View the Lacework Polygraph
Overview
The Lacework polygraph detects anomalies, generates appropriate alerts, and provides a tool for you to investigate and triage issues.
Use the polygraph to:
- Monitor your infrastructure.
- Spot IaaS account configurations that violate compliance.
- See security gaps and changes that could put your company at risk.
The polygraph technology dynamically develops a behavioral model of your services and infrastructure. The model understands natural hierarchies including processes, containers, pods, and machines. It then develops behavioral models that the polygraph monitors in search of activities that fall outside the model’s parameters. In addition, the polygraph continually updates its models to:
- Pinpoint exactly how a file changes.
- Investigate anomalous alerts and activities related to FIM signals.
- Provide cloud-wide capabilities for search, file type summaries, and detection of new files.
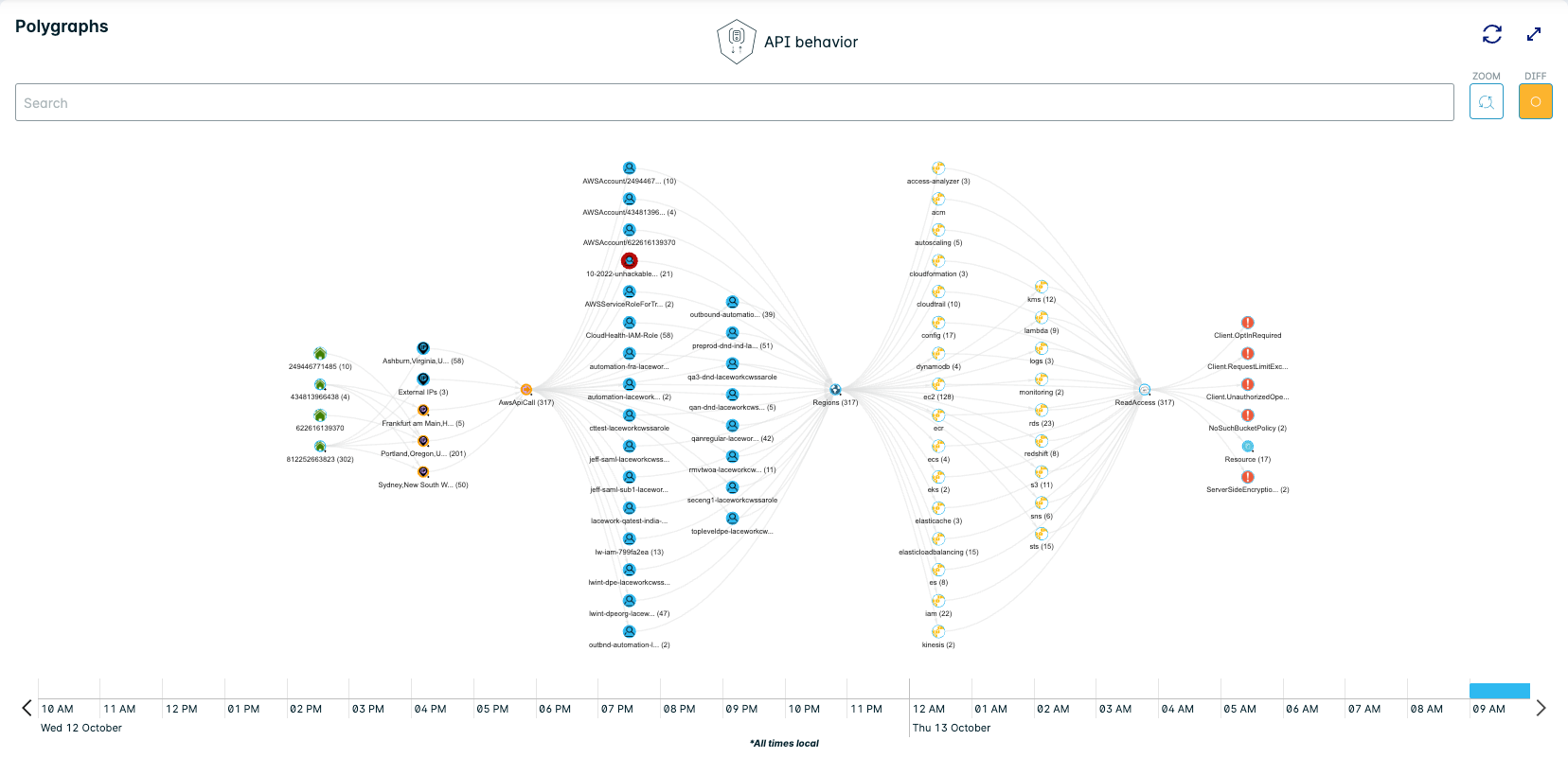
View the Polygraph of Cloud Activities
The Lacework Analyzer component consumes all cloud activities from a customer's cloud account, then filters and aggregates them before loading them into the database and the polygraph. For a complete list of AWS security alerts, see Introduction to AWS Alerts.
To view the polygraph of cloud activities, go to Resources > Cloud and select a cloud trail, such as AWS CloudTrail, Azure Activity Log, or GCP Audit Log.
Scroll down to view the Lacework polygraph.
If the number of clustered nodes is greater than 3000, then the polygraph does not appear. Instead, the following message appears:
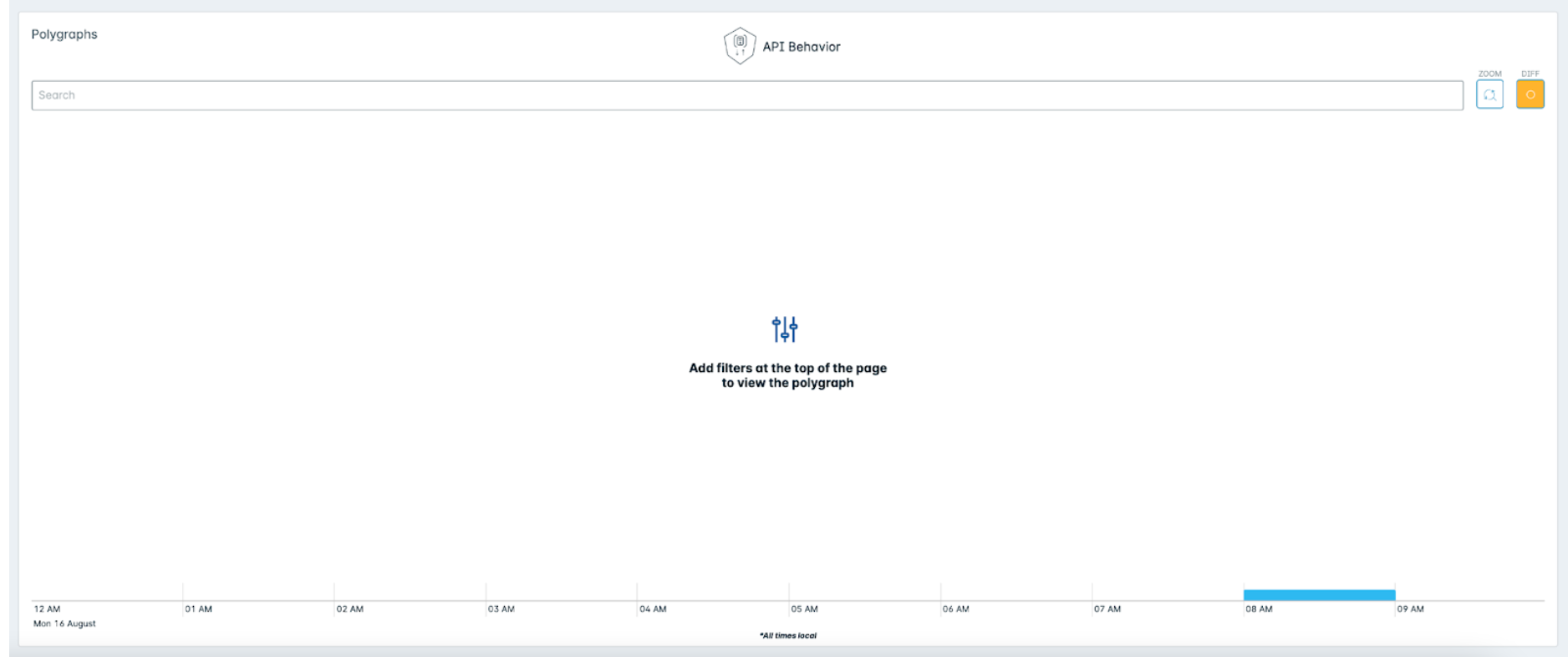
Lacework recommends using filters to refine the polygraph.
The following tabs describe in detail how to interact with the AWS CloudTrail Polygraph, Azure Activity Log Polygraph, and GCP Audit Log Polygraph:
AWS Azure GCP
You can filter the AWS CloudTrail polygraph by account ID, date/time range, or build a custom search.
Filter by Account ID
- Log in to the Lacework Console.
- Go to Resources > Cloud and click AWS CloudTrail.
- At the top of the page, click the Account drop-down to see a list of account IDs. Select the account ID you want to display or select All Accounts.
Filter by Date/Time Range
Date/time range and parameter filters are available at the top of the page.
The Date/Time (clock) icon provides preset ranges for data that you want to display:
- Latest hour
- Latest day
- Latest week
You can click the dates/times adjacent to the Date/Time icon to select the start and end date/time manually.
For example, if you select Latest hour from the Date/Time Range drop-down at 3 PM on May 05 2022, the polygraph includes activities that happen during the following date/time range: May 05, 2022, 2 PM to May 05, 2022, 3 PM.
The polygraph loads only activities found during the specified date/time range.
Note: All timestamps are in local time.Filter by Custom Search
To build a custom search:
- Log in to the Lacework Console.
- Go to Resources > Cloud, and click AWS CloudTrail.
- Click Show more to display all available filters:
- API
- Caller Account
- Event ID
- Principal ID
- Region
- Service
- Source IP
- User
- Select one of the following from the list of operators:
- matches
- does not match
- less than
- less than/equals
- greater than
- greater than/equals
- starts with
- includes
- excludes
- ends with
- Enter your keyword in the text field.
- Click Show results. Your filter becomes visible.
For example, if you select: API filter, includes operator, and enter API includes AssumeRole, it displays all API activities associated with AWS users with AssumeRole in the polygraph.
The search field is also available at the top of the page. You can build a custom search to refine the data displayed in the polygraph.
To remove a filter, click Reset.
You can filter the Azure Activity Log polygraph by tenant ID, subscription, date/time range, or build a custom search.
Filter by Tenant ID
- Log in to the Lacework Console.
- Go to Resources > Cloud, and click Azure Activity Log.
- At the top of the page, click the Tenant drop-down to view a list of tenant IDs. Select the tenant ID that you want to display or select All Tenants.
Filter by Subscription
- Log in to the Lacework Console.
- Go to Resources > Cloud, and click Azure Activity Log.
- At the top of the page, click the Subscription drop-down to view a list of subscriptions. Select the subscription that you want to display or select All Subscriptions.
Filter by Date/Time Range
Date/time range and parameter filters are available at the top of the page.
The Date/Time (clock) icon provides preset ranges for data that you want to display:
- Latest hour
- Latest day
- Latest week
You can click the dates/times adjacent to the Date/Time icon to select the start and end date/time manually.
For example, if you select Latest hour from the Date/Time Range drop-down at 3 PM on May 05 2022, the polygraph includes activities that happen during the following date/time range: May 05, 2022, 2 PM to May 05, 2022, 3 PM.
The polygraph loads only activities found during the specified date/time range.
Note: All timestamps are in local time.Filter by Custom Search
To build a custom search:
- Log in to the Lacework Console.
- Go to Resources > Cloud, and click Azure Activity Log.
- Click Show more to display all available filters:
- Caller IP
- Event Category
- Event ID
- Operation Name
- Principal ID
- Provider Name
- Subscription Name
- Tenant Name
- User
- Select one of the following from the list of operators:
- matches
- does not match
- less than
- less than/equals
- greater than
- greater than/equals
- starts with
- includes
- excludes
- ends with
- Enter your keyword in the text field.
- Click Show results. Your filter becomes visible.
For example, if you select: Caller IP filter, matches operator, and enter 54.213.133.47, it displays all API requests associated with the specified IP address in the polygraph.
The search field is also available at the top of the page. You can build a custom search to refine the data displayed in the polygraph.
To remove a filter, click Reset.
You can filter the GCP Audit Log polygraph by organization ID, project, date/time range, or build a custom search.
Filter by Organization ID
- Log in to the Lacework Console.
- Go to Resources > Cloud and click GCP Audit Log.
- At the top of the page, click the Organization drop-down to view a list of organization IDs. Select the organization ID that you want to display or select All Organizations.
Filter by Project
- Log in to the Lacework Console.
- Go to Resources > Cloud and click GCP Audit Log.
- At the top of the page, click the Project drop-down to see a list of active projects. Select the project that you want to display or select All Projects.
Filter by Date/Time Range
Date/time range and parameter filters are available at the top of the page.
The Date/Time (clock) icon provides preset ranges for data that you want to display:
- Latest hour
- Latest day
- Latest week
You can click the dates/times adjacent to the Date/Time icon to select the start and end date/time manually.
For example, if you select Latest hour from the Date/Time Range drop-down at 3 PM on May 05 2022, the polygraph includes activities that happen during the following date/time range: May 05, 2022, 2 PM to May 05, 2022, 3 PM.
The polygraph loads only activities found during the specified date/time range.
Note: All timestamps are in local time.Filter by Custom Search
To build a custom search:
- Log in to the Lacework Console.
- Go to Resources > Cloud, and click GCP Audit Log.
- Click Show more to display all available filters:
- Caller IP
- Event ID
- Method Name
- Principal Email
- Project ID
- Project Name
- Region
- Service Name
- Select one of the following from the list of operators:
- matches
- does not match
- less than
- less than/equals
- greater than
- greater than/equals
- starts with
- includes
- excludes
- ends with
- Enter your keyword in the text field.
- Click Show results. Your filter becomes visible.
For example, you select the following: Project ID filter, includes operator, and enter lw-belfast, it displays all API activities associated with the specified project to display in the polygraph.
The search field is also available at the top of the page. You can build a custom search to refine the data displayed in the polygraph.
To remove a filter, click Reset.
View the Polygraph of Host Activities
Lacework enables you to to assess, identify, and display vulnerabilities found on hosts in your environment into a polygraph.
To view the polygraph of host activities, go to Resources > Host and select a host, such as Applications, Machines, Networks, Processes, or Users. Scroll down to view the Lacework polygraph.
If the number of clustered nodes is greater than 3000, then the polygraph does not appear. Lacework recommends using filters to refine the polygraph.
The following tabs describe in detail how to interact with the Applications Polygraph, Machines Polygraph, Networks Polygraph, Processes Polygraph, and Users Polygraph:
Applications Machines Networks Processes Users
Polygraphs display all observed network activity from running applications. Lacework provides Application Communication, Application Launch, and Insider Behavior polygraphs.
They display information such as the application name, connections made to or from the application, and the number of connections. Connections include internal connections to other applications running on the host and external connections to hosts. If applications make external connections to known bad domains or IP addresses, they are flagged.
You can filter the applications polygraph by date/time range, or build a custom search.
Filter by Date/Time Range
Date/time range and parameter filters are available at the top of the page.
The Date/Time (clock) icon provides preset ranges for data that you want to display:
- Latest hour
- Latest day
- Latest week
You can click the dates/times adjacent to the Date/Time icon to select the start and end date/time manually.
For example, if you select Latest hour from the Date/Time Range drop-down at 3 PM on May 05 2022, the polygraph includes activities that happen during the following date/time range: May 05, 2022, 2 PM to May 05, 2022, 3 PM.
The polygraph loads only activities found during the specified date/time range.
Note: All timestamps are in local time.Filter by Custom Search
To build a custom search:
- Log in to the Lacework Console.
- Go to Resources > Host, and click Applications.
- Click Show more to display all available filters:
- Application
- Container
- External Hostname
- File Hash
- File Path
- Hostname
- IPV4 Address
- Instance ID
- Kubernetes Cluster
- Machines Tags
- Pod ID Address
- Pod Name
- Pod Namespace
- Pod Type
- Port
- Username
- VM Type
- Select one of the following from the list of operators:
- matches
- does not match
- less than
- less than/equals
- greater than
- greater than/equals
- starts with
- includes
- excludes
- ends with
- Enter your keyword in the text field.
- Click Show results. Your filter becomes visible.
For example, you select the following: File Path filter, matches operator, and enter /usr/lib/jvm/java-11-openjdk-amd64/bin/java. This results in all activities associated with the specified file path to display in the polygraph.
The search field is also available at the top of the page. You can build a custom search to refine the data displayed in the polygraph.
To remove a filter, click Reset.
Polygraphs display all observed machine network activity. Lacework provides Machine Communication, Machine Servers, and Machine DNS Lookup polygraphs. You can filter the Machine Communication polygraph by machine tag.
You can filter the machines polygraph by date/time range or build a custom search.
Filter by Date/Time Range
Date/time range and parameter filters are available at the top of the page.
The Date/Time (clock) icon provides preset ranges for data that you want to display:
- Latest hour
- Latest day
- Latest week
You can click the dates/times adjacent to the Date/Time icon to select the start and end date/time manually.
For example, if you select Latest hour from the Date/Time Range drop-down at 3 PM on May 05 2022, the polygraph includes activities that happen during the following date/time range: May 05, 2022, 2 PM to May 05, 2022, 3 PM.
The polygraph loads only activities found during the specified date/time range.
Note: All timestamps are in local time.Filter by Custom Search
To build a custom search:
- Log in to the Lacework Console.
- Go to Resources > Host, and click Machines.
- Click Show more to display all available filters:
- Application
- Container
- External Hostname
- File Hash
- File Path
- Hostname
- IPV4 Address
- Instance ID
- Kubernetes Cluster
- Machines Tags
- Pod ID Address
- Pod Name
- Pod Namespace
- Pod Type
- Port
- Username
- VM Type
- Select one of the following from the list of operators:
- matches
- does not match
- less than
- less than/equals
- greater than
- greater than/equals
- starts with
- includes
- excludes
- ends with
- Enter your keyword in the text field.
- Click Show results. Your filter becomes visible.
Polygraphs display network connections. Lacework provides Application Communication, Machine Communication, Machine DNS Lookup, and Insider Behavior polygraphs.
You can filter the machines polygraph by date/time range or build a custom search.
Filter by Date/Time Range
Date/time range and parameter filters are available at the top of the page.
The Date/Time (clock) icon provides preset ranges for data that you want to display:
- Latest hour
- Latest day
- Latest week
You can click the dates/times adjacent to the Date/Time icon to select the start and end date/time manually.
For example, if you select Latest hour from the Date/Time Range drop-down at 3 PM on May 05 2022, the polygraph includes activities that happen during the following date/time range: May 05, 2022, 2 PM to May 05, 2022, 3 PM.
The polygraph loads only activities found during the specified date/time range.
Note: All timestamps are in local time.Filter by Custom Search
To build a custom search:
- Log in to the Lacework Console.
- Go to Resources > Host, and click Networks.
- Click Show more to display all available filters:
- Application
- Container
- External Hostname
- File Hash
- File Path
- Hostname
- IPV4 Address
- Instance ID
- Kubernetes Cluster
- Machines Tags
- Pod ID Address
- Pod Name
- Pod Namespace
- Pod Type
- Port
- Username
- VM Type
- Select one of the following from the list of operators:
- matches
- does not match
- less than
- less than/equals
- greater than
- greater than/equals
- starts with
- includes
- excludes
- ends with
- Enter your keyword in the text field.
- Click Show results. Your filter becomes visible.
Polygraphs display all observed network activity from running applications. Lacework provides Application Communication, Application Launch, and Insider Behavior polygraphs.
The polygraphs display any connections made to or from an application and the number of connections. It also provides internal connections to other applications running on the host and external connections to hosts. If any external connections are made to known bad domains/IP addresses, they are flagged.
You can filter the machines polygraph by date/time range or build a custom search.
Filter by Date/Time Range
Date/time range and parameter filters are available at the top of the page.
The Date/Time (clock) icon provides preset ranges for data that you want to display:
- Latest hour
- Latest day
- Latest week
You can click the dates/times adjacent to the Date/Time icon to select the start and end date/time manually.
For example, if you select Latest hour from the Date/Time Range drop-down at 3 PM on May 05 2022, the polygraph includes activities that happen during the following date/time range: May 05, 2022, 2 PM to May 05, 2022, 3 PM.
The polygraph loads only activities found during the specified date/time range.
Note: All timestamps are in local time.Filter by Custom Search
To build a custom search:
- Log in to the Lacework Console.
- Go to Resources > Host, and click Processes.
- Click Show more to display all available filters:
- Application
- Container
- External Hostname
- File Hash
- File Path
- Hostname
- IPV4 Address
- Instance ID
- Kubernetes Cluster
- Machines Tags
- Pod ID Address
- Pod Name
- Pod Namespace
- Pod Type
- Port
- Username
- VM Type
- Select one of the following from the list of operators:
- matches
- does not match
- less than
- less than/equals
- greater than
- greater than/equals
- starts with
- includes
- excludes
- ends with
- Enter your keyword in the text field.
- Click Show results. Your filter becomes visible.
You can filter the machines polygraph by date/time range or build a custom search.
Filter by Date/Time Range
Date/time range and parameter filters are available at the top of the page.
The Date/Time (clock) icon provides preset ranges for data that you want to display:
- Latest hour
- Latest day
- Latest week
You can click the dates/times adjacent to the Date/Time icon to select the start and end date/time manually.
For example, if you select Latest hour from the Date/Time Range drop-down at 3 PM on May 05 2022, the polygraph includes activities that happen during the following date/time range: May 05, 2022, 2 PM to May 05, 2022, 3 PM.
The polygraph loads only activities found during the specified date/time range.
Note: All timestamps are in local time.Filter by Custom Search
To build a custom search:
- Log in to the Lacework Console.
- Go to Resources > Host, and click Users.
- Click Show more to display all available filters:
- Application
- Container
- External Hostname
- File Hash
- File Path
- Hostname
- IPV4 Address
- Instance ID
- Kubernetes Cluster
- Machines Tags
- Pod ID Address
- Pod Name
- Pod Namespace
- Pod Type
- Port
- Username
- VM Type
- Select one of the following from the list of operators:
- matches
- does not match
- less than
- less than/equals
- greater than
- greater than/equals
- starts with
- includes
- excludes
- ends with
- Enter your keyword in the text field.
- Click Show results. Your filter becomes visible.
View the Polygraph of Containers Activities
Lacework enables you to assess, identify, and display vulnerabilities found in the operating system software packages in container images into a polygraph.
To view the polygraph of containers activities, go to Resources > Containers.
If the number of clustered nodes is greater than 3000, then the polygraph does not appear. Lacework recommends that you use filters to refine the polygraph.
Filter by Date/Time Range Filter by Custom Search
Date/time range and parameter filters are available at the top of the page.
The Date/Time (clock) icon provides preset ranges for data that you want to display:
- Latest hour
- Latest day
- Latest week
You can click the dates/times adjacent to the Date/Time icon to select the start and end date/time manually.
For example, if you select Latest hour from the Date/Time Range drop-down at 3 PM on May 05 2022, the polygraph includes activities that happen during the following date/time range: May 05, 2022, 2 PM to May 05, 2022, 3 PM.
The polygraph loads only activities found during the specified date/time range.
Note: All timestamps are in local time.To build a custom search:
- Log in to the Lacework Console.
- Go to Resources > Containers.
- Click Show more to display all available filters:
- Application
- Container
- External Hostname
- File Hash
- File Path
- Hostname
- IPV4 Address
- Instance ID
- Kubernetes Cluster
- Machines Tags
- Pod ID Address
- Pod Name
- Pod Namespace
- Pod Type
- Port
- Username
- VM Type
- Select one of the following from the list of operators:
- matches
- does not match
- less than
- less than/equals
- greater than
- greater than/equals
- starts with
- includes
- excludes
- ends with
- Enter your keyword in the text field.
- Click Show results. Your filter becomes visible.
View the Polygraph of Kubernetes Activities
To view the polygraph of multiple namespaces and clusters, go to Resources > Kubernetes.
The polygraph can display the following behaviors:
- API
- Activity
- Node Network
- Pod Network
Each behavior presents a different set of filters that you can use to display the polygraph. Click a filter to view the data in a tabular format.
If the number of clustered nodes is greater than 3000, then the polygraph does not appear. You can use the following methods to refine the polygraph:
Use filters to display a subset of activities associated with specific clusters or namespaces. Click the filters at the top of the page to display only the desired clusters or namespaces.
Use the search function to display a subset of specific activities. Click the search field to view a list of field names that you can use to build your search.
Use the time filter to display a subset of specific activities based on when they occurred.
Filter by Kubernetes Cluster Filter by Namespace Filter Date/Time Range Filter by Custom Search
- Log in to the Lacework Console.
- Go to Resources > Kubernetes.
- Click Kubernetes Cluster to display the list of filters. From the Kubernetes Cluster drop-down, select the clusters that you want to display. The selected filters on the top of the page are highlighted.
- Log in to the Lacework Console.
- Go to Resources > Kubernetes.
- Click Namespace to display the list of filters. Select the namespaces you want to display from the Namespace drop-down. The selected filters on the top of the page are highlighted.
Date/time range and parameter filters are available at the top of the page.
The Date Range (calendar) icon provides preset ranges for data that you want to display:
- Latest day
- Latest three days
- Latest week
- Latest month
You can click the dates/times adjacent to the Date Range icon to select the start and end date/time manually.
For example, if you select Latest three days from the Date Range drop-down at 3 PM on May 05 2022, the polygraph includes Kubernetes activities that happen during the following date/time range: May 02, 2022, 3 PM to May 05, 2022, 3 PM.
It reports only activities found during the specified date range.
Note:s All timestamps are in local time.The search field is available at the top of the page. You can build a custom search to refine the polygraph.
To build a custom search:
- Log in to the Lacework Console.
- Go to Resources > Kubernetes.
- Click the search field for a list of field names
- Pod IP Address
- Pod Name
- Pod Type
- VM Type
- Select one of the following from the list of operators:
- =
- includes
- excludes
- starts with
- ends with
- !=
- Enter your keyword to the adjacent of the selected operator.
- Select the Enter key to submit. Your filter is highlighted.
For example, if you select the following: Pod Type filter, matches operator, and enter alert-evidence-mgr, it displays all activities associated with the specified pod type in the polygraph.
Click Reset to remove all filters.