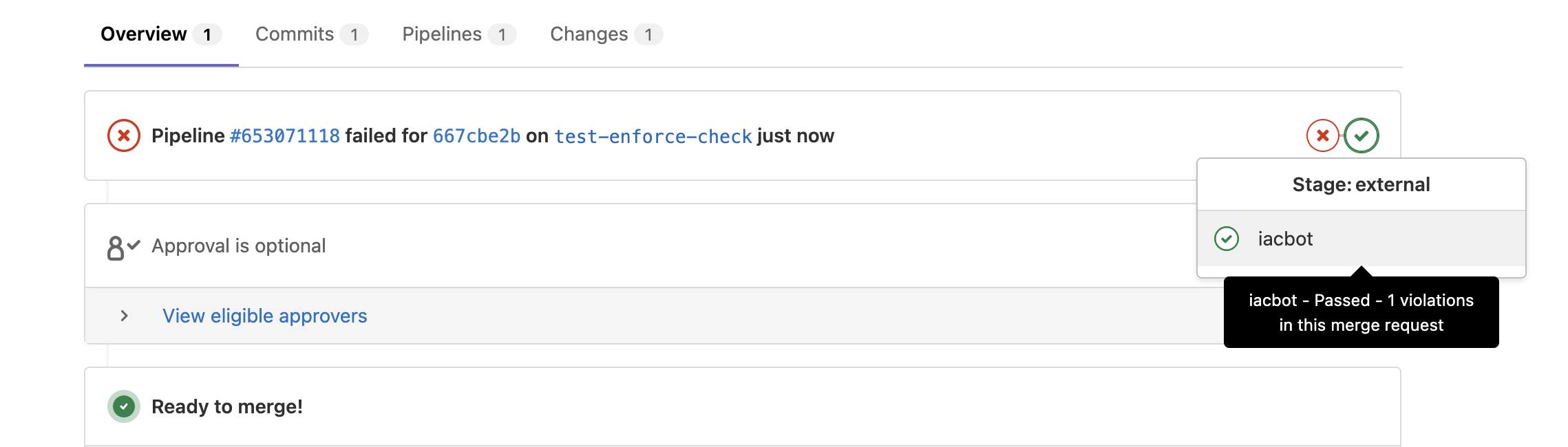 |
Bitbucket
| Mode | PR Comments |
|---|---|
| Audit Mode (default) | 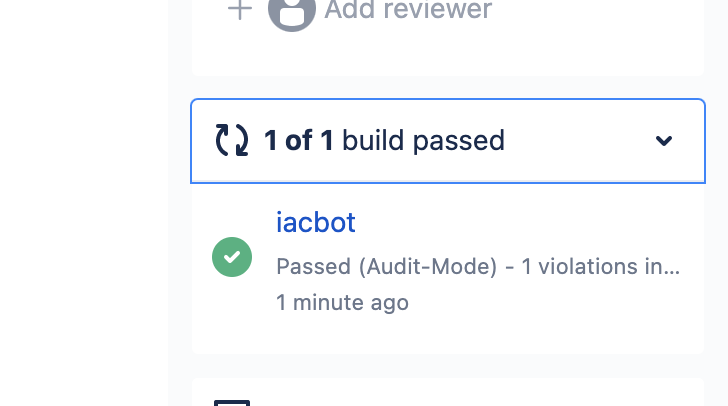 |
| Enforce Status Check Mode | 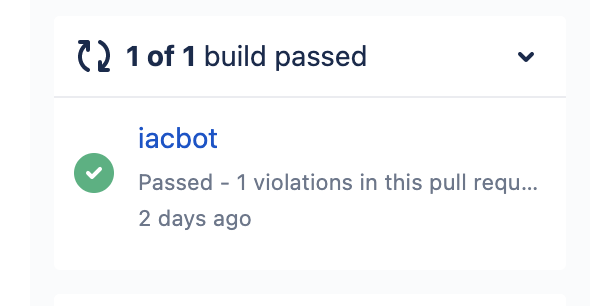 |
GitHub
| Mode | PR Comments |
|---|---|
| Audit Mode (default) | 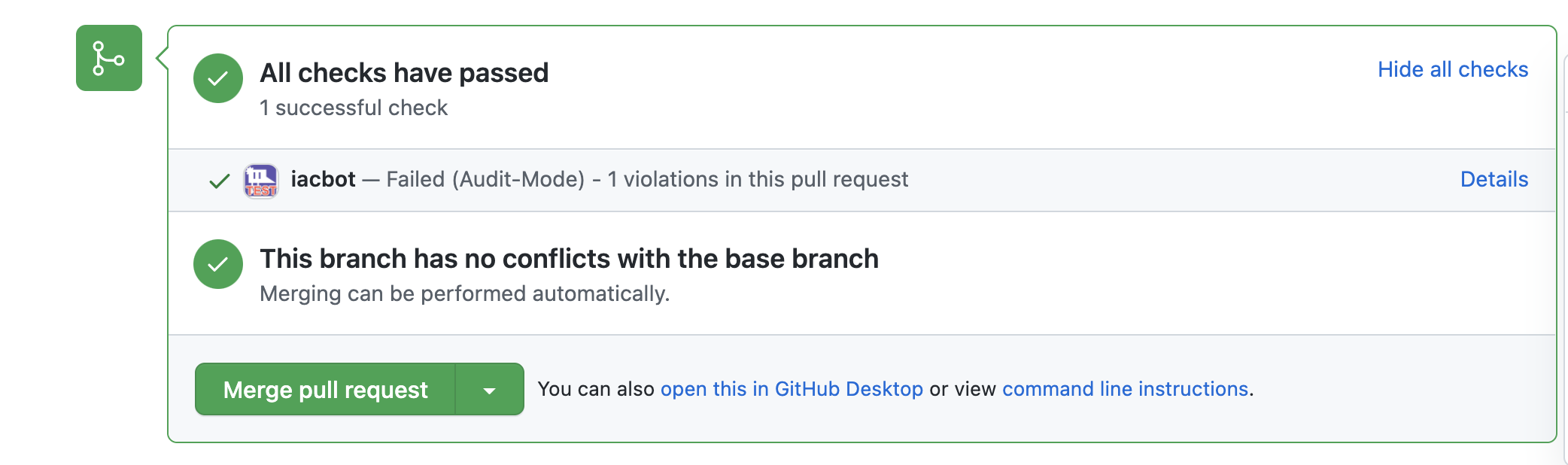 |
| Enforce Status Check Mode | 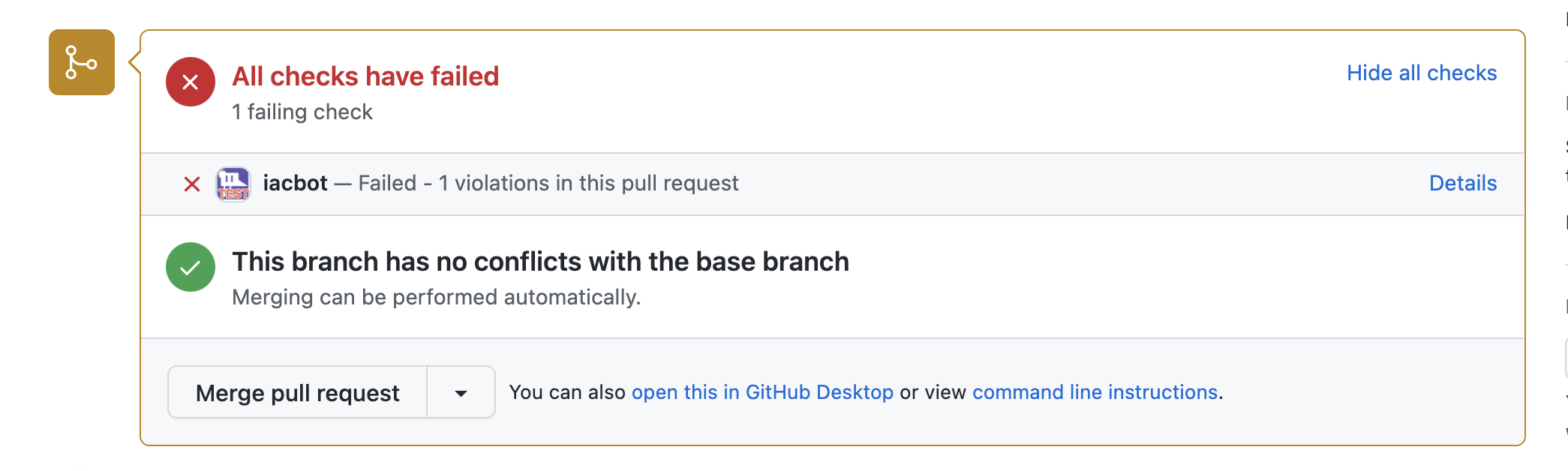 |
Configuration Options
Ignore Files
The ignore directive takes a list of strings, which are interpreted using gitignore syntax.
Example:
ignore:
- "test/**"
- "some-other-file"
note
Currently this directive only applies to assessments uploaded to IaC Security. The ignore directive will not be applied to local CLI output.
Suppress Findings
The suppress directive takes a list of strings that are matched against the sid for a particular finding.
Example:
suppress:
- "sid-1"
- "sid-2"
note
Currently this directive only applies to assessments uploaded to IaC Security. The suppress directive will not be applied to local CLI output.
Prevent Submodule Scans
If you are not interested in scanning the submodules of a repository, you can add the following flag in the repository’s .lacework/config.yml file:
scan_git_submodules_enabled: false
This prevents IaC Security from scanning the submodules.
Manual Trigger
Lacework IaC Security users can also ad hoc trigger the iacbot on any of their repositories using the trigger option available on the repository.