Lacework Overview
Lacework delivers end-to-end visibility into what’s happening across your cloud environment, including detecting threats, vulnerabilities, misconfigurations, and unusual activity, so you can innovate with speed and safety. The Polygraph Data Platform automatically learns how your environment is supposed to run, and tells you when it deviates.
The Polygraph Data Platform
The Polygraph Data Platform helps you understand what’s happening across your cloud environments and helps you uncover risk — from finding misconfigurations to prioritizing vulnerabilities based on runtime data — to help you prove compliance faster, without the overhead. Lacework continuously monitors for vulnerabilities and noncompliance in your cloud accounts and workloads using behavior-based threat detection.
Our patented Polygraph technology automatically builds a baseline of how your unique environment operates. It uncovers the relationships between resources, services, users, and network activity, and uses behavioral analytics to detect abnormal activity. With the cloud, new events happen all the time, but Lacework technology recognizes those patterns automatically and uncovers meaningful new behaviors that you should pay attention to most. Lacework identifies unknowns because the platform looks at changes in behavior at scale, based on learning your unique cloud.
Lacework alerts based on the criticality of changes, and shows browsable graphs of all the connections in order to make investigations easier. Lacework automatically makes correlations across your environment that would have taken hours, days, or longer to uncover and piece together.
For any event, Lacework tells you who, what, when, where, and why and provide a visualization to show you exactly what happened; eliminating the manual queries and intensive research typically needed.
How it Works
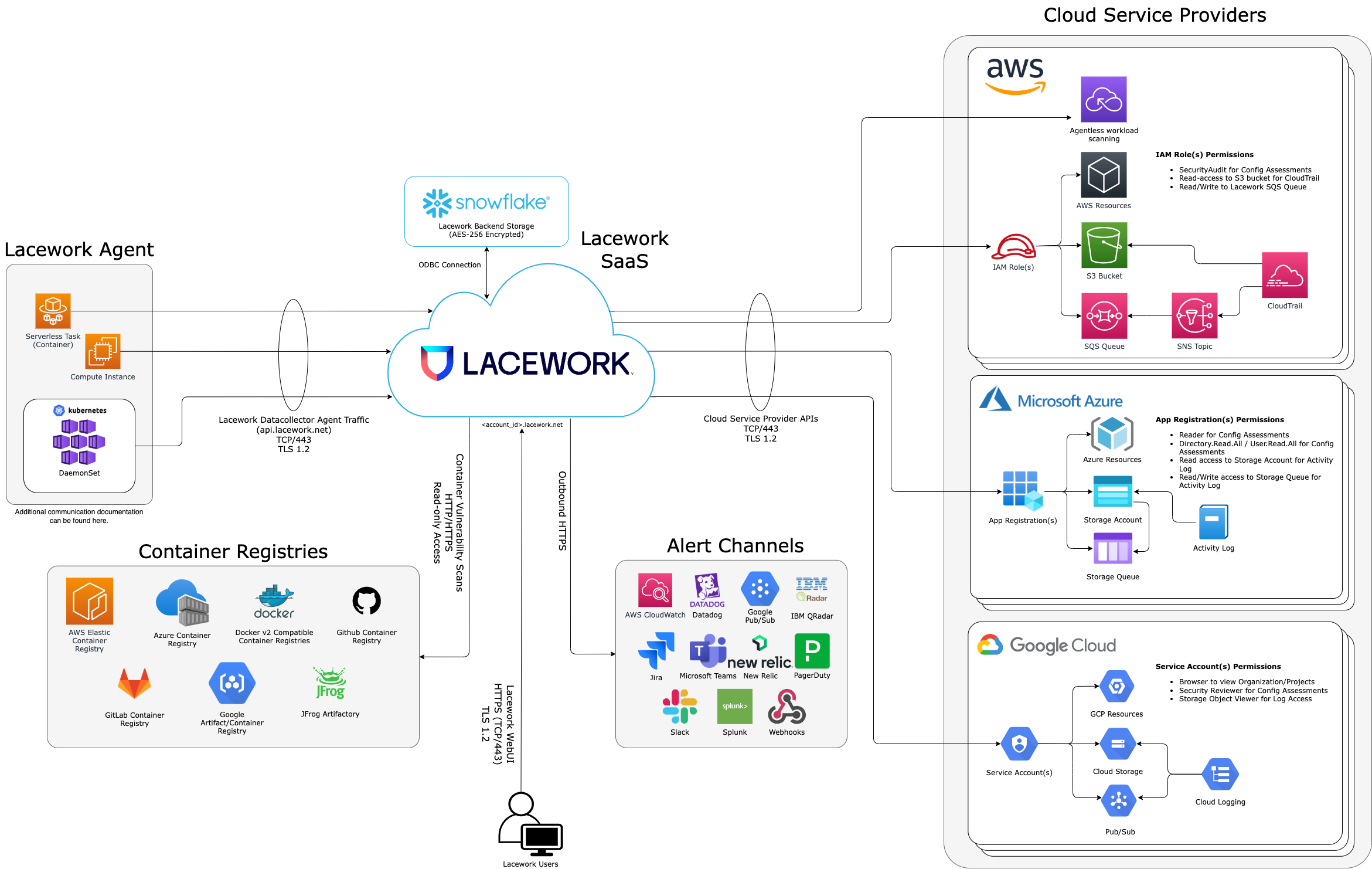
Lacework continuously ingests configuration and activity data from your cloud environment with or without agents. Lacework collects data at the host, container, and process-level and tracks interactions between users, resources, and cloud services to help you better understand what's happening in your environment and the behaviors that put your environment at risk. This data includes API calls, user activity, application launches, configurations, and more.
Lacework automatically checks for misconfigurations and vulnerabilities by modeling resources and interactions at a functional level, such as applications, processes, and privilege changes based on deviations from your baseline. It creates the baseline based on Polygraph technology that uses cloud behavioral analytics to create detailed models of how your cloud operates. The Platform automatically learns and tunes itself based on your unique environment. Within one hour, it creates a baseline of normal cloud activity.
Lacework detects behaviors to find unknown threats through a patented form of behavioral analytics to detect new activities and changes. Lacework finds threats that are difficult to detect by continuously monitoring for deviations in user and cloud resource behavior in your unique environment. By automatically learning how your environment operates and finding anomalous behavior, you can find potential exploits before an attack or vulnerability is known, widely publicized, or patched. Lacework also incorporates details from the Lacework Labs threat research team, threat feeds (known bad IPs/domains/file hashes, etc.), vulnerability feeds, and standard and/or custom policies you can edit or create if there’s something specific in your environment that shouldn’t happen or you want to be alerted about. Additionally, Lacework correlates data about vulnerabilities and what is actively happening during runtime so you can understand risk and prioritize action.
Lacework compiles all of this data and delivers contextual alerts, browsable graphs to visualize your cloud activity, and provides remediation guidance for misconfigurations and vulnerabilities.
Workload and Container Security
Lacework provides visibility into risks across cloud environments. It deploys in minutes, with or without agents, to your cloud accounts (AWS, Azure, Google Cloud (GCP)), and shows what you have deployed, how it’s configured, and if any vulnerabilities or misconfigurations exist. You can also scan workloads for vulnerabilities and secrets without agents, giving instant coverage of production environments. This includes scanning container images, hosts, and language libraries.
Lacework correlates all of this data to show what combinations of risk factors and vulnerable resources could lead to potential attack paths. By combining risk factors like vulnerabilities, network reachability, secrets, and identity and access management (IAM) roles, you can better prioritize which issues to address first to reduce risk, see a visualization to aid in investigations, and leverage remediation guidance.
Lacework monitors what is actually happening in your cloud accounts and services, including Kubernetes. This is how Lacework can see if you’ve been compromised through any of those critical risks and help you understand the blast radius if you were. The Polygraph technology continuously learns what behaviors are normal and when there are meaningful changes to help you uncover account compromise or other malicious activity. Lacework provides context to help you quickly understand what happened, why, and how through cloud audit log analysis and by pre-filtering and analyzing the logs.
Lacework uses such data to alert you of anomalous behavior with detailed context based on your cloud environment's baseline and your custom and standard policies.