S3 Data Export
Beta Feature
This topic describes functionality that is currently in beta.
S3 data export lets you export data collected from your Lacework account and send it to an S3 bucket of your choice. You can extend Lacework processed/normalized data to report/visualize alone or combine with other business/security data to get insights and make meaningful business decisions.
note
You can use Amazon S3 buckets only for data export purposes and not as an alert channel.
Every hour, Lacework collects data from your Lacework account and sends it to an internal Lacework S3 bucket as a staging location. The data remains in the internal Lacework S3 bucket until its hourly scheduled export to your designated S3 bucket.
For detailed information about the data exported by Lacework, see Lacework Data Share.
Lacework offers the following methods to add an S3 alert channel:
Summary of Steps
- In AWS, create a bucket to receive the data exported from Lacework.
- If using Amazon server-side encryption, read Lacework S3 Export and Amazon Server-Side Encryption.
- In the Lacework Console, create an S3 alert channel, which Lacework uses to send the data to your designated bucket in AWS.
- In the Lacework Console, create a data export rule, which defines the specific data to export from Lacework.
Create an Amazon S3 Alert Channel in Lacework
Navigate to Amazon S3
- Log in to the Lacework Console as a Lacework user that has administrative privileges.
- Navigate to Settings > Notifications > Alert channels.
- Click + Add New.
- Select Amazon S3.
- Click Next.
- Follow the steps in the next section.
Create an Amazon S3 Alert Channel
First, ensure that the bucket that will receive the data from Lacework already exists in AWS. Creating the S3 alert channel lets Lacework use it to send data to your designated bucket in AWS.
During alert channel creation, Lacework creates an IAM role with the least privileges. To grant Lacework permission to create this role, you must log in to your AWS account as a user with administrator credentials [arn:aws:iam::aws:policy/AdministratorAccess]. You cannot complete alert channel creation without the required credentials.
Complete the following steps:
- Name the alert channel.
If you use the CloudFormation template, this name will be replaced by the stack name. - Select CloudFormation.
- Continue the configuration process using the corresponding option’s steps.
If you use the CloudFormation template, you can either run or download the CloudFormation template. The download option is helpful if you need to distribute the template to different account owners.
Use the CloudFormation Template
Option 1: Run CloudFormation Template - This option requires fewer steps and less user interaction. For this option, disable your browser pop-up blocker.
- Click Run CloudFormation Template.
You are redirected to the AWS Create stack > Select Template page. The Lacework script populates the Specify an Amazon S3 template URL for you. - After reviewing the page, click Next.
- To continue configuration, follow the steps in Create Stack - Specify Details.
Option 2: Download CloudFormation Template - This option requires more user interaction, but may be useful if you have multiple accounts with distributed ownership.
- Click Download CloudFormation Template to download the template locally.
- Log in to your AWS account.
- Select the CloudFormation service and click Create New Stack, which displays the Create stack > Select Template page.
- Upload the Lacework template and click Next.
For more information on Selecting a Stack Template, refer to the AWS documentation library. - To continue your configuration, use the following steps in Create Stack - Specify Details.
Create Stack - Specify Details
- Specify details on the Create Stack - Specify Details page:
- Create a Stack name [for example, Lacework-S3-AlertChannel].
The name must be unique within the region. This stack name replaces the alert channel name you provided earlier. - Resource name prefix, is populated with the account name of the first account configured to use Lacework for AWS Config if the direct configuration method was chosen. You can keep this prefix or enter a different prefix to ensure account uniqueness. If you chose to upload the template during initial installation, Resource name prefix will be empty. Enter a prefix such as an account name.
- ExternalID is populated by Lacework. It is not editable when you use the Run CloudFormation Template option.
- S3 Bucket ARN is the ARN of a preexisting S3 bucket for data export, for example, arn:aws:s3:::lacework-data-export. The S3 bucket is not created by CloudFormation.
- Click Next.
- Create a Stack name [for example, Lacework-S3-AlertChannel].
- No changes are required on the Create stack - Options page. Click Next.
- On the Create stack - Review page, complete the following steps:
- Select I acknowledge that AWS CloudFormation might create IAM resources with custom names.
- Click Create.
You are redirected back to the CloudFormation page. If you do not see your new stack in the table, refresh the page. Select your stack to see the event log as it is being created. When the stack is CREATE-COMPLETE, the S3 alert channel creation is complete.
Create an Amazon S3 Alert Channel Manually
Before proceeding, ensure that the bucket that will receive the data from Lacework already exists in AWS.
During alert channel creation, Lacework creates an IAM role with the least privileges. To grant Lacework permission to create this role, you must log in to your AWS account as a user with administrator credentials [arn:aws:iam::aws:policy/AdministratorAccess]. You cannot complete alert channel creation without the required credentials.
Creating the S3 alert channel lets Lacework use it to send data to your designated bucket in AWS.
- Select Amazon S3.
- Select Manual Configuration.
- Name the alert channel.
- Provide the External ID.
- Provide the Role ARN.
- Provide the Bucket ARN.
Create a Data Export Rule in Lacework
To create a data export rule in Lacework, follow these steps:
- Navigate to Settings > Configuration > Data export rules.
- Click + Add New.
- Name the rule and optionally provide a description.
- Select the alert channels to use.
- Select the Data Export Profile Version.
For detailed information about the data exported by Lacework, see Lacework Data Share. - Click Save.
After creating a data export rule, S3 data export configuration is complete and Lacework starts to export data to your S3 bucket hourly.
Lacework S3 Export and Amazon Server-Side Encryption
Lacework S3 export supports Amazon server-side encryption (SSE), but additional steps might be required depending on the bucket’s SSE configuration.
Buckets configured with Server-Side Encryption with Amazon S3-Managed Keys (SSE-S3) work transparently with Lacework S3 export and don’t require changes to the S3 bucket or policies.
Buckets configured with Server-Side Encryption KMS keys, such as the Server-Side Encryption with Customer Master Keys (CMKs) Stored in AWS Key Management Service (SSE-KMS), illustrated in the following figure, are supported, but you must complete the following additional steps in AWS to allow Lacework S3 exports.
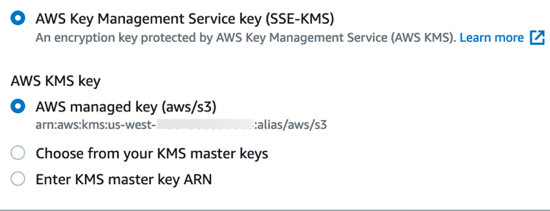
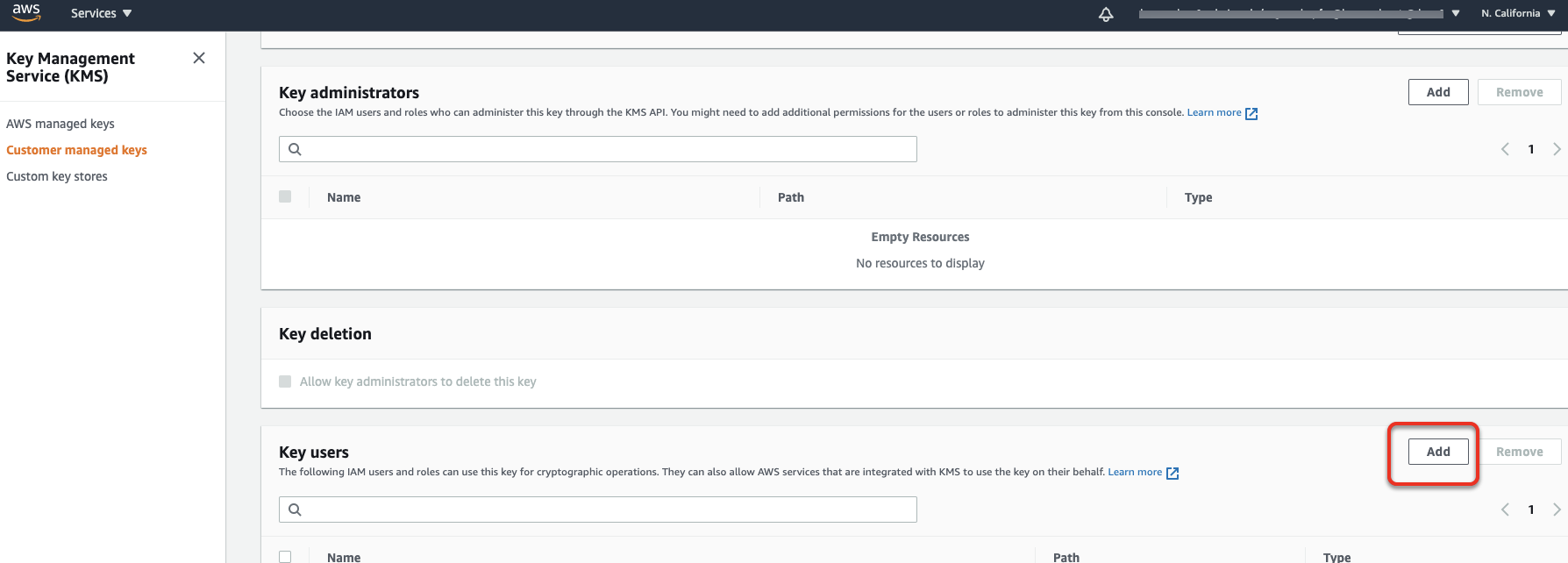
- Go to Key Management Service.
- Go to Customer Managed keys.
- Add the Lacework role to the key users.
Create an Amazon S3 Data Export Using Terraform
S3 data export lets you export data collected from your Lacework account and send it to an S3 bucket of your choice. You can extend Lacework processed/normalized data to report/visualize alone or combine with other business/security data to get insights and make meaningful business decisions.
Every hour, Lacework collects data from your Lacework account and sends it to an internal Lacework S3 bucket as a staging location. The data remains in the internal Lacework S3 bucket until its hourly scheduled export to your designated S3 bucket.
For detailed information about the data exported by Lacework, see Lacework Data Share.
resource "lacework_alert_channel_aws_s3" "data_export" {
name = "s3 Alerts"
bucket_arn = "arn:aws:s3:::bucket_name/key_name"
credentials {
role_arn = "arn:aws:iam::1234567890:role/lacework_iam_example_role"
external_id = "12345"
}
}
Additional information on the lacework_alert_channel_aws_s3 resource can be found on the Terraform Registry.