Get Started with IaC Security
To get started with Lacework IaC Security, connect the iacbot to your git provider.
Get Started with GitHub
Prerequisites
To install iacbot, you need admin-level access to all the repositories you plan to integrate. You can select some or all of the repositories for monitoring. You can also install iacbot directly from the GitHub marketplace.
Ensure that the GitHub iacbot application is installed for each organization. To verify this, go to the GitHub iacbot App and make sure that the app is correctly installed.
Permissions
To ensure you have the correct permissions and authorization needed to configure the iacbot, go to the GitHub Application Settings.
Under the "Authorized OAuth Apps" tab, select "Lacework IaC Security" and verify that the GitHub organization is granted access.
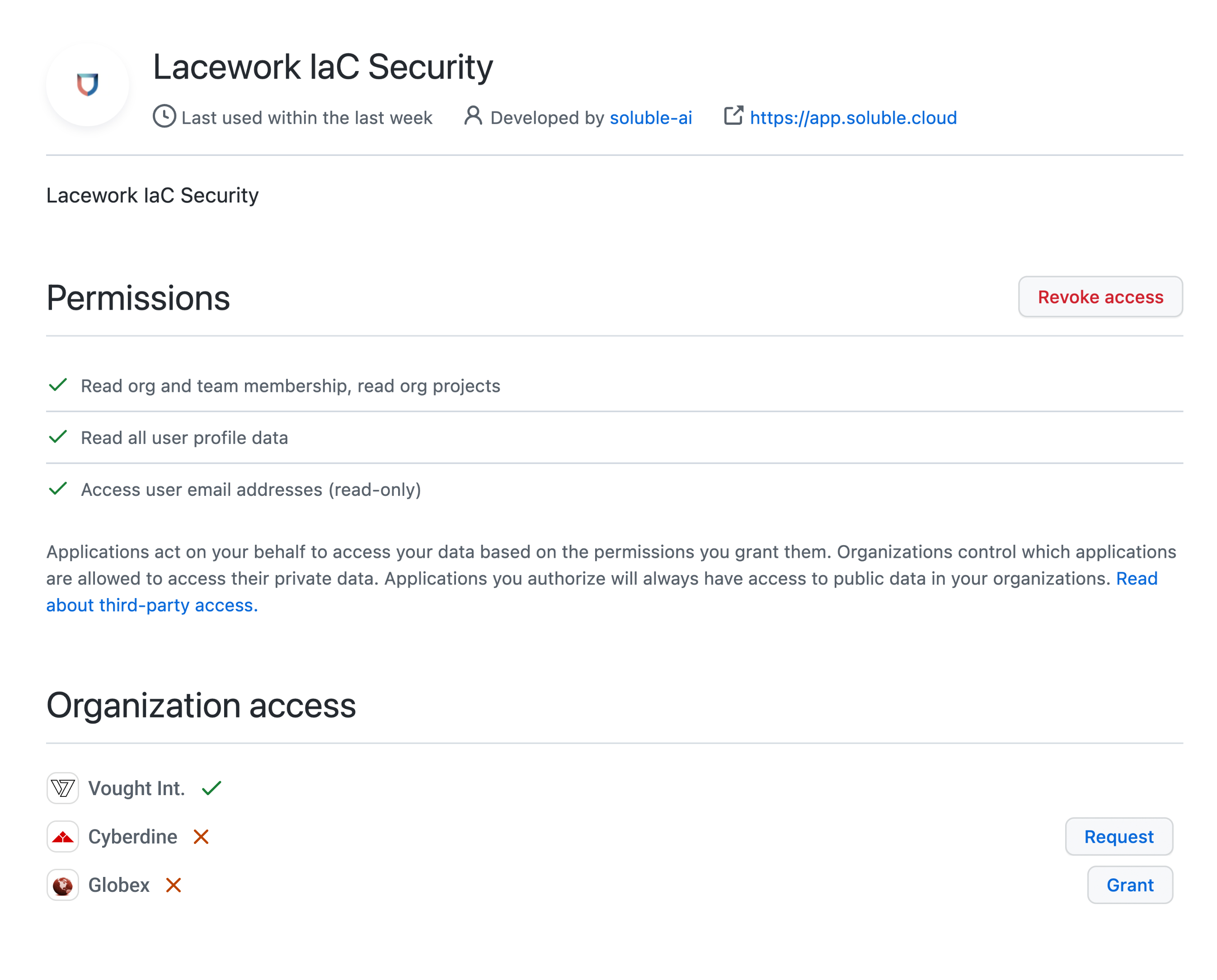
Click Grant next to your Organization (as shown above). After you have done that, you will need to sign out and sign back in to Lacework IaC Security.
Configure the iacbot with GitHub
Go to the Lacework IaC Security page.
Select GitHub as your provider.
Go to https://github.com/apps/iacbot and click Configure.
Select the Organization for which you want to install the iacbot.
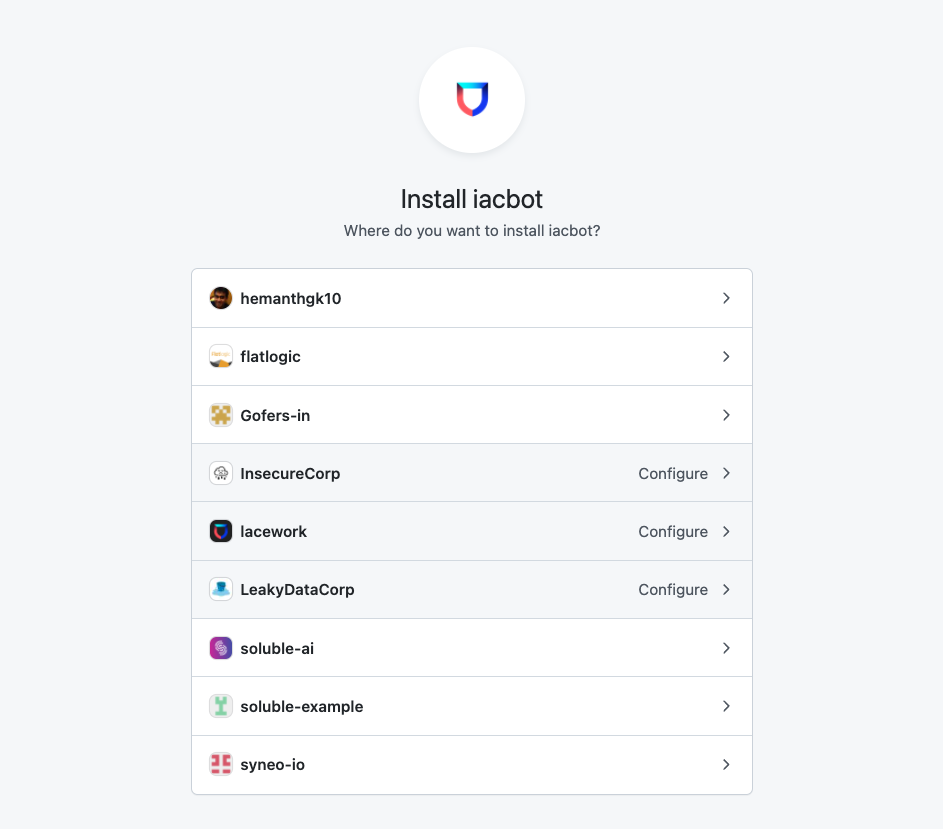
- Ensure you have assigned each organization the correct permissions.
Review and authorize iacbot for a selected few or all repositories.
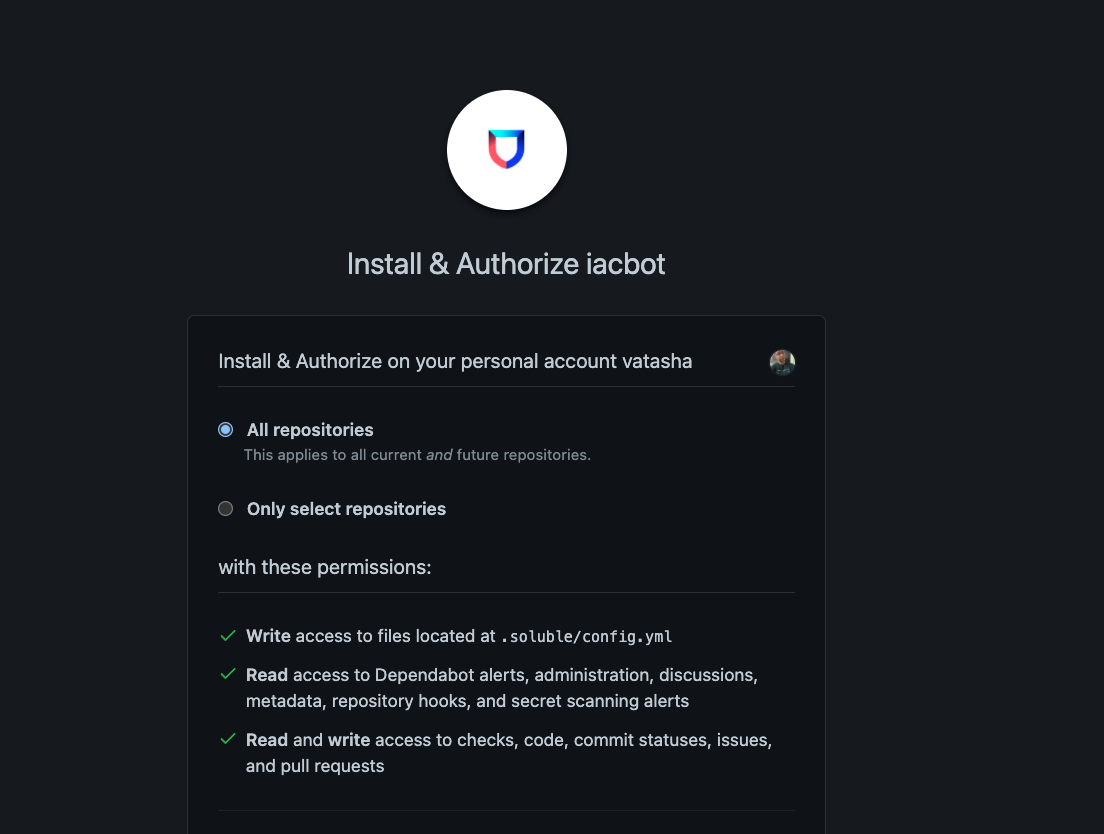
Accept the Terms of Service.
At this point, iacbot is analyzing your repos. It looks for Terraform, CloudFormation, Kubernetes, and other IaC Languages (see Language Support for details). When it finds IaC source code, it initiates a static analysis of your code.
As soon as the first assessment is complete, you should see this message:
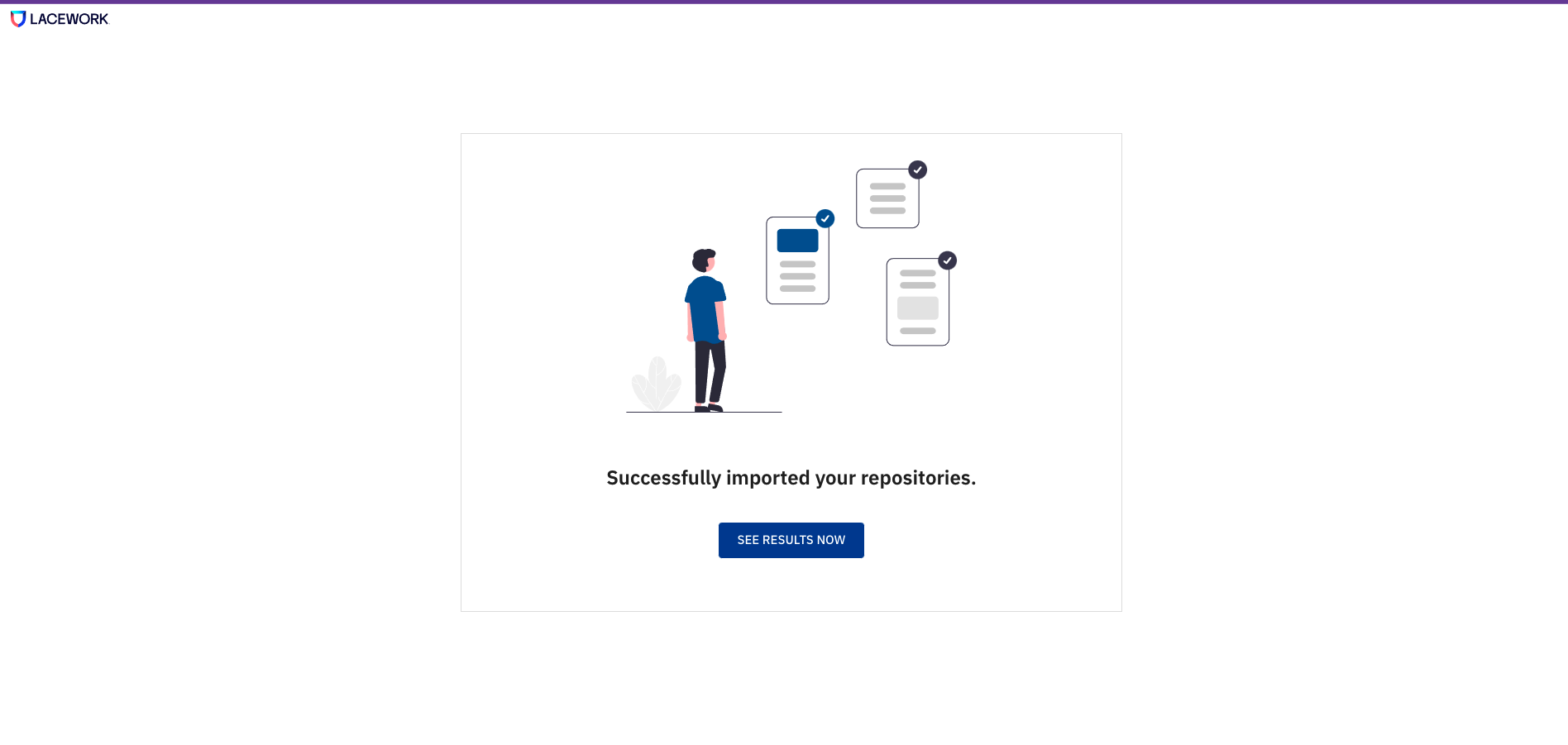
Get Started with GitLab
Prerequisites
To install iacbot, you need a service account with an Owner or Maintainer role and the scopes api, read_repository, openid, read_user and email.
Configure the iacbot with GitLab
Go to the Lacework IaC Security page.
Select GitLab as your provider.
Log in to GitLab.
Accept the Terms of Service.
Each
Groupin GitLab corresponds to an organization in Lacework IaC. Select a group from the dropdown to change which organization is being integrated.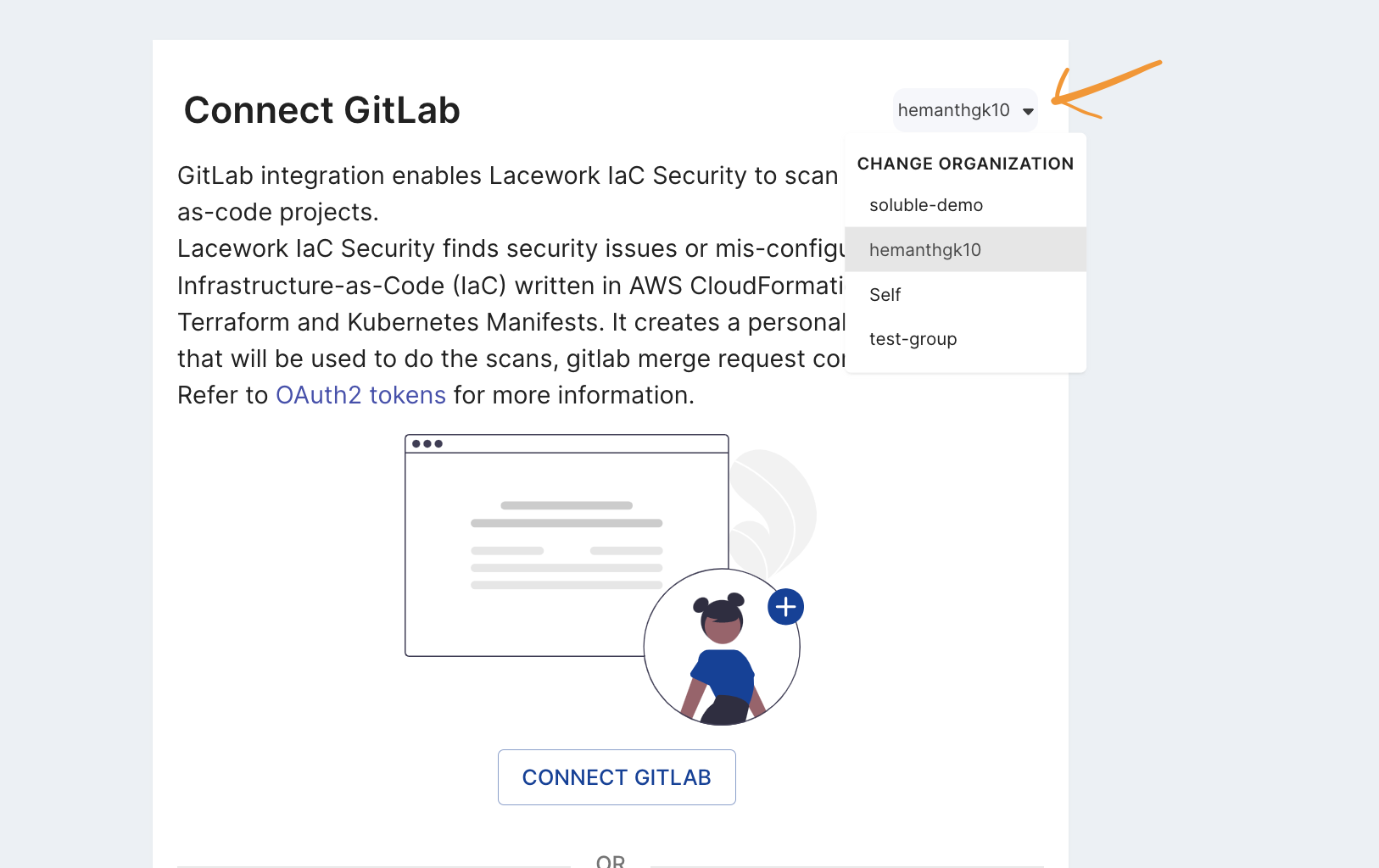
Create the Service Account token with the required roles and scopes mentioned in the prerequisites for the GitLab group which you want us to scan. Configure the service account access token and click
CONNECT GITLAB.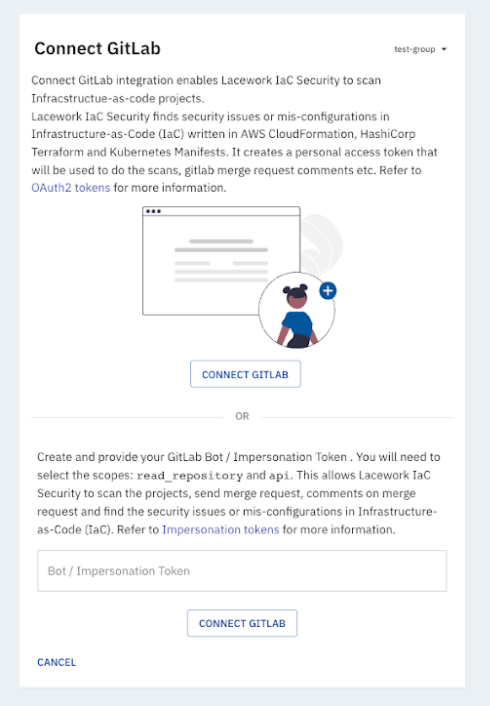
At this point, iacbot is analyzing your repos. It looks for Terraform, CloudFormation, Kubernetes and other IaC Languages (see Language Support for details). When it finds IaC source code, it initiates a static analysis of your code.
As soon as the first assessment is complete, you should see the following message:
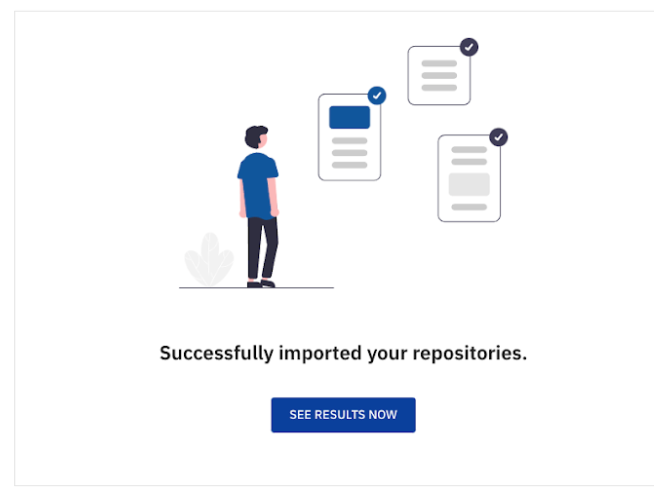
note
If you require an IaC Security integration with on-premise tools (for example, GitLab or GitHub), contact your Lacework representative.
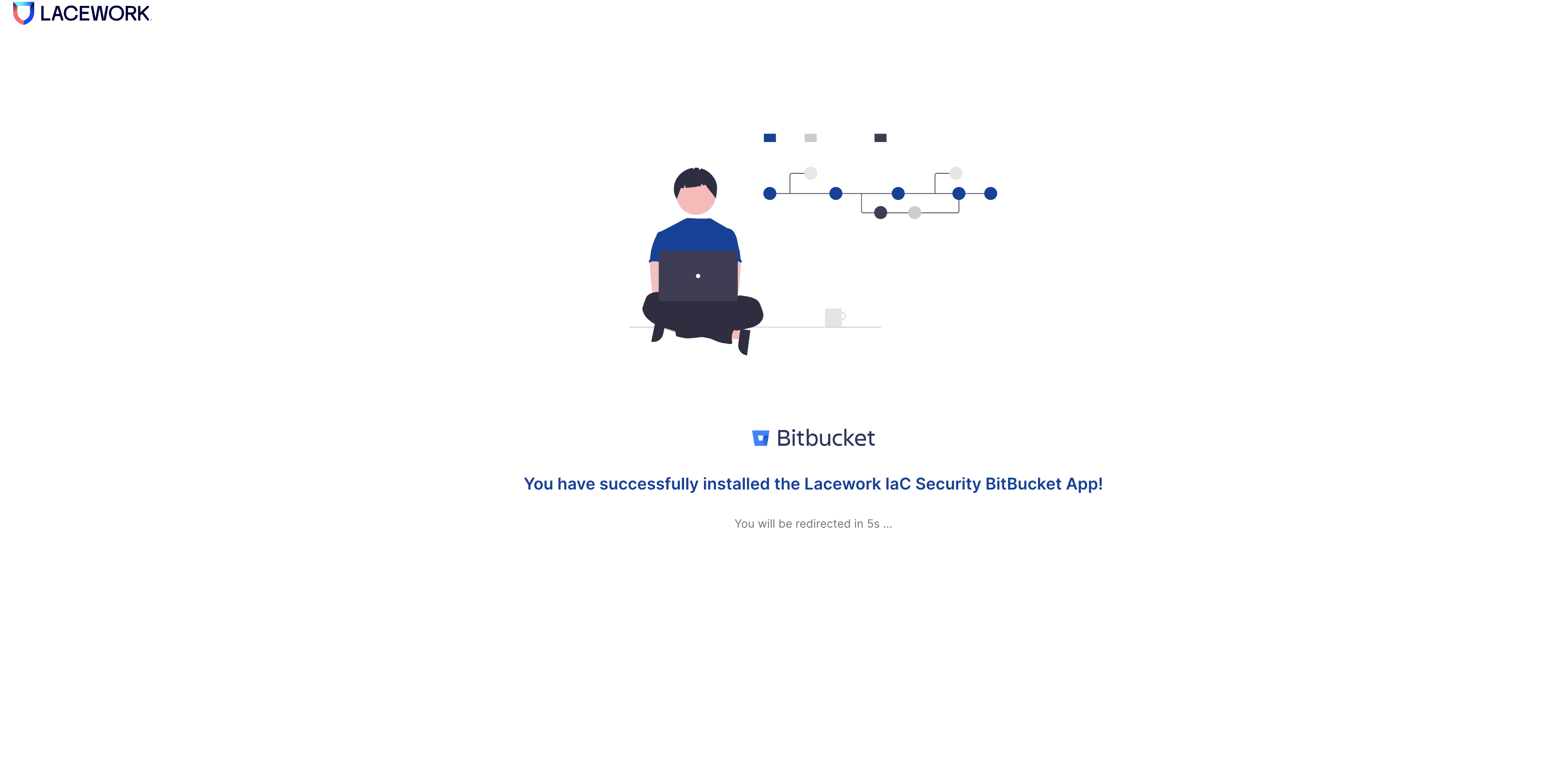
Get Started with Bitbucket
Prerequisites
To install iacbot, you need admin-level access to all of your integrated organization's repositories.
Configure iacbot with Bitbucket
Go to the Lacework IaC Security page.
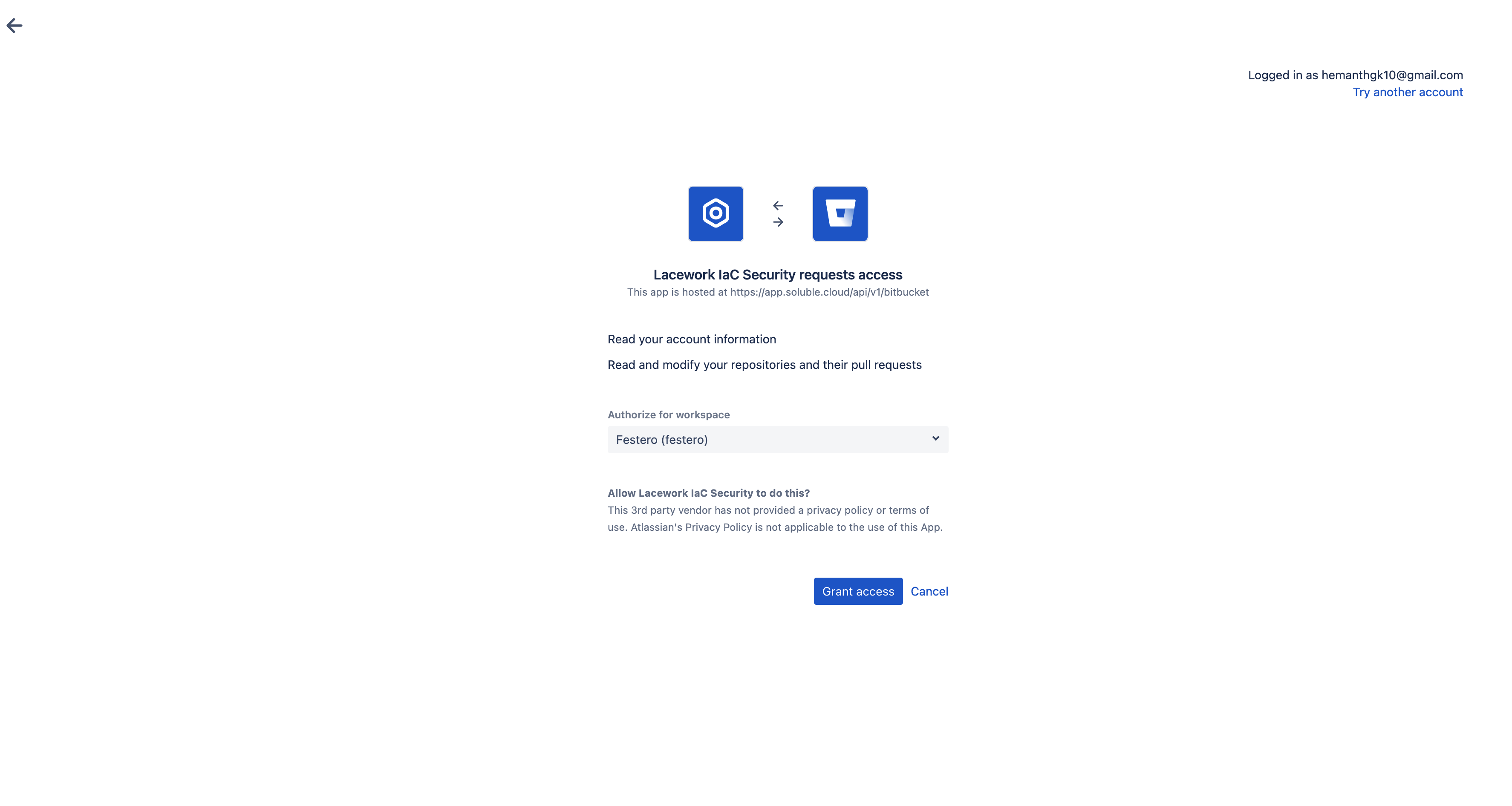
Select Bitbucket as your provider and continue.
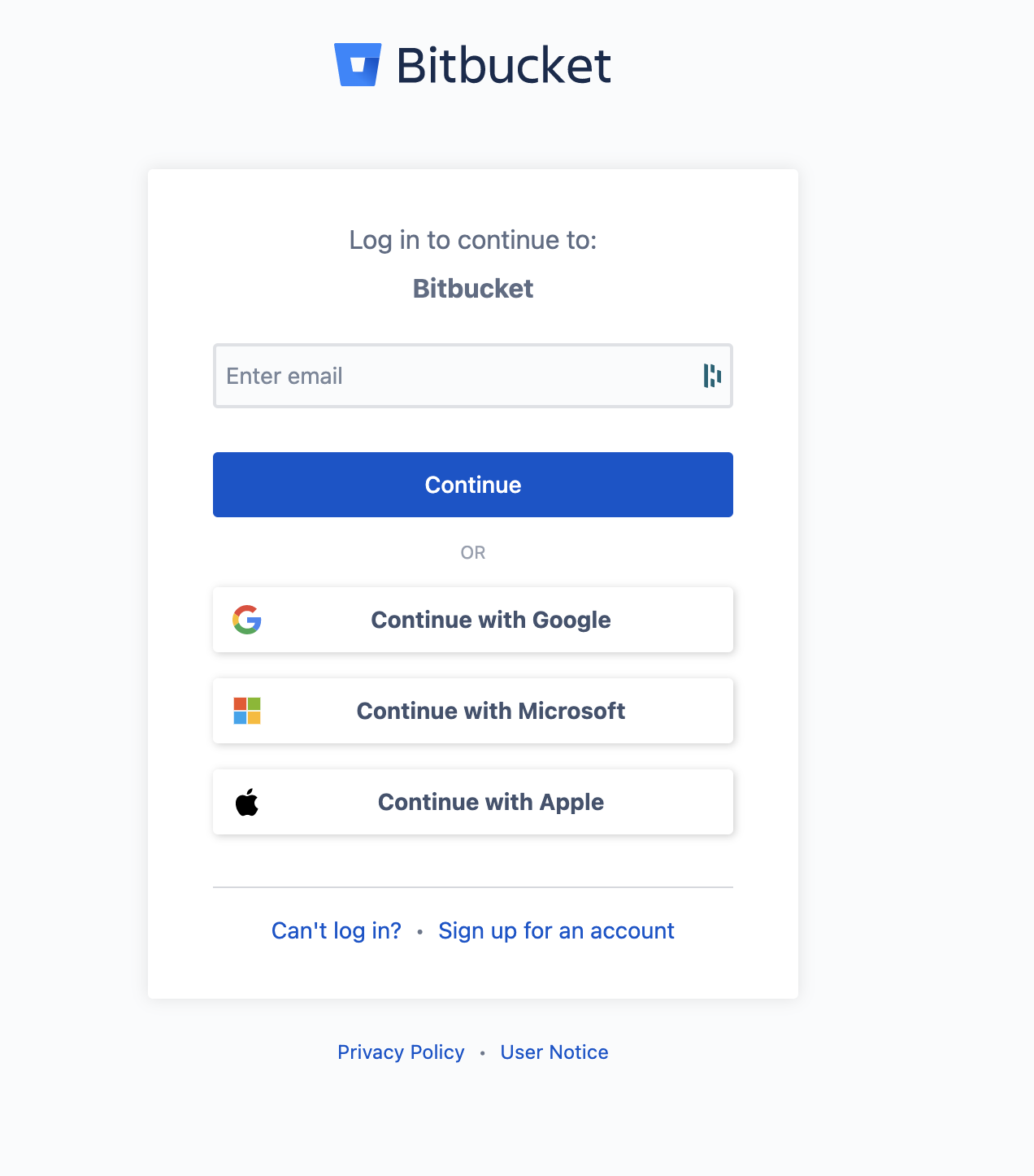
Log in to Bitbucket.
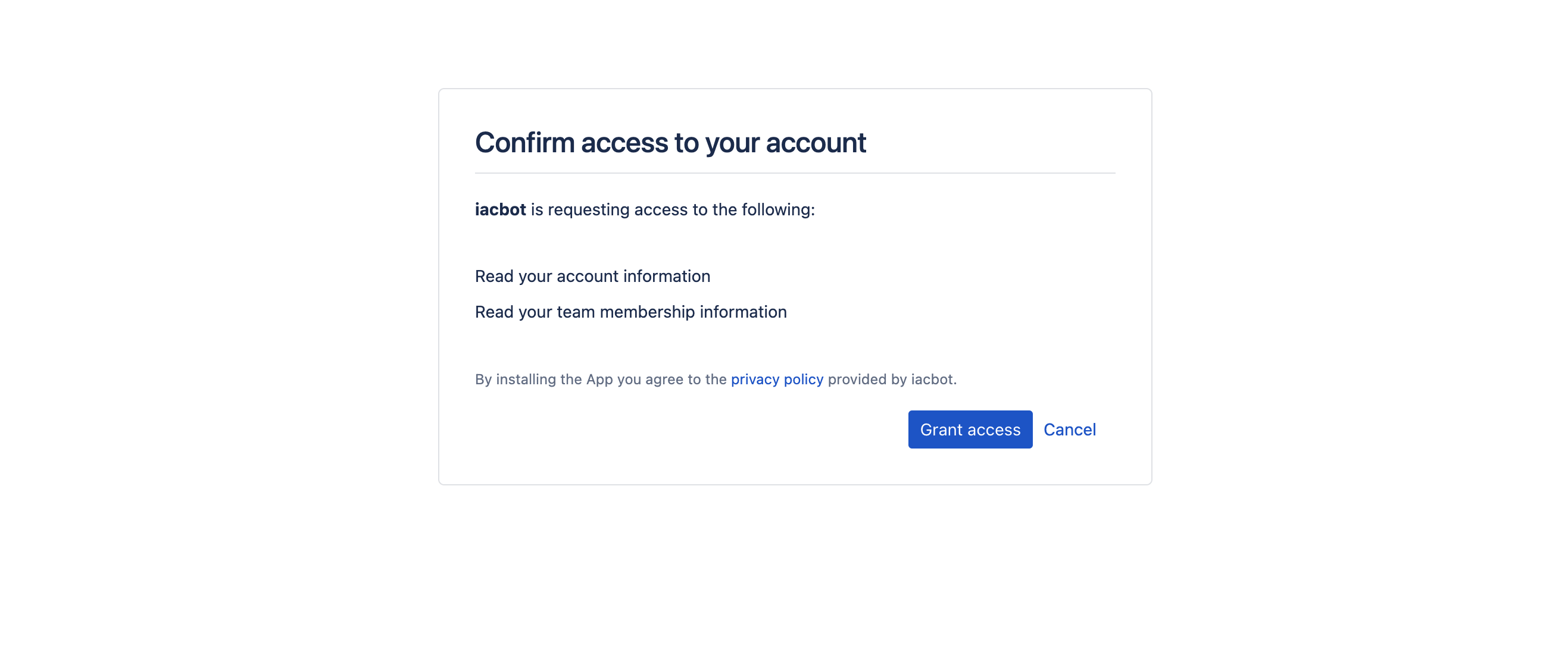
Confirm iacbot access to your Bitbucket account.
Select the workspace to install the Lacework IaC Security app.
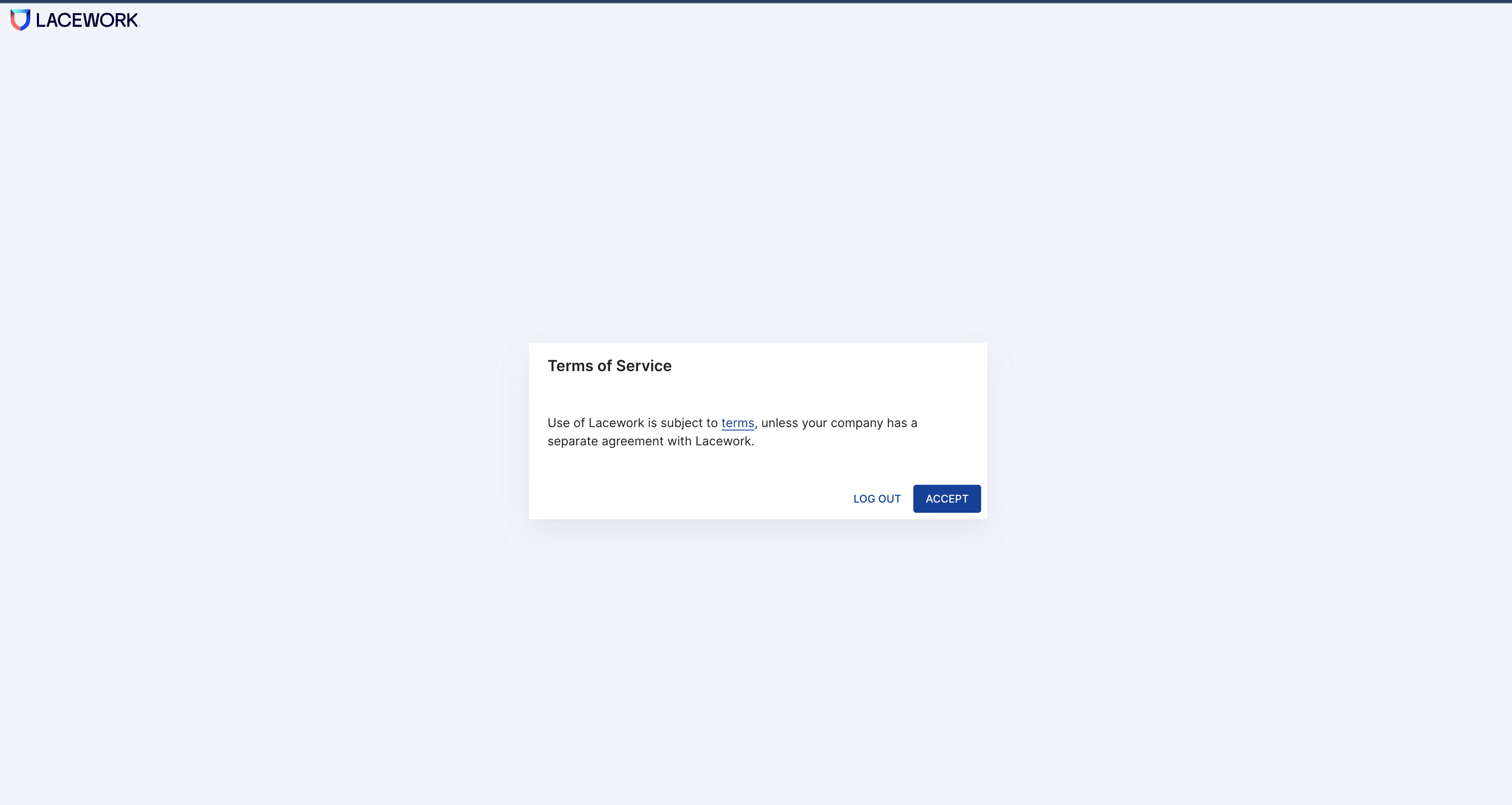
Accept the Terms of Service.
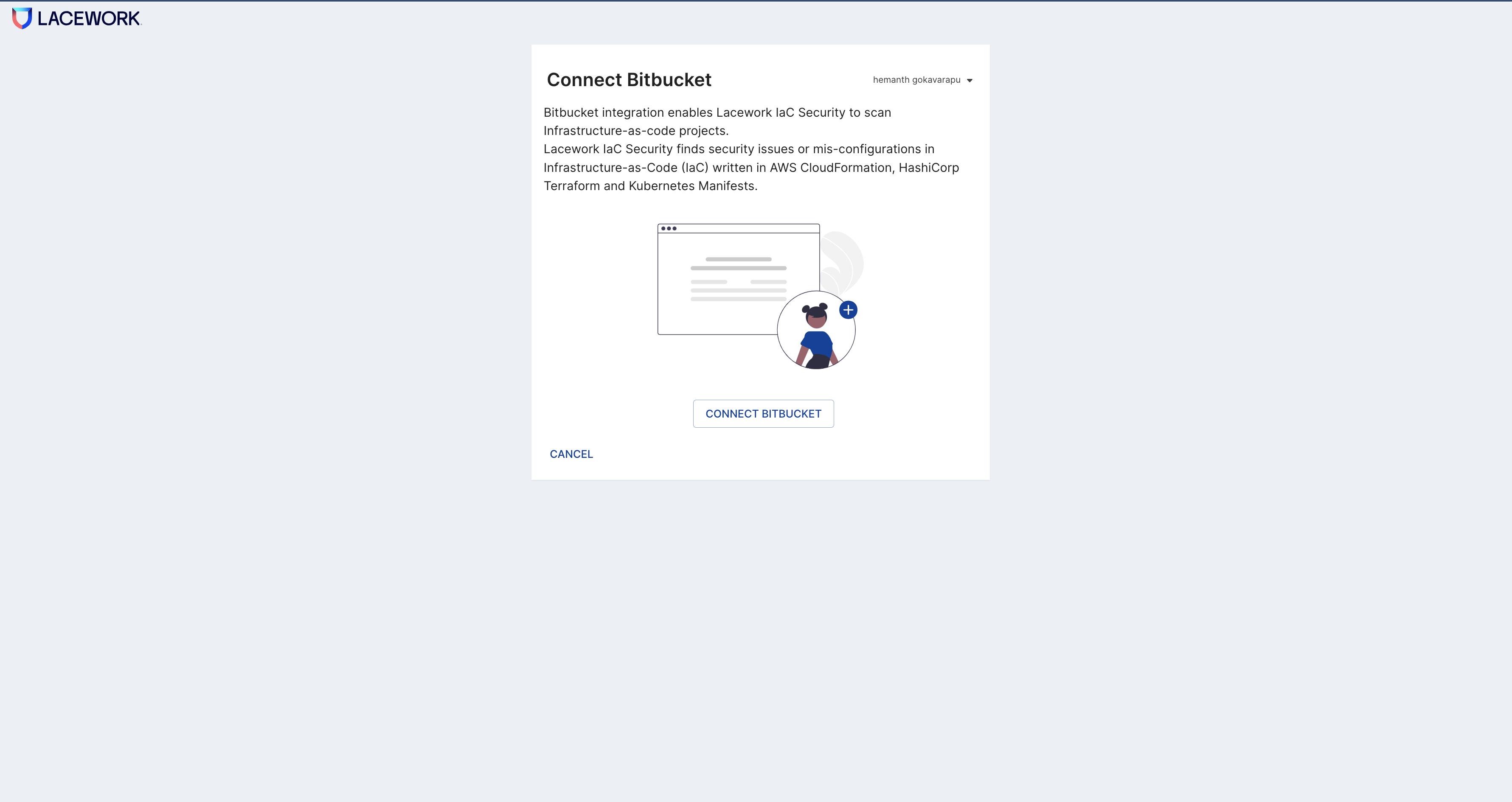
Connect your Bitbucket account with Lacework IaC.
At this point, iacbot is analyzing your repos. It looks for Terraform, CloudFormation, Kubernetes and other IaC Languages (see Language Support for details). When it finds IaC source code, it initiates a static analysis of your code.
As soon as the first assessment is complete, you should see this message: