Lacework for Azure FAQ
Compliance
How do I start using the Azure CIS benchmarks in the Compliance Reports?
See Azure Assessments for instructions on how to enable the latest available benchmarks for your Azure environment.
Why do some benchmark rules show a 'Manual' status in the Compliance Reports?
Lacework automates your Compliance rules where it is possible to do so, but some rules cannot be automated. The reasons for this can vary:
- Scope is defined by the user.
- It requires configuring other products or API permissions that are out of scope through the Azure integration with Lacework.
- Known issues for audit procedure described by CIS control rule.
There are certain rules that require manual intervention even when the Center for Internet Security (CIS) deemed them as automated. Conversely, Lacework has automated some rules that were deemed manual.
See the Automated vs Manual Rules sections in Azure Assessments for further details on affected rules.
Why do some Compliance rules display at the Tenant level but not at the Subscription level?
The majority of the Azure CIS benchmark rules are evaluated at the Subscription level, however, some are evaluated at the Tenant level.
A small subset of rules are also applicable at the Tenant and Subscription levels.
Why do some Compliance Tenant level IAM rules take longer to update?
Some Identity and Access Management rules can take up to 48 hours before they initially show in the Lacework Console. This is because they leverage the Azure Security Benchmark Policy, which runs once every 24 hours.
Why do some Compliance Tenant level IAM rules still not show after 48 hours?
Some Identity and Access Management policies are only initialized if the Azure Security Center free has been enabled in your environment.
After setting this up, the rules are only available if you have skipped the free trial.
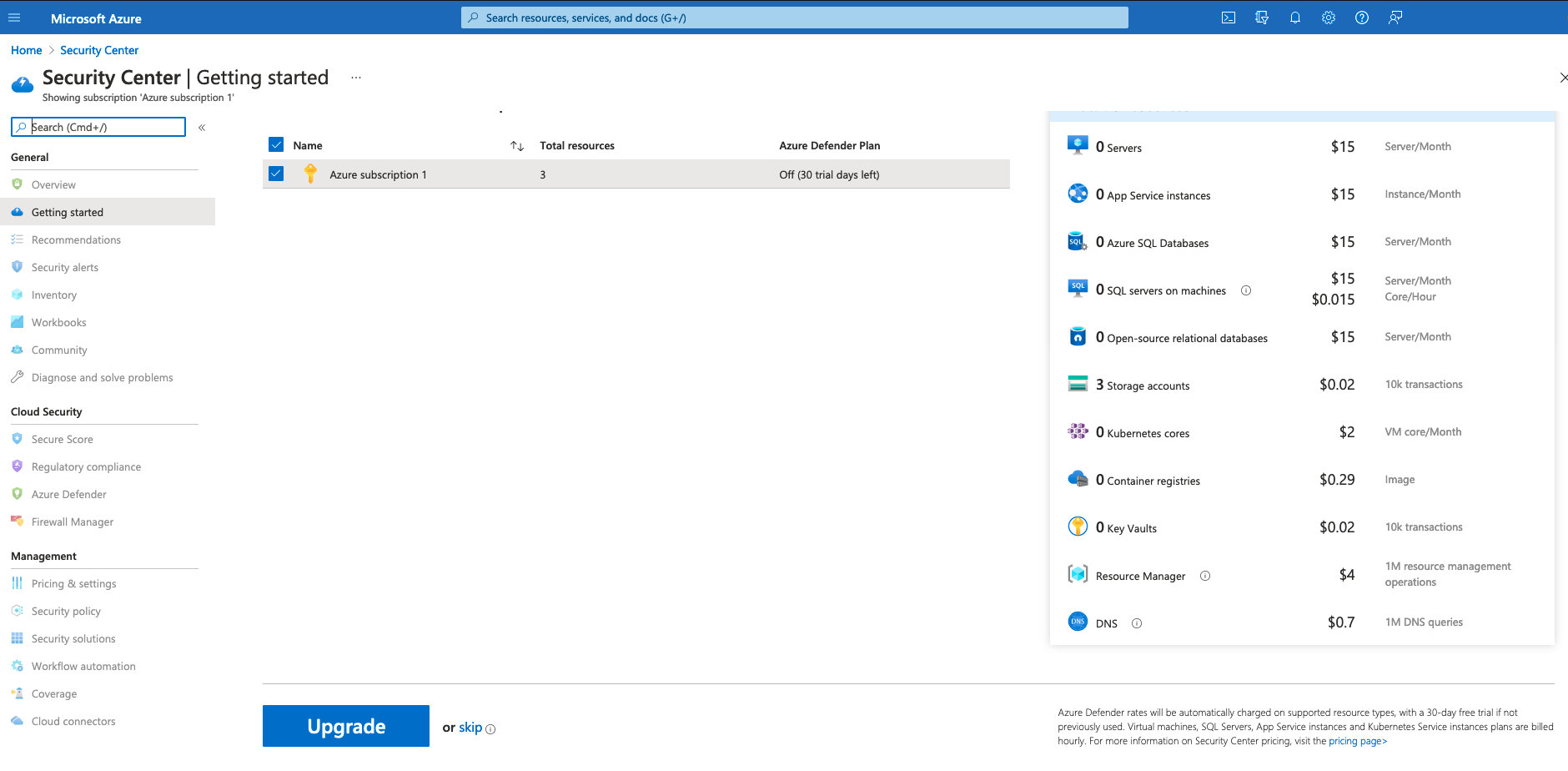
The rules are also available if you have started paying for Azure Defender.
Are Azure Key Vault permissions required for an Azure Configuration integration?
Azure Key Vault permissions are required to be able to assess some compliance policies in your environment. Not having the appropriate permissions can result in "Could Not Assess" errors on enabled policies that require Key Vault access.
See Assign Azure Key Vault permissions for the necessary steps.